Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
January 2026 Notes
Monthly Summary and Highlights
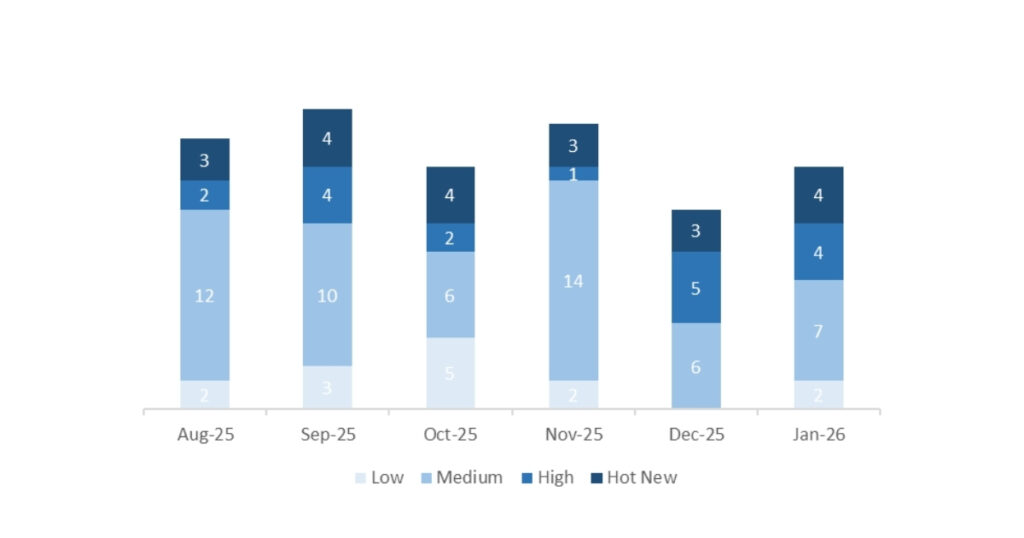
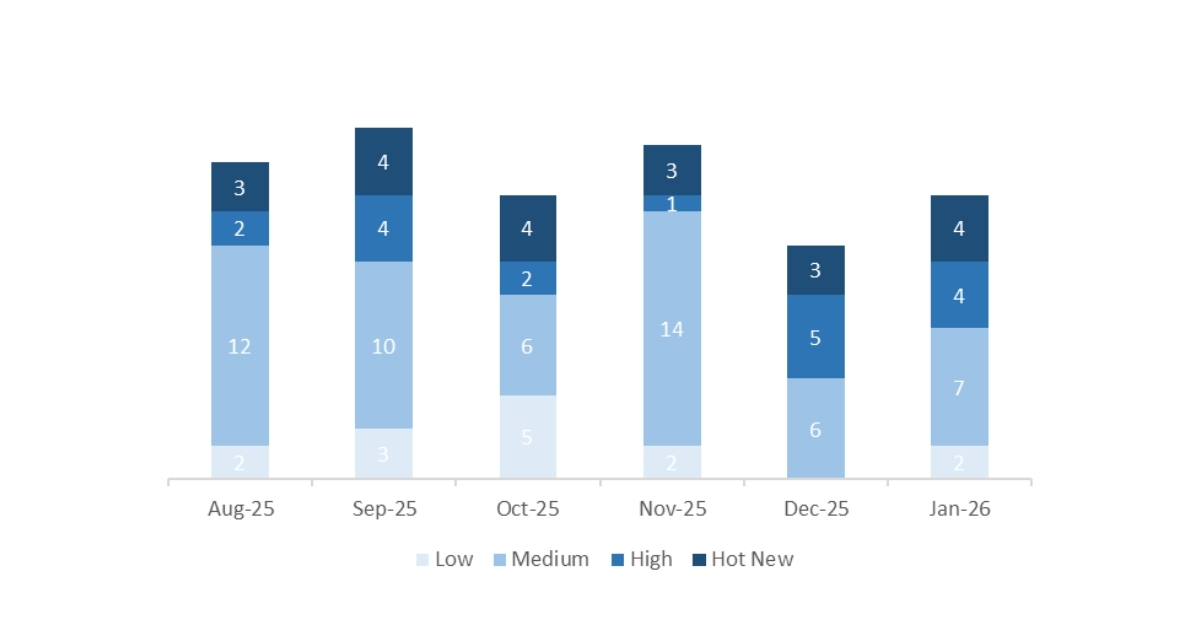
This month, a total of 17 notes were released, 3 more than in December 2025. Four Hot News notes were published, one more than in the previous period. Regarding high-criticality notes, there are 4, one fewer compared to December. Medium and low notes will not be reviewed, therefore we will provide details on a total of 8 notes (all those with a CVSS score of 7 or higher).
