Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
Today we bring you the update of the Q3 2020 SAP security notes. Although there has been a large drop in the number of notes published (as last quarter was the highest ever), we still have a significant number of critical notes and also in the same quarter we have two new notes of maximum criticality (CVSS 10). It should be noted that at least one of them could affect you, since it is precisely for SAP Solution Manager.
Q3 2020 notes
Summary and highlights of the quarter
The total number of notes/patches has decreased compared to the last quarter. It also decreases the number of critical and high notes. Except for last quarter where we didn’t find any low notes, they are present in this quarter. As always we will leave the middle and low grades unchecked this quarter, but we will detail a total of 15 grades (all those with a CVSS of 7 or higher). As we said before, if you highlight that the critical notes are especially high level (CVSS).
We have 6 unique critical notes (Hot News), totaling 8 this quarter, one of which is the recurring update for the SAP Business Client with Chromium with 2 appearances and a review of SAP NetWeaver AS JAVA (LM Configuration Wizard) which appears in July and is updated in August. We will also review in detail 9 of the total 9 high scores (those of CVSS greater or equal to 7) for the review in detail of 15 different scores.
- The most critical notes of the quarter (both with CVSS 10) one related to multiple vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard) and the other the update affecting the lack of authentication verification in SAP Solution Manager.
- The next in criticality (CVSS 9. 8) are 2. It is the usual “Browser Control Chromium Delivered with SAP Business Client (2622660)” which appears twice in this quarter, the first time in July and then in September.
- From there, we have a review with a CVSS of 9. 6, another with 9. 1 and the last one with a CVSS of 9.
- Of the high level ones we should perhaps point out that there are 2 for SAP NetWeaver (ABAP) and ABAP Platform, the main note and the update with CVSS of 8. 3.
We have a total of 61 notes for the entire quarter, 20 less than last quarter (42 of the Tuesday patches, 24 less than last quarter):
- A total of 20 notes were released in July (10 in the Security Notes Tuesday – 8 new and 2 updates to previous notes).
- We also have a total of 2 “hot news” (reviews). One that affects SAP NetWeaver AS JAVA (LM Configuration Wizard), due to several vulnerabilities, and the second, which is a repeat update for “Browser Control Chromium Delivered with SAP Business Client (2622660)”. Both with a CVSS of 10 and 9. 8 respectively.
- There are also 2 high priority notes, one affecting SAP NetWeaver (XMLToolkit for Java) with a CVSS of 7. 7 and the other, which is an update affecting information disclosure in SAP ABAP Server with a CVSS of 7. 4. The rest (16) are medium and low level, and we will not see them in detail although it is worth noting that 3 medium level affect SAP Business Objects.
- This month the most predominant types are “Missing Authorization Check” (6/20 and 0/10 in patch day) and “Cross-Site Scripting (XSS)” (4/20 and 4/10 in patch day).
- A total of 21 notes were published in August (16 in the Security Notes Tuesday – 15 new and 1 update of previous notes).
- We have a total of 2 “hot news” (critical), 1 new, which would be related to the type “Cross-Site Scripting (XSS)” and 1 update of the note we saw in July “Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard)”. The same number of critical notes as last month, with 1 new and 1 updated.
- There are also 6 high priority notes, the most relevant with a CVSS of 8. 5, which through unauthenticated access of an attacker to the server, allows to obtain the username and password of connected users. The rest of the scores (13) are of a lower level – mostly medium level – and the platform highlighted this month is SAP Netweaver, with a total of 7 scores (2 reviews, 3 additions and 2 averages).
- This month the most predominant types are “Information Disclosure” (5/21 and 4/16 in patch day) and secondly tied “Cross-Site Scripting (XSS)” (4/21 and 3/16 in patch day) and “Missing Authorization Check” (4/21 and 4/16 in patch day).
- A total of 20 notes were published in September (16 in the Security Notes Tuesday – 10 new and 6 updates to a previous note).
