Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
April 2021 notes
Summary and highlights of the month
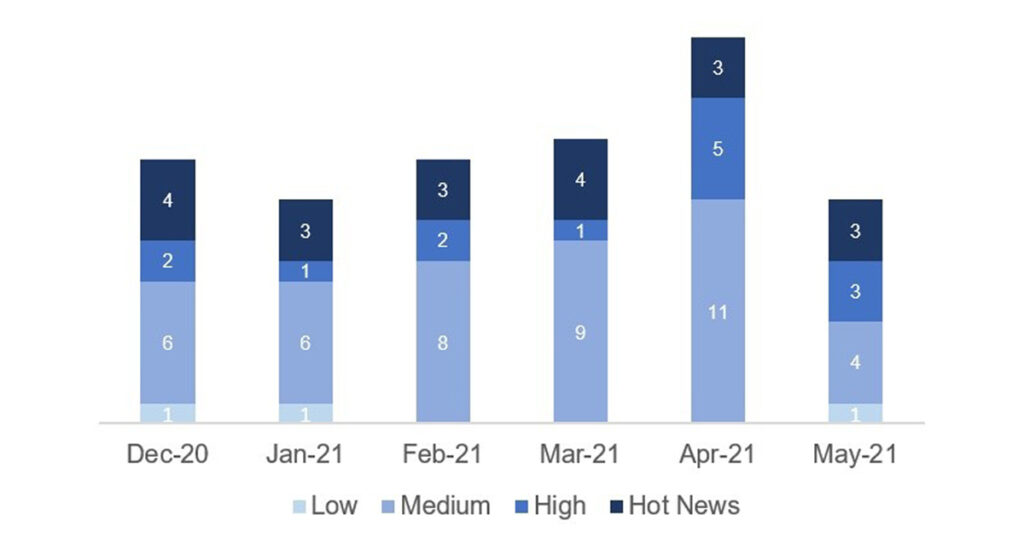
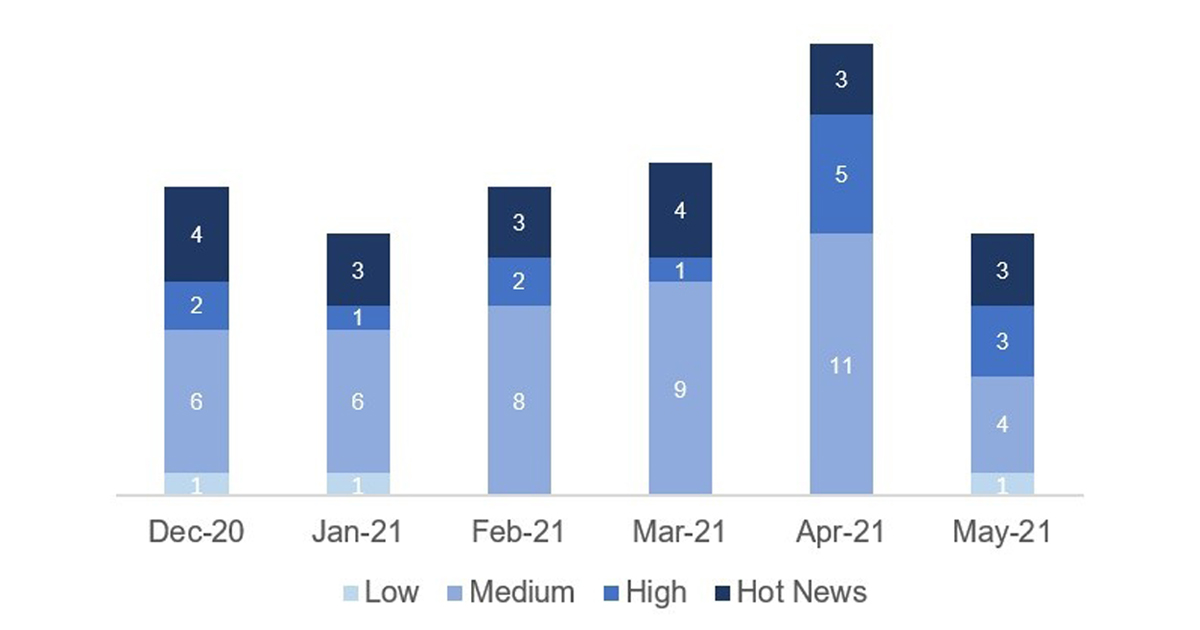
The total number of notes/patches has decreased compared to last month. Despite this decrease in the total number of notes, the number of Hot News has remained the same, with 3 Hot News notes last month compared to 3 in May. On the other hand, it should be noted that the number of highly critical notes decreased from 5 to 3 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 6 scores (all those with a CVSS of 7 or higher).
