Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
May 2022 notes
Summary and highlights of the month
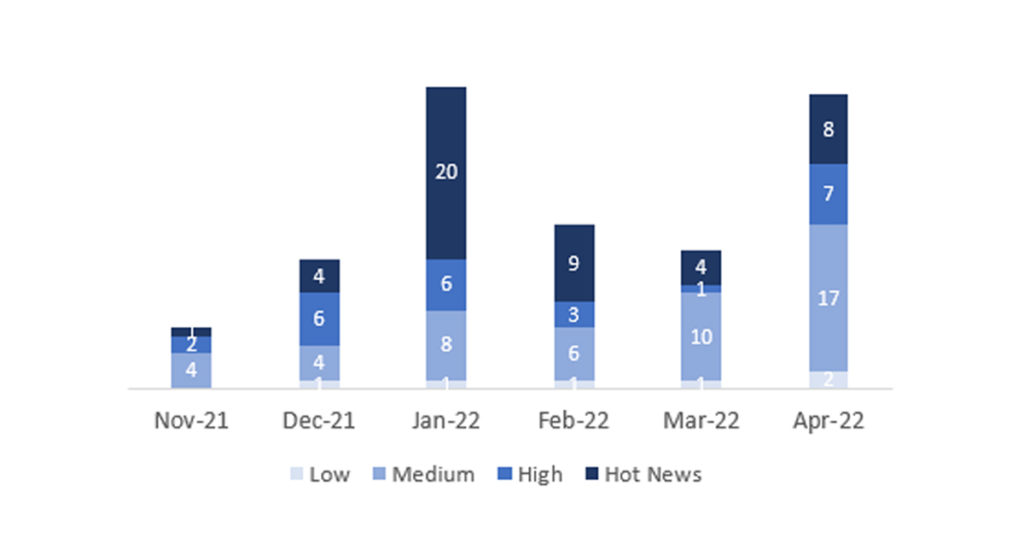
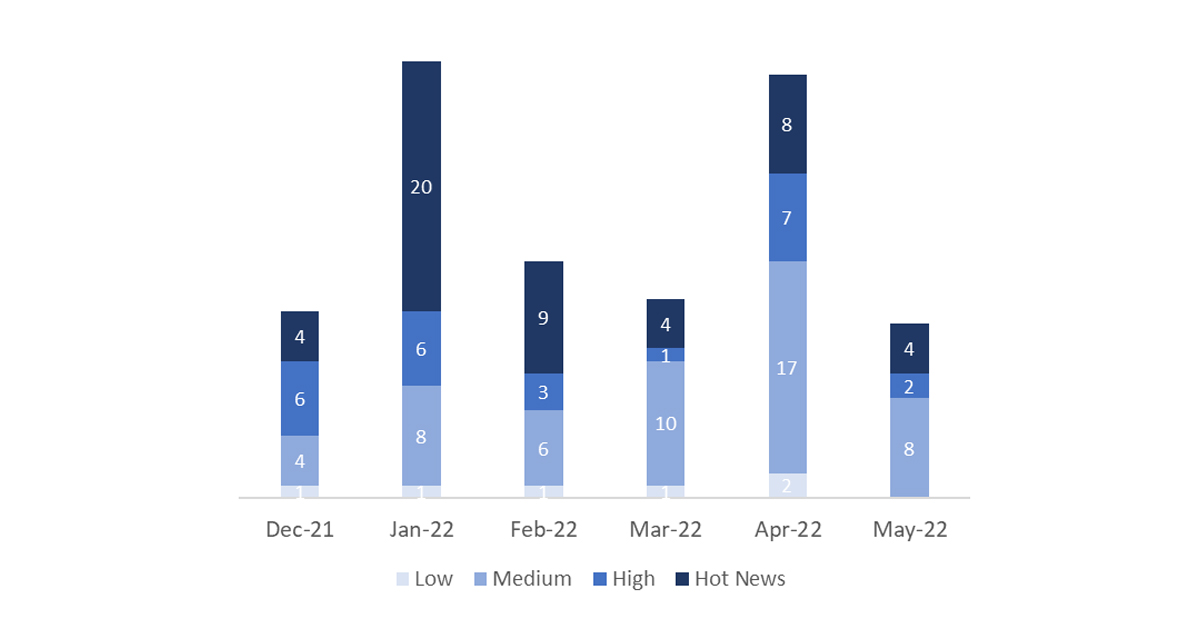
The total number of notes/patches has decreased compared to last month. In addition to this decrease in the total number of notes, the number of Hot News also decreased, with 8 notes last month compared to 4 in May. On the other hand, it should be noted that the number of high criticality notes decreased from 7 to 2 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 6 scores (all those with a CVSS of 7 or higher).
We have a total of 17 notes for the whole month, 18 less than last April (12 from Patch Tuesday, 8 new and 4 updates, being 21 less than last month).
We have 4 Hot News, 3 new and 1 update, in this month, which stand out for their high CVVS. We will also review in detail 2 of the total of 2 new high notes (those with CVSS greater than or equal to 7).
