Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
June 2021 notes
Summary and highlights of the month
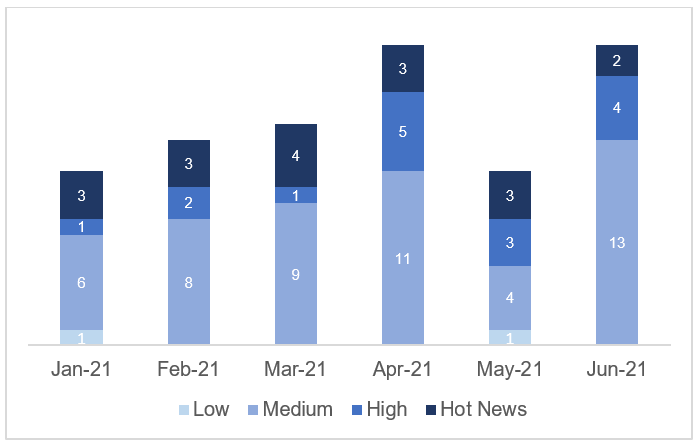
The total number of notes/patches has increased compared to last month. Despite this increase in the total number of notes, the number of Hot News has decreased, with 3 notes last month compared to 2 in June. On the other hand, it should be noted that the number of high criticality notes has increased from 3 to 4 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 6 scores (all those with a CVSS of 7 or higher).
We have a total of 20 notes for the whole month, 6 more than last May (19 from Patch Tuesday, 2 new ones and 17 updates, being 8 more than last month).
This month there are 2 critical notes (Hot News), an update and a new note, which stand out for their high CVVS. In addition we will review in detail 4 of the total of 4 high notes (those with CVSS greater than or equal to 7) where this month they would all be new notes.
- The most critical note of the month (with CVSS 9.9) is an update to a remote code execution vulnerability, where only an updated link to a FAQ document has been added.
- Next in criticality (CVSS 9), would be a note related to an inadequate authentication vulnerability, as an ABAP server could not correctly identify 100% whether the communication via RFC or HTTP is between application servers in the same SAP system or with servers outside the system.
- From there, we located the 4 notes of high criticality (high priority) being the most relevant with a CVSS of 8.7 a new note of Missing XML Validation that affects SAP NetWeaver AS for Java. The rest (14), would be medium and low level notes, and we will not see them in detail.
- This month the most predominant types are “Cross-Site Scripting (XSS)” (5/20 and 4*/19 in patch day) and “Memory Corruption” (4/20 and 4*/11 in patch day).
In the graph (post June 2021 from SAP) we can see the ranking of the June notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Remote Code Execution vulnerability in Source Rules of SAP Commerce (3040210): SAP Commerce Backoffice application allows certain authorized users to create source rules which are translated to drools rule when published to certain modules within the application. An attacker with this authorization can inject malicious code in the source rules and perform remote code execution enabling them to compromise the confidentiality, integrity and availability of the application. SAP Commerce Cloud addresses this vulnerability by adding validation and output encoding when processing Promotion Rules and other Source Rules. As mentioned earlier, this update is just a minor update that only contains an updated link on a FAQ document. CVSS v3 Base Score: 9,9 / 10 (CVE-2021-27602)
- Improper Authentication in SAP NetWeaver ABAP Server and ABAP Platform (3020104): The vulnerability affects SAP NetWeaver ABAP Server and ABAP Platform, that do not create information about internal and external RFC user in distinguished and consistent format, which may be exploited by malicious users to obtain illegitimate access to the system. The risk of an attack can be reduced by restricting access from network external sources for RFC and HTTP communication in network protection solution accordingly and with the correction provided in this SAP Note the identification of application servers within one SAP system is improved and allows communication to distinguish from application servers of another SAP system or external client and server programs. For the correction, a new Kernel version for RFC and HTTP is required and an ABAP correction for HTTP communication. CVSS v3 Base Score: 9 / 10 (CVE-2021-27610).
- Missing XML Validation in SAP NetWeaver AS for JAVA (3053066): The note is related with the vulnerability that a malicious user authenticated as an administrator can connect over a network and submit a specially crafted XML file which can be used to attack the Java NetWeaver system under consideration. This attack can fully compromise confidentiality by allowing the attacker to read any file on the filesystem or fully compromise availability by causing the system to crash. The attack cannot be used to change any data so that there is no compromise as to integrity. To fix the issue, the XML parser is now configured securely to validate submitted XML documents so that external entities are not allowed. To protect against attack, it is necessary to apply corresponding patch. CVSS v3 Base Score: 8.7 / 10 (CVE-2021-27635).
- Memory Corruption vulnerability in SAP NetWeaver ABAP Server and ABAP Platform (3020209): An unathenticated attacker without specific knowledge of the system can send a specially crafted packet over a network which will trigger an internal error in the system causing the system to crash and rendering it unavailable. In this attack, no data in the system can be viewed or modified. The crafted packet is a malformed request which is not recognized as such by the SAP Gateway process. As a consequence, the SAP Gateway attempts to handle the malformed request as if it were a proper request. The SAP Gateway might then attempt to copy from or into arbitrary memory locations. Malformed requests might then lead to a crash of the SAP Gateway process, which will in turn break all open RFC connections, and all registrations of programs with the SAP Gateway. With the correction, SAP Gateway is hardened against such memory corruption caused by request forgeries. To do so, implement the patch level of SAP Gateway mentioned in this SAP Note. CVSS v3 Base Score: 7.5 / 10 (Multiple CVEs).