- We have a total of 4 “hot news” (reviews), two updates and two new ones. These are the update ones, one due to the lack of authentication verification affecting SAP Solution Manager and the other for the classic “Browser Control Chromium Delivered with SAP Business Client (2622660)”. Both with a CVSS of 10 and 9. 8 respectively. With respect to the two new ones, we found one that affects SAP Marketing due to inadequate access control, and another one of code vulnerability in SAP NetWeaver (ABAP Server) and ABAP Platform. Both with a CVSS of 9. 6 and 9. 1 respectively.
- There are also 2 high priority notes, the most relevant being an update also for SAP NetWeaver (ABAP) and ABAP Platform with a CVSS of 8. 3. The second, also updated with a CVSS of 7. 6, would affect SAP NetWeaver AS ABAP due to the vulnerability of application forgery.
- This month the most predominant types are “Cross-Site Scripting (XSS)” (5/20 and 4*/16 in patch day) and “Missing Authorization Check” (4/20 and 2*/16 in patch day).
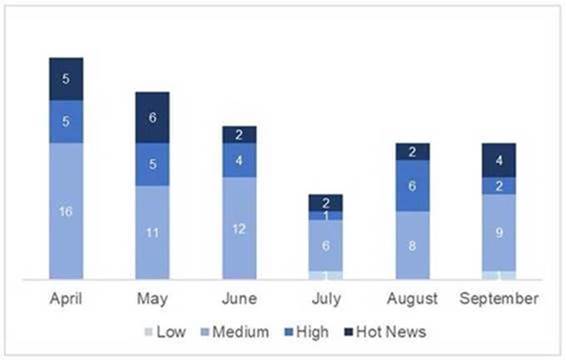
In the graph (post September 2020 of SAP) we can see the evolution and classification of the notes of the 3 months of the second quarter of the year (2020), in addition to the 3 months of the last quarter (only the notes of the Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Missing XML Validation Vulnerability in SAP Commerce (2904480): SAP Hybris is an eCommerce Java-based platform that provides solutions for B2B and B2C commerce, among others. This vulnerability is present in SAP Hybris with a default configuration and exploitable by a remote unauthenticated attacker. It could potentially allow a malicious agent to read sensitive files and data from the system and even affect availability (in some limited scenarios). SAP has provided patches for both SAP Hybris on-prem implementations as well as SAP Commerce Cloud. CVSS v3 Base Score: 9.3 / 10 (CVE-2020-6238).
- Directory Traversal Vulnerability in SAP NetWeaver (Knowledge Management) (2896682): this vulnerability is a Path Traversal present in SAP NetWeaver Knowledge Management, which is a centralized access point for distributed repositories of files along the systems. It lets users navigate through folders, create, delete files, etc. In all these functionalities, a user can upload files. If unpatched, the system does not sufficiently validate input and therefore may allow a potential attacker to overwrite, delete or corrupt arbitrary files on the remote server. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-6225).
- Update 2 to Security Note 2808158: OS Command Injection vulnerability in SAP Diagnostics Agent (2839864): In this latest update, SAP updated the ‘Attachments’ section adding a correction in one of the files attached to the note. If you want to better understand the scope and severity of this vulnerability, you can read previous post regarding the original note (Q3 2019). We can confirm that this latest update is a minor one, that improves attachments for customization of the protection after the patch. Customers who have applied the March fix are protected against critical exploitation of this vulnerability.. CVSS v3 Base Score: 9.1 / 10 (CVE-2019-0330).
- Deserialization of Untrusted Data in SAP Business Objects Business Intelligence Platform (CrystalReports WebForm Viewer) (2863731): This notes appears in April and then it is updated in May. It describes the possibility of a remote command execution caused by a deserialization attack in SAP BusinessObjects Business Intelligence Platform. Parameters of a specific component can be manipulated in order to inject deserialized content. The provided fix enables data encryption for the traffic between client and server so that it can no longer be read. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-6219).
