In this article, we will explore how Mitigation Controls in SAP® GRC help manage risks across the GRC ecosystem. This article focuses on the Access Control and Process Control modules, comparing their key functions and how they impact security and compliance within organizations.
SAP® GRC
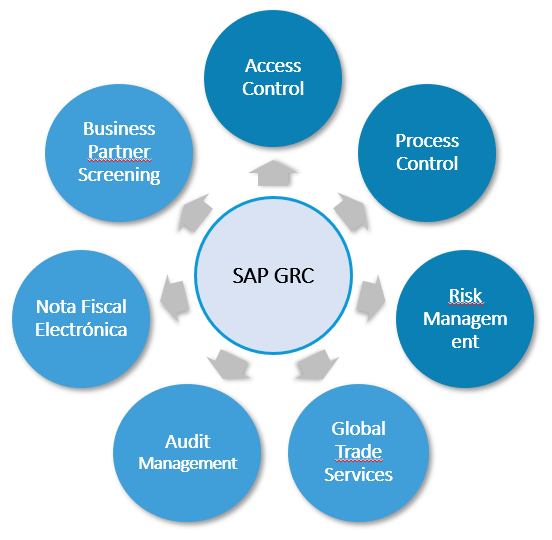
SAP® GRC is a solution provided by SAP® that helps organizations reduce risks, provide decision-making information, and increase efficiency through automation:
The SAP® GRC area includes different modules, and here we will focus on the most important ones:
When it comes to mitigation controls, they can be maintained within two different modules: Access Control and Process Control. However, the maintenance of Mitigation Controls is different in each of them.
SAP® GRC Access Control
This module focuses on the technical area of User and Role Management. In summary, the tools provided by the Access Control module are:
- Access Risk Analysis (ARA), which helps define and control access risks within a system.
- Access Request Management (ARM), which helps define and execute the user provisioning process in a system.
- Emergency Access Management (EAM), which helps define and execute the Emergency Access Provisioning process in an SAP® system.
- Business Role Management (BRM), which helps define and execute the role management process in an SAP® system.
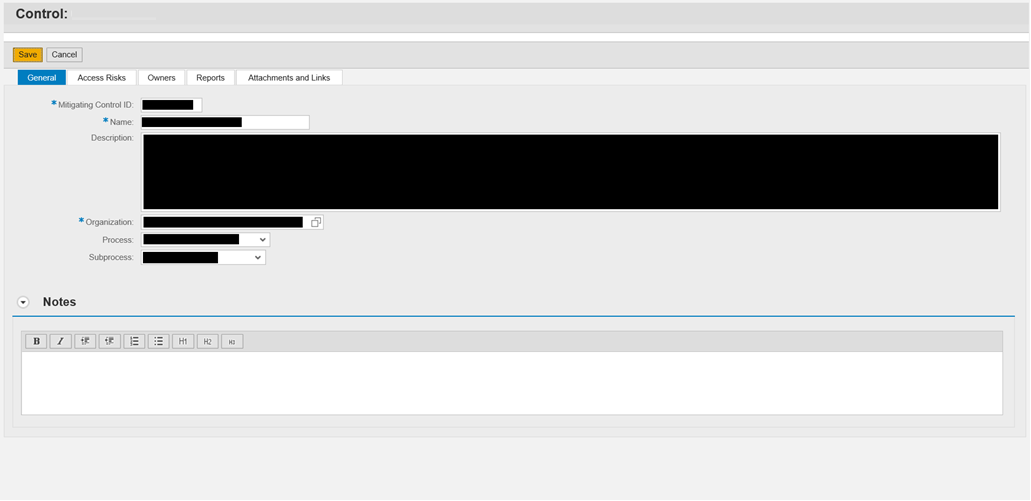
The first module, Access Risk Analysis (ARA), is the one that manages the definition and use of Mitigation Controls. Below, you will find a screenshot showing the different fields required for the creation of a Mitigation Control:
- Mitigating Control ID: the ID that will identify the Mitigation Control being created.
- Name: a brief description included within the mitigation control.
- Description: a long description that provides all the information about the Mitigation Control.
- Organization: the scope in which the mitigating control is applicable.
- Process: the business process to which the mitigation control belongs.
- Subprocess: the subprocess to which the Mitigation Control belongs.
Apart from the first tab (“General”), the Mitigation Control has 4 more tabs:
- Access Risk: This is where the Access Risks to which this Mitigation Control applies are set.
- Owners: Here, an Owner must be included for the Mitigation Control, who will be responsible for its periodic review.
- Reports: Documentation tab.
- Attachments and Links: Here, documents with more information about the mitigation control can be uploaded (or referenced to a specific site).
Once we understand what information is included as part of the Mitigation Control definition, it is important to know what can be done with this within the SAP® GRC Access Control module.
Mitigation controls are mainly used within the ARA, ARM, and BRM modules. Let’s see what can be done in each of them.