We have a total of 17 notes for the entire month (all 17 are new, and there are no updates to notes published in previous months).
We will review in detail a total of 8 notes, all of them high-criticality and Hot News:
-
The most critical note of the month (CVSS 9.9) is a Hot News note, related to “SQL Injection Vulnerability in SAP S/4HANA Private Cloud and On-Premise”.
-
The next most critical note (CVSS 9.6) is another Hot News, the second of the month, related to “Remote code execution in SAP Wily Introscope Enterprise Manager”.
-
The following notes in terms of criticality (CVSS 9.1) are two Hot News notes: one related to “Code Injection vulnerability in SAP S/4HANA” and the other to “Code Injection vulnerability in SAP Landscape Transformation”.
-
The next one is a high-criticality note (CVSS 8.8) related to “Privilege escalation vulnerability in SAP HANA database”.
-
The next in criticality (CVSS 8.4) is the second high-criticality note, related to “OS Command Injection vulnerability in SAP Application Server for ABAP and SAP NetWeaver RFCSDK”.
-
The following notes in terms of criticality (CVSS 8.1) are two high-criticality notes, related to “Multiple vulnerabilities in SAP Fiori App (Intercompany Balance Reconciliation)” and “Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform”.
-
This month, the most predominant vulnerability type was “Code Injection” (3/17 on patch day).
In the chart, we can see the classification of the January notes, as well as the trend and classification over the previous 5 months (only Sec. Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
-
SQL Injection Vulnerability in SAP S/4HANA Private Cloud and On-Premise (Financials – General Ledger) (3687749): Due to insufficient input validation an authenticated user could execute crafted SQL queries to read, modify, and delete backend database data. This leads to a high impact on the confidentiality, integrity, and availability of the application. A temporary workaround is available. CVSS v3 Base Score 9,9/ 10 [CVE-2026-0501]
-
Remote code execution in SAP Wily Introscope Enterprise Manager (WorkStation) (3668679): Due to a critical remote code execution vulnerability, an unauthenticated attacker could craft a malicious JNLP (Java Network Launch Protocol) file and host it via a public URL. Once a victim accesses this URL, the Wily Introscope Server can be leveraged to execute arbitrary commands on the victim’s application environment. This exploit poses a severe risk as it could lead to a total compromise of the application’s confidentiality, integrity, and availability. CVSS v3 Base Score 9,6/ 10 [CVE-2026-0500]
-
Code Injection vulnerability in SAP S/4HANA (Private Cloud and On-Premise) (3694242): SAP S/4HANA (Private Cloud and On-Premise) allows an attacker with admin privileges to exploit a vulnerability in the function module exposed via RFC. This flaw enables the injection of arbitrary ABAP code/OS commands into the system, bypassing essential authorization checks. This vulnerability effectively functions as a backdoor, creating the risk of full system compromise, undermining the confidentiality, integrity and availability of the system. CVSS v3 Base Score 9,1/ 10 [CVE-2026-0498]
-
Code Injection vulnerability in SAP Landscape Transformation (3697979): A security flaw in SAP Landscape Transformation allows an attacker with administrative privileges to exploit a vulnerability within a function module exposed via RFC. By leveraging this weakness, an unauthorized user can inject arbitrary ABAP code or OS commands into the system while bypassing critical authorization checks. This vulnerability essentially operates as a backdoor, posing a severe risk of a full system compromise the confidentiality, integrity, and availability of the entire environment. CVSS v3 Base Score 9,1/ 10 [CVE-2026-0491]