- The most critical notes of the month (with CVSS 9.8) are 4 related to “Remote Code Execution vulnerability”.
- The next in criticality (CVSS 8.3 and 7.8) are two critical scores, one for “Cross-Site Scripting (XSS) vulnerability in administration UI of SAP Webdispatcher and SAP Netweaver AS for ABAP and Java (ICM)” and the other for “Central Management Server Information Disclosure in Business Intelligence Update”.
- The rest (11) are medium level, and we will not look at them in detail, although it is worth noting that there is more than one that affects SAP NetWeaver.
- This month the most predominant types are “Remote Code Execution vulnerability” (4/17 and 4/12 in patch day) and “Cross-Site Scripting (XSS)” (3/17 and 3/17 in patch day).
In the graph (post May 2022 from SAP) we can see the classification of the May notes in addition to the evolution and classification of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Remote Code Execution vulnerability associated with Spring Framework used in in SAP Business One Cloud (3189409): Symptom: SAP Business One Cloud 1.1 uses a version of Spring Framework which has Remote Code Execution vulnerability. Solution: Upgrade to SAP Business One Cloud 1.1 PL18 Hotfix1. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Update – Central Security Note for Remote Code Execution vulnerability associated with Spring Framework (3170990): This security note is the central document to consolidate all SAP Security Notes released for the Remote Code Execution vulnerability associated with Spring Framework. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
The Spring4Shell Summary HotNews Note, #3170990 was updated and currently includes the following affected SAP applications.
| Note |
SAP Application |
| 3189428 | SAP HANA Extended Application Services |
| 3187290 | SAP Customer Checkout |
| 3189429 | Sybase PowerDesigner Web |
| 3189635 | SAP Customer Profitability Analytics |
| 3171258 | SAP Commerce |
| 3189409 | SAP Business One Cloud |
- Remote Code Execution vulnerability associated with Spring Framework used in SAP Commerce (3171258): Symptom: SAP Commerce uses a version of Spring Framework which has Remote Code Execution vulnerability. Reason and Prerequisites: This vulnerability affects all SAP Commerce web applications that use Spring MVC. This includes HAC, Backoffice, SmartEdit, and Accelerators. Solution: SAP Commerce fixes this vulnerability by updating to the latest version of Spring libraries. These Spring Framework versions are not affected by this vulnerability anymore. If you cannot upgrade to the latest SAP Commerce Cloud patch release yet, you can implement the workaround described. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Remote Code Execution vulnerability associated with Spring Framework used in SAP Customer Profitability Analytics (3189635): Symptom: SAP Customer Profitability Analytics uses a version of Spring Framework which has Remote Code Execution vulnerability. Reason and Prerequisites: SAP Customer Profitability Analytics makes use of a version of the Spring framework that is vulnerable to Spring4Shell attacks. Solution: The Spring framework has been updated to a patched version, which isn’t vulnerable to Spring4Shell attacks. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Cross-Site Scripting (XSS) vulnerability in administration UI of SAP Webdispatcher and SAP Netweaver AS for ABAP and Java (ICM) (3145046): It patches a Cross-Site Scripting vulnerability in the administration UI of ICM in SAP Application Server ABAP/Java, and in the administration UI for SAP Web Dispatcher (stand-alone and (A)SCS instance embedded). SAP and the Onapsis Research Labs (ORL) found a high impact on a system’s confidentiality, integrity, and availability when exploiting the vulnerability. The only thing that prevents this vulnerability from being tagged with a higher CVSS is the fact that an attacker must entice a victim to log on to the administration UI using a browser and that the attack is highly complex. CVSS v3 Base Score: 8,3 / 10 (CVE-2022-27656).
- Central Management Server Information Disclosure in Business Intelligence Update (2998510): This note patches a problem that exists during an upgrade of SAP BusinessObjects Enterprise. The upgrade exposes information in the Sysmon event logs that could be used in follow-up attacks with high impact on systems’ confidentiality, integrity, and availability. CVSS v3 Base Score: 7.8 / 10 (CVE-2022-28214).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for May:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-mayo-2022
Other references, from SAP and Onapsis (May):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
Resources affected
- SAP Business One Cloud, versión 1.1;
- SAP BusinessObjects Business Intelligence Platform, versiones 420 y 430;
- SAP Commerce, versiones 1905, 2005, 2105 y 2011;
- SAP Customer Profitability Analytics, versión 2;
- SAP Employee Self Service (Fiori My Leave Request), versión 605;
- SAP Host Agent, versión 7.22.
- SAP NetWeaver Application Server para ABAP y ABAP Platform, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 787 y 788;
- SAP Netweaver AS para ABAP y Java (ICM), versiones KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC, 7.22, 7.22EXT, 7.49, 7.53, 8.04, KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87 y 8.04;
- SAP Webdispatcher, versiones 7.22EXT, 7.49, 7.53, 7.77, 7.81, 7.83 y 7.85.