Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
February 2023 notes
Summary and highlights of the month
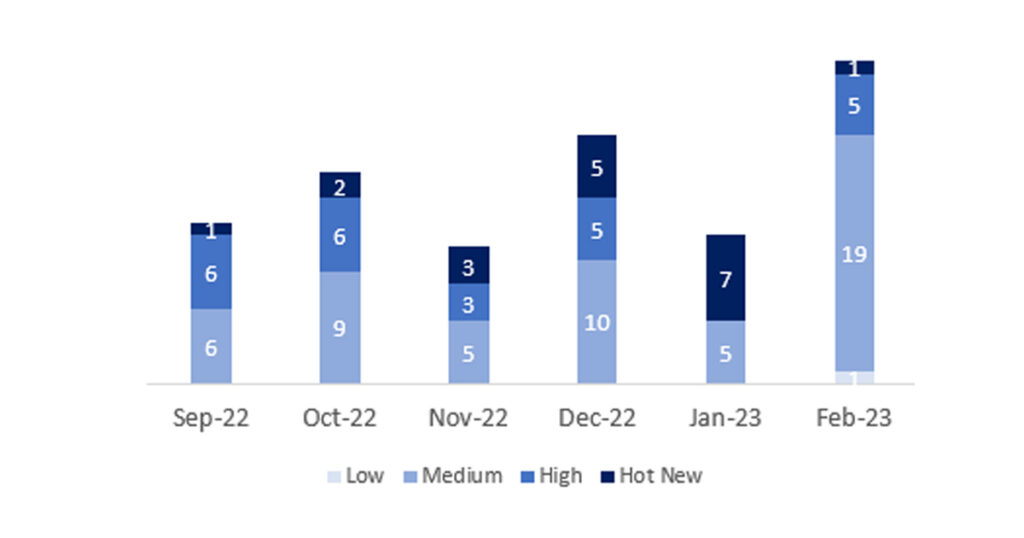
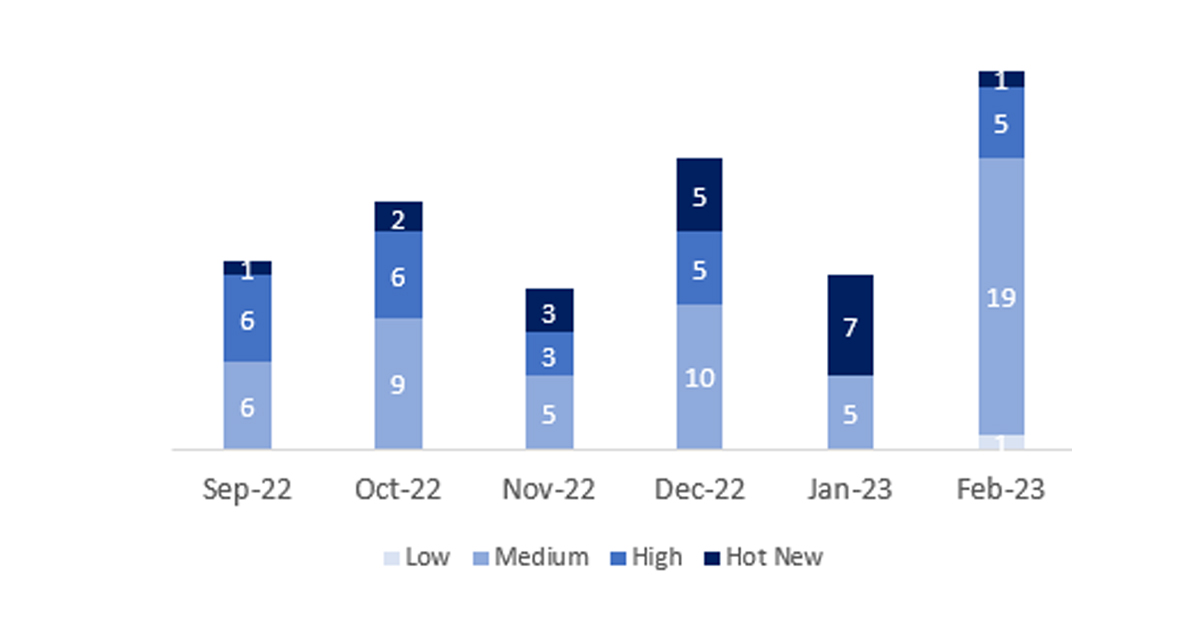
The total number of notes/patches was 26, 14 more than last month. The number of Hot News decreased from 7 to 1 this month. On the other hand, it is worth noting that the number of high criticality notes increases from 0 to 5. As usual we will leave the medium and low notes unchecked this month, but we will give details of a total of 7 notes (all those with a CVSS of 7 or higher).