- Code Injection vulnerability in SAP OrientDB 3.0 (2900118): It fixes a Code Injection vulnerability in SAP OrientDB 3.0. SAP OrientDB is a multi-model, graph-based, no-SQL database that SAP acquired from Callidus Software Inc. in 2018. Because an attacker requires authentication and script execution privileges the level vulnerability is not the highest. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-6230).
- Missing authentication check in SAP Solution Manager (Diagnostics Agent) (2906994): It fixes a missing authentication check in SAP SolMan, which may allow an attacker to read sensitive information or even access administrative or other privileged functionalities abusing the lack of an authentication check-in a component. This vulnerability, despite being a little bit less critical (CVSS vector-only affects confidentiality), has some similarities with the one patched in SAP Security Note #2890213, HotNews that was previously released in March 2019. Both vulnerabilities allow an unauthenticated attacker to get privileged access to SolMan and, combined with other vulnerabilities, post-exploitation alternatives include critical scenarios for affected customers if attacked. CVSS v3 Base Score: 8.6 / 10 (CVE-2020-6235).
- Update to Security Note: Remote Code Execution in SAP Business Objects Business Intelligence Platform (Crystal Reports) (2861301): While this vulnerability also allows the remote execution of code with an even higher impact on the application’s confidentiality and integrity, unlike #2863731, this vulnerability requires user interaction and therefore the CVSS is lower in this case. CVSS v3 Base Score: 8.1 / 10 (CVE-2020-6208).
- Information Disclosure in SAP Business Objects Business Intelligence Platform (dswsbobje Web Application) (2898077): It fixes an Information Disclosure vulnerability. A non-authenticated user could exploit this vulnerability with CVSS of 7.5 in a certain web application of SAP BusinessObjects in order to gain information that can be then used for further exploits and/or attacks. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-6237).
- Code Injection vulnerability in Service Data Download (2835979): Due to an insufficient input validation in a remote-enabled function module that dynamically generates code, an attacker can take complete control of any SAP NW ABAP system that is connected to a Solution Manager (SolMan) system. Only the fact that an attacker needs a minimum level of authorizations to exploit this vulnerability has prevented it from receiving a CVSS of 10.0. Fortunately, there are no manual steps involved in the provided fix. Strong recommendation in applying the corresponding patch as soon as possible is given. CVSS v3 Base Score: 9.9 / 10 (CVE-2020-6262).
- Update – Security Updates for the Browser Control Chromium Delivered with SAP Business Client (2622660): This note addresses multiple vulnerabilities in the third-party web browser control Chromium, which is used in SAP Business Client and is periodically updated based on web browser updates. Since exploits for third-party tools are more common than exploits that are SAP-specific, which tend to be more targeted and selective, it is important to keep this note installed with every update to stay secure. These patches provide support for Chromium version 81.0.4044.92. CVSS v3 Base Score: 9.8 / 10
- Missing Authentication check in SAP Business Objects Business Intelligence Platform (Live Data Connect) (2885244): It describes a scenario that leads to a missing authentication vulnerability. Thanks to the unchanged scope in case of an exploit, the CVSS is “only” 9.8. CVSS v3 Base Score: 9.8 / 10 (CVE-2020-6242).
- Code injection in SAP Adaptive Server Enterprise (Backup Server) (2917275): SAP Adaptive Server Enterprise (ASE) Backup Server does not perform the necessary validation checks for an authenticated user while executing DUMP or LOAD command allowing arbitrary code execution or Code Injection. SAP ASE is one of the SQL database servers supported by SAP business applications. It uses a relational data management model and provides on-premises as well as cloud deployment options. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-6248).