- Memory Corruption vulnerability in SAP NetWeaver ABAP Server and ABAP Platform (3020104): An unauthenticated attacker without specific knowledge of the system can send a specially crafted packet over a network which will trigger an internal error in the system causing the system to crash and rendering it unavailable. Memory corruption can be provoked in SAP Enqueue Server (ENSA1) due to programming error. In this attack, no data in the system can be viewed or modified. The patch will protect against the memory corruption attacks described earlier by correcting a programming error. To apply the fix, implement the patch level mentioned in this SAP Note. CVSS v3 Base Score: 7.5 / 10 (Multiple CVEs).
- Memory Corruption vulnerability in SAP NetWeaver ABAP Server and ABAP Platform (3021197): SAP NetWeaver ABAP Server and ABAP Platform are vulnerable for externally triggered memory corruption. More precisely, the Dispatcher process of an SAP system is vulnerable for request forgery using a crafted packet of SAP´s proprietary DIAG protocol, which is used for SAP GUI communication. The packet causes a crash either of a work process or of the Dispatcher process. The latter immediately causes a hard shutdown of the application server. In this attack, no data in the system can be viewed or modified. By the provided correction, disp+work is hardened against memory corruption caused by such request forgeries.. CVSS v3 Base Score: 7.5 / 10 (Multiple CVEs).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for June:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-junio-2021
Other references, from SAP and Onapsis (June):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=578125999
Resources affected
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Business One, versión 10.0;
- SAP Commerce, versiones 1808, 1811, 1905, 2005 y 2011;
- SAP Commerce Cloud, versión 100;
- SAP Enable Now (SAP Workforce Performance Builder – Manager), versiones 10.0 y 1.0;
- SAP Fiori Apps 2.0 for Travel Management in SAP ERP, versión 608.
- SAP Manufacturing Execution, versiones 15.1, 1.5.2, 15.3 y 15.4;
- SAP NetWeaver ABAP Server y ABAP Platform (Dispatcher):
-
- KERNEL, versiones 7.22, 8.04, 7.49, 7.53, 7.73, 7.77, 7.81, 7.82 y 7.83;
- KRNL32NUC, versiones 7.22 y 7.22EXT;
- KRNL32UC, versiones 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 8.04, 7.22, 7.22EXT, 7.49, 7.53 y 7.73;
- SAP NetWeaver ABAP Server y ABAP Platform (Enqueue Server):
-
- KERNEL, versiones 7.22, 8.04, 7.49, 7.53 y 7.73;
- KRNL32NUC, versiones 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 8.04, 7.22, 7.22EXT, 7.49, 7.53, y 7.73;
- SAP NetWeaver AS (Internet Graphics Server – Portwatcher), versiones 7.20, 7.20EXT, 7.53, 7.20_EX2 y 7.81;
- SAP NetWeaver AS ABAP:
-
- KERNEL, versiones 7.22, 8.04, 7.49, 7.53, 7.73, 7.77, 7.81, 7.82, 7.83 y 7.84;
- KRNL32NUC, versiones 7.22 y 7.22EXT;
- KRNL32UC, versiones 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 8.04, 7.22, 7.22EXT, 7.49, 7.53 y 7.73;
- SAP NetWeaver AS ABAP (RFC Gateway):
-
- KERNEL, versiones 7.22, 8.04, 7.49, 7.53, 7.73, 7.77, 7.81, 7.82 y 7.83;
- KRNL32NUC, versiones 7.22 y 7.22EXT;
- KRNL64NUC, versiones 7.22, 7.22EXT y 7.49;
- KRNL64UC, versiones 8.04, 7.22, 7.22EXT, 7.49, 7.53 y 7.73;
- SAP NetWeaver AS ABAP (Web Survey), versiones 700, 702, 710, 711, 730, 731, 750, 750, 752, 75A y 75F;
- SAP NetWeaver AS ABAP y ABAP Platform, versiones 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755 y 804;
- SAP NetWeaver AS ABAP y ABAP Platform (SRM_RFC_SUBMIT_REPORT), versiones 700, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754 y 755;
- SAP NetWeaver AS for JAVA, versiones 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver AS for Java (UserAdmin), versiones 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver Application Server ABAP (Aplicaciones basadas en SAP GUI para HTML):
- KERNEL, versiones 7.49, 7.53, 7.77, 7.81 y 7.84;
- KRNL64NUC, versión 7.49;
- KRNL64UC, versiones 7.49 y 7.53;
- SAP NetWeaver Application Server ABAP (Aplicaciones basadas en Web Dynpro ABAP):
-
- SAP_BASIS, versión 702,31;
- SAP_UI, versiones 750, 752, 753, 754 y 755;