Access Risk Analysis (ARA)
Mitigation Controls can be assigned to a specific user or role, and this will mitigate the risk. It is important to understand that each Mitigating Control will only be applicable when the Risks selected within the Master Data appear. A risk cannot be mitigated if no Mitigation Control is linked to it. Once we mitigate the User/Role, they will be excluded from the Risk Analysis (only for the Risks to which you assigned a Mitigating Control; if no Risk is mitigated, the User/Role will continue to appear for that Risk).
Access Request Management (ARM)
When executing the User Provisioning process, a Mitigation Control can be assigned to a User before the actual assignment within the system. This will help identify the Risks that were reviewed and approved.
On the other hand, there is a specific periodic review of Mitigation Controls within the ARM tool. This will help periodically review the Master Data of the Mitigation Controls to ensure everything is up-to-date.
Business Role Management (BRM)
Similar to the previous case in the ARM module, when executing the Role Provisioning process, a mitigation control can be assigned to a Role that is going to be promoted to the Production system. It is important to note that when mitigating a Role, this will extend to all Users who currently have the Role assigned within the SAP® system.
SAP® GRC Process Control
The SAP® GRC Process Control module differs from the SAP® GRC Access Control module because it not only stores documentation but also performs monitoring operations within the SAP® system.
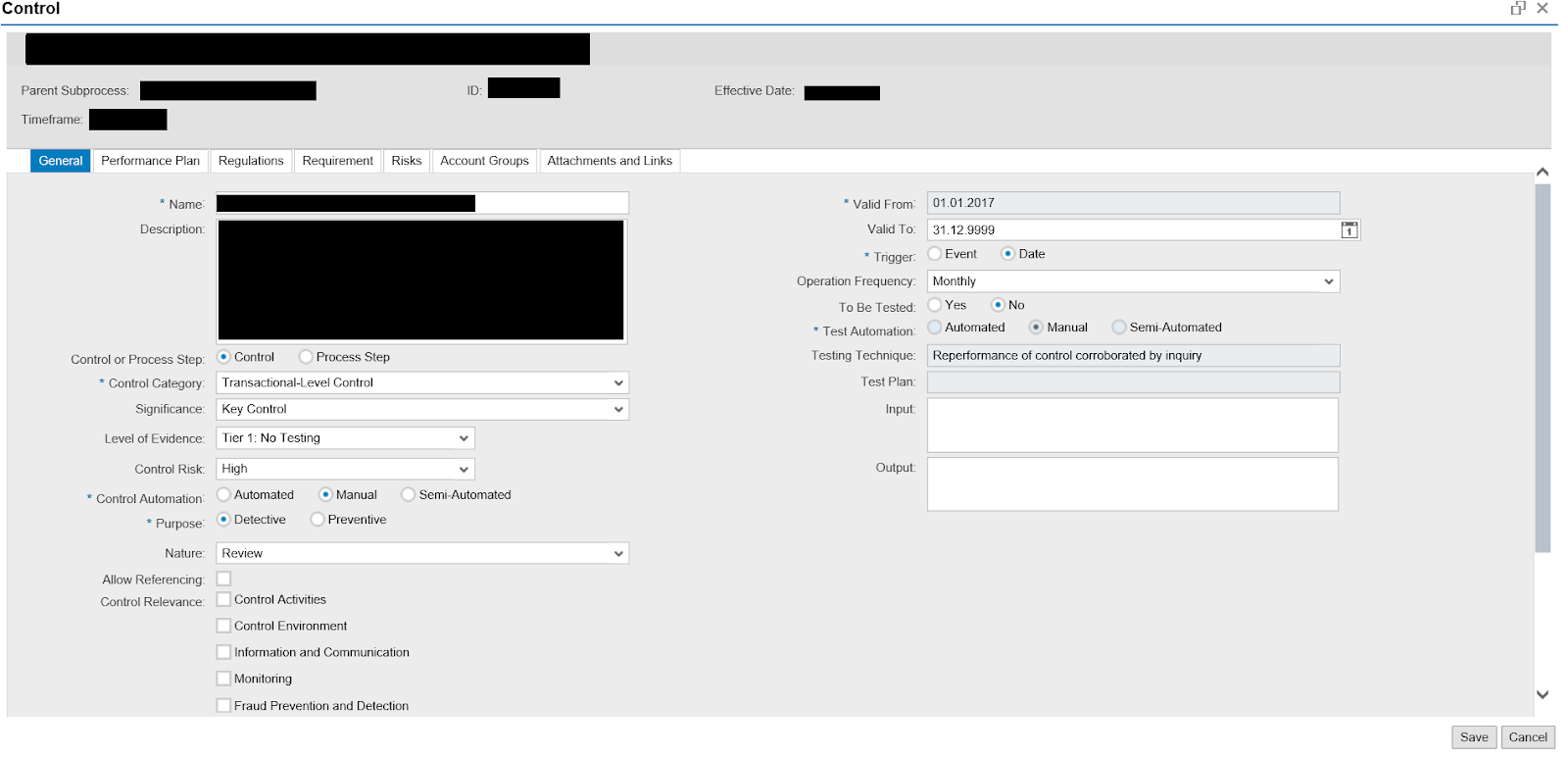
The Master Data for Mitigation Controls is much more detailed than the example we reviewed in the SAP® GRC Access Control Module:
The main differences are:
- Control Automation: defines whether the Control is automatic, semi-automatic, or manual.