-
Privilege escalation vulnerability in SAP HANA database (3691059): SAP HANA database is vulnerable to privilege escalation allowing an attacker with valid credentials of any user to switch to another user potentially gaining administrative access. This exploit could result in a total compromise of the system’s confidentiality, integrity, and availability. CVSS v3 Base Score 8,8/ 10 [CVE-2026-0492]
-
OS Command Injection vulnerability in SAP Application Server for ABAP and SAP NetWeaver RFCSDK (3675151): Due to an OS Command Injection vulnerability in SAP Application Server for ABAP and SAP NetWeaver RFCSDK, an authenticated attacker with administrative access and adjacent network access could upload specially crafted content to the server. If processed by the application, this content enables execution of arbitrary operating system commands. Successful exploitation could lead to full compromise of the system’s confidentiality, integrity, and availability. CVSS v3 Base Score 8,4/ 10 [CVE-2026-0507]
-
Multiple vulnerabilities in SAP Fiori App (Intercompany Balance Reconciliation) (3565506): SAP Fiori App Intercompany Balance Reconciliation does not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. This has high impact on confidentiality and integrity of the application, availability is not impacted.. CVSS v3 Base Score 8,1/ 10 [CVE-2026-0511]
-
Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform (3688703): SAP Web Due to a Missing Authorization Check vulnerability in Application Server ABAP and ABAP Platform, an authenticated attacker could misuse an RFC function to execute form routines (FORMs) in the ABAP system. Successful exploitation could allow the attacker to write or modify data accessible via FORMs and invoke system functionality exposed via FORMs, resulting in a high impact on integrity and availability, while confidentiality remains unaffected. CVSS v3 Base Score 8,1/ 10 [CVE-2026-0506]
Reference links
Other references, from SAP and Onapsis (january):
SAP Security Patch Day – January 2026
SAP Patch Day: January 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
- SAP S/4HANA Private Cloud and On-Premise (Financials – General Ledger) Version(s) – S4CORE 102, 103, 104, 105, 106, 107, 108, 109
- SAP Wily Introscope Enterprise Manager (WorkStation) – WILY_INTRO_ENTERPRISE 10.8
- SAP S/4HANA (Private Cloud and On-Premise) – S4CORE 102, 103, 104, 105, 106, 107, 108, 109
- SAP Landscape Transformation – DMIS 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2018_1_752, 2020
- SAP HANA database – SAP HANA database HDB 2.00
- SAP Application Server for ABAP and SAP NetWeaver RFCSDK – KRNL64UC 7.53, NWRFCSDK 7.50, KERNEL 7.53, 7.54, 7.77, 7.89, 7.93, 9.16
- SAP Fiori App (Intercompany Balance Reconciliation) – UIAPFI70 500, 600, 700, 800, 900, 901, 902, S4CORE 102, 103, 104, 105, 106, 107, 108
- SAP NetWeaver Application Server ABAP and ABAP Platform – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758, SAP_BASIS 816
- SAP ERP Central Component and SAP S/4HANA (SAP EHS Management) – SAP_APPL 618, S4CORE 102, 103, 104, 105, 106, 107, 108, 109, EA-APPL 605, 606, 617
- SAP NetWeaver Enterprise Portal – EP-RUNTIME 7.50
- SAP Business Connector – SAP BC 4.8
- SAP Supplier Relationship Management (SICF Handler in SRM Catalog) – SRM_SERVER 700, 701, 702, 713, 714
- SAP Identity Management – DM_CLM_REST_API 8.0, IDMIC 8.0