- Information Disclosure in SAP Adaptive Server Enterprise (Cockpit) (2917090): Under certain conditions SAP Adaptive Server Enterprise (ASE) Cockpit allows an attacker to access sensitive and confidential information through local network which would otherwise be restricted. It could be used to get user account credentials, tamper with system data and impact system availability. Some well-known impacts of Information Disclosure are: 1) loss of information and system configuration confidentiality; 2) information gathering for further exploits and attacks. SAP ASE is one of the SQL database servers supported by SAP business applications. It uses a relational data management model and provides on-premises as well as cloud deployment options. CVSS v3 Base Score: 9.0 / 10 (CVE-2020-6252).
- SQL Injection vulnerability in SAP Adaptive Server Enterprise (2916927): The note provides fixing SQL Injection vulnerabilities that can lead to an escalation of privileges and thus allowing authenticated users to execute commands that they are otherwise not allowed to execute. CVSS v3 Base Score: 8.8 / 10 (CVE-2020-6241).
- Information Disclosure in SAP Landscape Management (2903743): A disclosure vulnerability exists in the enterprise edition or standard edition of SAP Landscape Management that would allow an authenticated user with high privilege to obtain privileged access to other systems making those other systems vulnerable to information disclosure and modification. The information disclosed are the credentials. The disclosed information can only be accessed by authenticated users with high privileges (J2EE administrator), but they can escalate their privileges to other systems. CVSS v3 Base Score: 8.7 / 10 (CVE-2020-6243).
- Code Injection in SAP Adaptive Server Enterprise (XP Server on Windows Platform) (2915585): SAP Adaptive Server Enterprise (XP Server on Windows Platform) does not perform the necessary checks for an authenticated user while executing the extended stored procedure. Under certain conditions, the impact of this code injection is that the potential attacker can read, modify and delete restricted data on connected servers. CVSS v3 Base Score: 8.0 / 10 (CVE-2020-6243).
- SQL Injection vulnerability in SAP Master Data Governance(MDG) (2908560): The use of an admin backend report from within MDG allows an attacker to execute crafted database queries, exposing the backend database. Some well-known impacts of SQL Injection vulnerability are: 1) Read sensitive data; 2) Execute admin level operations on database. CVSS v3 Base Score: 7.7 / 10 (CVE-2020-6249).
- ‘Ghostcat’ Apache Tomcat AJP Vulnerability in SAP Liquidity Management for Banking (2928570): Due to a known vulnerability in Apache Tomcat, called “Ghostcat,” SAP strongly recommends disabling all ports using the Apache JServ Protocol (AJP Protocol). While the note points out the risk of a remote code execution, the description of the corresponding vulnerability mentions that “AJP connections…can be exploited in ways that may be surprising.” The latter statement, together with the CVSS score of 9.8, should be reason enough to disable all AJP ports. If customers absolutely need the AJP protocol in their scenario, the note recommends to set the required secret attribute in the configuration of the AJP connector. CVSS v3 Base Score: 9.8 / 10 (CVE-2020-1938).
- Use of Hard-coded Credentials in SAP Commerce and SAP Commerce Datahub (2918924): It addresses hard-coded user credentials in SAP Commerce and SAP Commerce Data Hub. This problem can be found in many software products because the products use some built-in accounts with publicly known passwords and do not force the administrators to change these passwords during or after installing the application. For example, every SAP Basis person knows the owners of “6071992” or “admin” passwords. SAP has now solved the problem for SAP Commerce and SAP Commerce Data Hub. After applying the patch, a new installation of SAP Commerce will only activate the built-in “admin” account. The installer is forced to maintain an initial password for that account. Other built-in users are still created during installation, but they are inactive until an individual password is set for these accounts. The later rule also applies to all built-in users of SAP Commerce Data Hub. An important fact is that the patches only affect new installations of SAP Commerce (Data Hub). They do not remove default passwords from built-in accounts of existing installations. As one option to achieve this, the note proposes to re-initialize the SAP Commerce installation after applying the patch, an option that likely does not apply to most customers. Therefore, the note also provides a Disabling All Default Passwords for Users Guide to remove the default passwords from all built-in accounts. CVSS v3 Base Score: 9.8 / 10 (CVE-2020-6265).