We have a total of 14 notes for the whole month, 9 less than last April (11 from Patch Tuesday, 6 new and 5 updates, being 8 less than last month).
This month there are 3 Hot News, all updates, which stand out for their high CVVS. One of them is the recurring update for the SAP Business Client with Chromium. In addition we will review in detail 3 of the total of 3 high notes (those of CVSS greater than or equal to 7) where this month we locate the three as new notes.
- The most critical note of the month (with CVSS 10) is an update. This note is the usual “Browser Control Google Chromium Delivered with SAP Business Client”.
- Next in criticality (CVSS 9.9) are also two updates. One for Remote Code Execution vulnerability in Source Rules of SAP Commerce and another for Code Injection affecting SAP Business Warehouse and SAP BW/4HANA.
- From there, we find the 3 notes of high priority, being the most relevant with a CVSS of 8.2 a new note of Code Injection vulnerability that affects SAP NetWeaver AS ABAP. The rest (8) are of medium and low level, and we will not see them in detail.
- This month the most predominant types are “Information Disclosure” (4/14 and 2*/11 in patch day) and “Code Injection” (2/14 and 2*/11 in patch day).
In the graph (post May 2021 from SAP) we can see the classification of the May notes in addition to the evolution and classification of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
 Full details
Full details
The full details of the most relevant notes are as follows:
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): SAP Business Client now includes Chromium version 90.0.4430.93. Compared to the last supported Chromium version (89.0.4389.90), this new version fixes 63 security issues in total, including 22 High Priority patches that are based on externally reported issues. CVSS v3 Base Score: 10 / 10.
- Update – Remote Code Execution vulnerability in Source Rules of SAP Commerce (3040210): It was updated only 6 days after its initial release on April Patch Day. The note provides a patch for the rules engine in SAP Commerce on-premise and SAP Commerce Cloud. Unfortunately, it is impossible to identify the reason for the update but one can assume that it’s nothing worth mentioning as SAP normally will introduce updated notes with some kind of information about the update reason when more important. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-27602).
- Update – Code Injection in SAP Business Warehouse and SAP BW/4HANA (2999854): The note that fixes critical Code Injection vulnerabilities in SAP Business Warehouse and SAP BW/4HANA now provides additional correction instructions for SAP BW 7.40 SP3 and SP4. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-21466).
- Code Injection vulnerability in SAP NetWeaver AS ABAP (3046610): It affects SAP NetWeaver AS ABAP up to version 7.31. These versions include a SAP Basis program that allows the injection of malicious code and thus enables an attacker who has access to the local SAP system to read and overwrite data, as well as initiate a Denial-of-Service attack. Only the need for local access, together with the fact that an attacker requires high privileges to execute the program, prevents this vulnerability from being tagged with a CVSS score of 10. CVSS v3 Base Score: 8.2 / 10 (CVE-2021-27611).
- Multiple vulnerabilities in SAP Business One, version for SAP HANA (Business-One-Hana-Chef-Cookbook) (3049661): The issues in the cookbook for SAP B1 on SAP HANA are patched with SAP Security Note #3049661. This note can lead to the injection of malicious code allowing an attacker to control the behavior of the entire application. CVSS v3 Base Score: 7.8 / 10 (CVE-2021-27616).
- Information Disclosure in SAP Business One (Chef business-one-cookbook) (3049755): SAP provides two Chef Cookbooks for automated SAP Business One test system installations on GitHub—one for SAP B1 on MS SQL Server and one for SAP B1 on SAP HANA. The vulnerability in the first Cookbook is described in this note and can lead to an Information Disclosure on payroll data. CVSS v3 Base Score: 7.8 / 10 (CVE-2021-27613).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for May:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-mayo-2021
Other references, from SAP and Onapsis (May):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=576094655
https://onapsis.com/blog/sap-security-patch-day-may-2021
Resources affected
- SAP Business Client, versión 6.5;
- SAP Business One (Cookbooks), versión 0.1.9;
- SAP Business One para SAP HANA (Cookbooks), versiones 0.1.6, 0.1.7 y 0.1.9;
- SAP Business Warehouse, versiones 700, 701, 702, 711, 730, 731, 740, 750 y 782;
- SAP BW4HANA, versiones 100 y 200;
- SAP Commerce, versiones 1808, 1811, 1905, 2005 y 2011;
- SAP Focused RUN, versiones 200 y 300;
- SAP GUI for Windows, versiones 7.60 y 7.70;
- SAP NetWeaver:
- Application Server Java (Applications basadas en Web Dynpro Java), versiones 7.00, 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- AS ABAP, versiones 700, 701, 702, 730 y 731;
- SAP Process Integration (Integration Builder Framework), versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50.