We have a total of 26 scores for the whole month (the 26 from Patch Tuesday, 21 new and 5 updates, that’s 14 more scores than last month).
We will review in detail the 5 high notes, of which 3 are new and 2 are updates and the HotNews, which is an update:
- The most critical note of the month (with CVSS 10) is the usual note related to “Google Chromium”.
- The next in criticality (with CVSS 8.8) are 2 high notes, one related to “Privilege Escalation vulnerability in SAP Start Service” and the other related to “Code Injection vulnerability in SAP BASIS“, this last note is an update of a note released on Patch Day December 2022.
- The next 2 criticality scores (with CVSS 8.5) are 2 high scores, one related to “Information disclosure vulnerability in SAP BusinessObjects Business Intelligence platform” and the other one related to “Privilege escalation vulnerability in SAP Business Planning and Consolidation“, this last score is an update of a score released in the Patch Day December 2022.
- next criticality note (with CVSS 8.4) is a high note, related to “Unrestricted Upload of File in SAP BusinessObjects Business Intelligence Platform (CMC)“.
- This month the most predominant type is “Cross-Site Scripting (XSS)” (10/26 on patch day).
In the graph (post February 2023 from SAP) we can see the ranking of the February notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Privilege Escalation vulnerability in SAP Start Service (3285757): An attacker authenticated as a non-admin user with local access to a server port assigned to the SAP Host Agent Service can submit a specially crafted webservice request with an operating system command which will be executed with administrator privileges. The OS command can read or modify any user or system data and can make the system unavailable. CVSS v3 Base Score: 8,8 / 10 [CVE-2023-24523].
- Update – Code Injection vulnerability in SAP BASIS (3268172): Due to unrestricted scope of the RFC function module, SAP BASIS allows an authenticated non-administrator attacker to access a system class and execute any of its public methods with parameters provided by the attacker. On successful exploitation the attacker can have full control of the system to which the class belongs, causing high impact on integrity of the application. The update adds that this note is also relevant if you do not use a HANA database on your system. The correction instruction in this note simply deactivates the obsolete but critical code.CVSS v3 Base Score: 8,8 / 10 [CVE-2022-41264].
- Information disclosure vulnerability in SAP BusinessObjects Business Intelligence platform (3263135): SAP BusinessObjects Business Intelligence platform allows an authenticated attacker to access sensitive information which is otherwise restricted. On successful exploitation, there could be a high impact on confidentiality and limited impact on integrity of the application. CVSS v3 Base Score: 8,5 / 10 [CVE-2023-0020].
- Update – Privilege escalation vulnerability in SAP Business Planning and Consolidation (3271091): In some SAP standard roles in SAP Business Planning and Consolidation, a transaction code reserved for customer is used. By implementing such transaction code, a malicious user may execute unauthorized transaction functionality. Under specific circumstances, a successful attack could enable an adversary to escalate their privileges to be able to read, change or delete system data. The update simply adds minor text changes. No changes requiring customer intervention have been made. CVSS v3 Base Score: 8,5 / 10 [CVE-2022-41268].
- Unrestricted Upload of File in SAP BusinessObjects Business Intelligence Platform (CMC) (3256787): SAP BusinessObjects Business Intelligence Platform (CMC) allows an authenticated admin user to upload malicious code that can be executed by the application over the network. On successful exploitation, attacker can perform operations that may completely compromise the application causing high impact on confidentiality, integrity and availability of the application. The note contains a workaround. CVSS v3 Base Score: 8,4 / 10 [CVE-2023-24530].
Reference links
Other references, from SAP and Onapsis (February):
SAP Patch Day: February 2023 (onapsis.com)
Resources affected
- SAP Business Client, Versions – 6.5, 7.0, 7.70
- SAP Business Planning and Consolidation,Versions–SAP_BW 750, 751, 752, 753, 754, 755, 756, 757, DWCORE 200, 300, CPMBPC 810
- SAP BusinessObjects Business Intelligence platform (Analysis edition for OLAP), Versions -420, 430
- SAP BusinessObjects Business Intelligence platform (CMC), Versions -420, 430
- SAP Host Agent Service, Versions -7.21, 7.22
- SAPBASIS, Versions –731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 789, 790, 791