- Information Disclosure in SAP Commerce (2906366): It fixes an Information Disclosure vulnerability in SAP Commerce. Under a specific configuration of some property values, a malicious user could exploit insecure features of the login-form to gain information that could be used for further exploits and attacks. Some of the required property values are even set by default. CVSS v3 Base Score: 8.6 / 10 (CVE-2020-6264).
- Missing XML Validation in SAP Solution Manager (Problem Context Manager) (2931391): It describes a Missing XML Validation vulnerability in Problem Context Manager. While an exploit has only a minor impact on the system’s confidentiality, it can have a serious impact on the system’s availability. CVSS v3 Base Score: 8.2 / 10 (CVE-2020-6271).
- Server Side Request Forgery vulnerability in SAP NetWeaver AS ABAP (2912939): It fixes a vulnerability in the architecture of the batch input process allowing a malicious user to grab user credentials. Although the impact on the system’s integrity, confidentiality and availability is high, the CVSS score is “only” 7.6 as the attack complexity is high and it also needs admin privileges on MS SQL Server as well as batch input authorizations in SAP in order to successfully exploit the vulnerability. CVSS v3 Base Score: 7.6 / 10 (CVE-2020-6275).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for the 3 months of this quarter:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-julio-2020
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-agosto-2020
Other references, from SAP and Onapsis (in order: July->September):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552599675
https://onapsis.com/blog/sap-security-notes-july-2020-recon
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552603345
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=557449700
https://onapsis.com/blog/sap-security-notes-september-2020
Resources affected
- BANKING SERVICES FROM SAP 9.0 (Bank Analyzer), versión 500;
- S/4HANA FIN PROD SUBLDGR, versión 100;
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Adaptive Server Enterprise, versiones 15.7, 16.0.
- SAP Banking Services (Generic Market Data), versiones 400, 450 y 500;
- SAP Business Client, versión 6.5;
- SAP Business Objects Business Intelligence Platform (BI Workspace), versiones 4.1 y 4.2;
- SAP Business Objects Business Intelligence Platform, versiones 4.1, 4.2 y 4.3.
- SAP Commerce, versiones 6.7, 1808, 1811, 1905 y 2005;
- SAP Data Intelligence, versión 3;
- SAP Disclosure Management, versión 1.0;
- SAP ERP (HCM Travel Management), versiones 600, 602, 603, 604, 605, 606, 607 y 608;
- SAP Marketing (Mobile Channel Servlet), versiones 130, 140 y 150;
- SAP NetWeaver:
- ABAP Server y ABAP Platform, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754 y 755;
- AS ABAP (BSP Test Application), versiones 700, 701, 702, 730, 731, 740, 750, 751, 752, 753, 754 y755;
- AS ABAP, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753 y 754;
- Knowledge Management, versiones 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver AS JAVA (P4 Protocol), versiones:
- CORE-TOOLS (IIOP service) versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- ENGINEAPI versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50
- J2EE-FRMW versiones J2EE-FRMW 7.10 y 7.11
- LM Configuration Wizard versiones 7.30, 7.31, 7.40 y 7.50;
- SERVERCOR (IIOP service) versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SERVERCORE versiones 7.10, 7.10 y 7.11;
- WSRM versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP S/4 HANA (Fiori UI for General Ledger Accounting), versiones 103 y 104;
- SAP Solution Manager (User Experience Monitoring), versión 7.2;
- SAPFiori (Launchpad), versiones 750, 752, 753, 754 y 755;
- SAPUI5 (SAP_UI), versiones 750, 751, 752, 753, 754 y 755;
- SAPUI5 (UI_700), versión 200;
- SAPUI5 (UISAPUI5_JAVA), versión 7.50;