- Level of Evidence: defines whether the Control needs to be tested.
- Purpose: indicates whether the Control is Preventive or Detective.
Additionally, the following tabs are key to defining the master data:
- Regulation: set the Regulation in which the Mitigation Control applies.
- Risk: set the Risk that may arise if the Control does not function as expected.
- Performance Plan: set the test steps and the responsible persons for each of them when performing the Control test.
- Attachment and Links: upload all information related to the mitigation control that will be sent to the responsible party when testing the control.
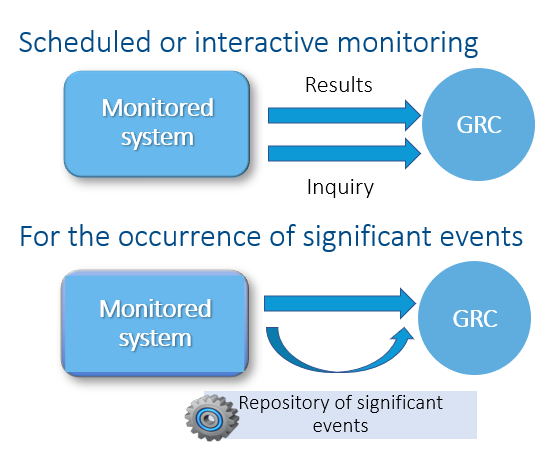
There are two types of operations that SAP® GRC Process Control can perform:
As mentioned earlier, the Process Control system can perform operations to verify if the Controls are functioning as expected within the system.
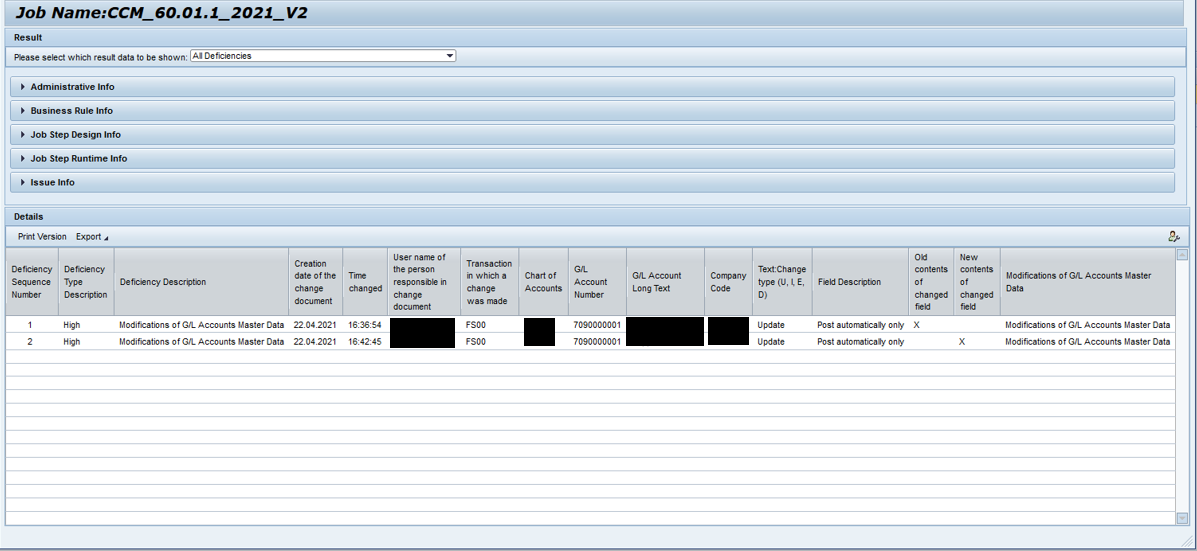
The following image detects all the GL accounts created within an SAP® system and identifies the person who created them. Additionally, as we discussed earlier, the advantage of Process Control is the ability to perform follow-up activities to ensure everything aligns with the Organization’s Policies.
SAP® Access Control and Process Control: Key Tools for Risk Mitigation in Your Organization
The SAP® GRC Access Control module helps organizations document Mitigation Controls and use them specifically for Access Risks.
On the other hand, the SAP® GRC Process Control module offers more advanced capabilities, excelling in automating Mitigation Controls and identifying deficiencies that do not comply with the Mitigation Control description. Both solutions are essential to ensure security and compliance within an organization.
At Inprosec, we have SAP® GRC experts who can help you implement and optimize these modules in your company. If you have any questions or would like more information, please do not hesitate to contact us by clicking here or continue exploring our blog to discover how we can help you strengthen your organization’s security.