Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
April 2022 notes
Summary and highlights of the month
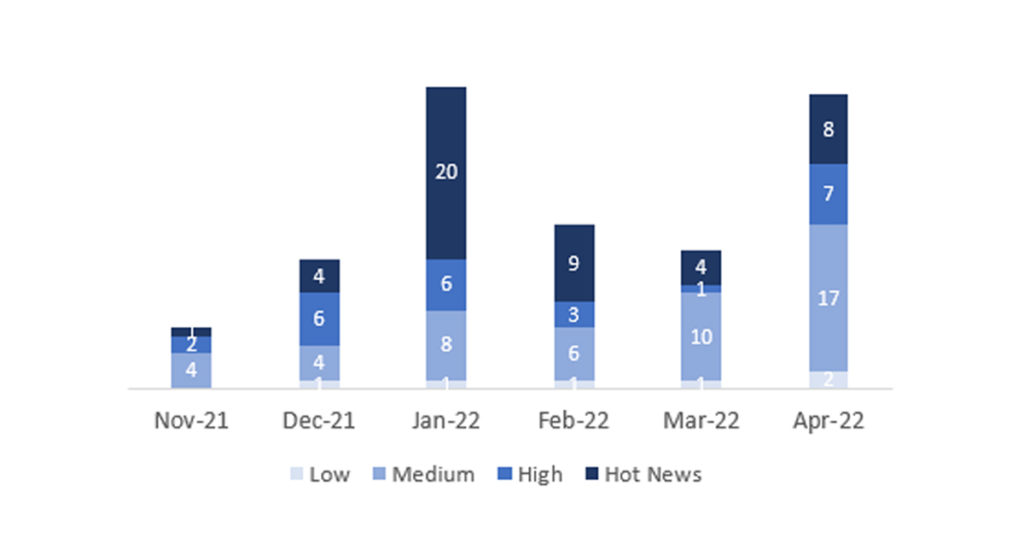
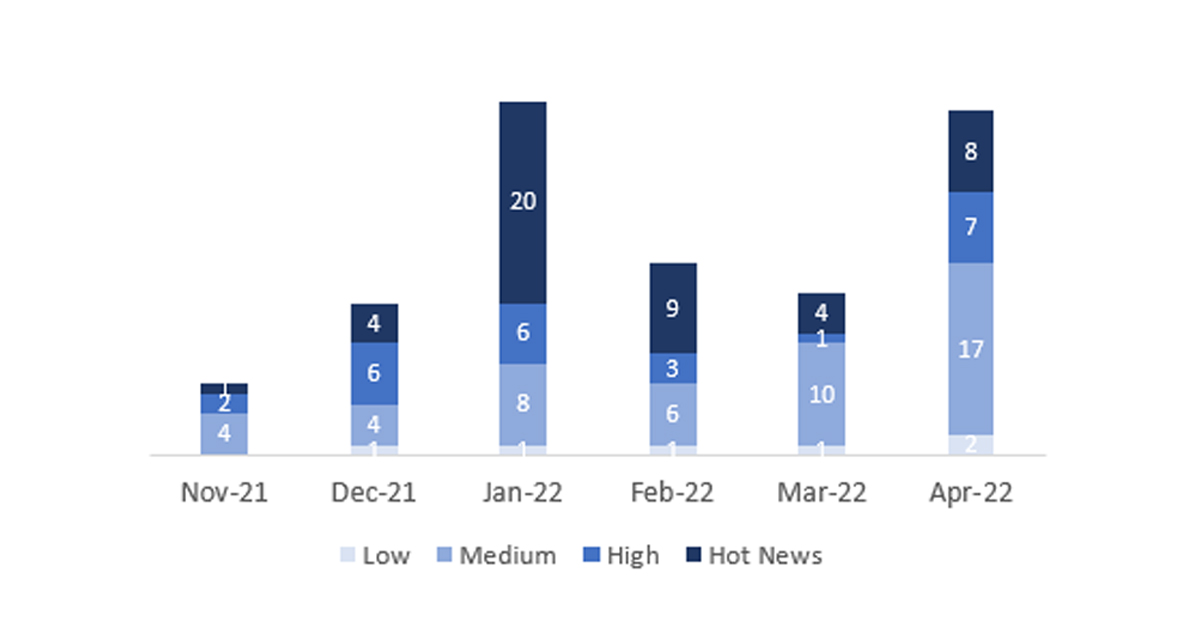
The total number of notes/patches has increased compared to last month. In addition to this increase in the total number of notes, the number of Hot News is also reduced, with 4 notes last month compared to 8 in April. On the other hand, it should be noted that the number of high criticality notes increased from 1 to 7 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 15 scores (all those with a CVSS of 7 or higher).
We have a total of 35 notes for the whole month, 18 more than last March (33 from Patch Tuesday, 23 new and 10 updates, being 17 more than last month).
We have 8 critical notes (Hot News), 4 new and 4 updates, in this month, which stand out for their high CVVS. We will also review in detail 7 of the total of 7 high notes (those with CVSS greater than or equal to 7), which this month are 3 updates and 4 new notes.
- The most critical notes of the month (with CVSS 10) are 2. On the one hand the usual note of Google Chromium and, on the other hand, the other note with this CVSS would affect SAP NetWeaver, SAP Content Server and SAP Web Dispatcher.
- Next in criticality (CVSS 9.9) is a “Code Injection Vulnerability” note affecting SAP Manufacturing Integration and Intelligence.
- From there, we located 4 notes of very high criticality (CVSS 9.8), all related to “Remote Code Execution” and that would be affecting Spring Framework, SAP HANA Extended Application Services, SAP Customer Checkout and SAP Powerdesigner Web Portal.
- Finally, in relation to Hot News, we have one last criticality (CVSS 9.1), which would be of the type “Code injection vulnerability” and would be related to SAP Manufacturing Integration and Intelligence.
- In relation to the high level notes, there would be a total of 7, including one with CVSS 8.9 and two others with 8.2, related to HTTP Request Smuggling, Cross-Site Scripting (XSS) and CSRF token visible. The rest (18) are medium and low level, and we will not look at them in detail.
- This month the most predominant note types are “Cross-Site Scripting (XSS)”, “Remote Code Injection” “Information Disclosure” and “Denial of Service”, all with 4/33 and 4/35 on patch day.
In the graph (post April 2022 by SAP) we can see the ranking of the April notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Update – Request smuggling and request concatenation in SAP NetWeaver, SAP Content Server and SAP Web Dispatcher (3123396): This security note will be related to the vulnerability of SAP NetWeaver Application Server ABAP, SAP NetWeaver Application Server Java, ABAP Platform, SAP Content Server 7.53 and SAP Web Dispatcher for request smuggling and request concatenation. Due to that, an unauthenticated attacker can prepend a victim’s request with arbitrary data. This way, the attacker can execute functions impersonating the victim or poison intermediary Web caches. A successful attack could result in complete compromise of Confidentiality, Integrity and Availability of the system. The correction requires patching both SAP Web Dispatcher and SAP Kernel, where the patch solves the security issue completely. CVSS v3 Base Score: 10 / 10 (CVE-2022-22536).
- Update – Code injection vulnerability in SAP Manufacturing Integration and Intelligence (3022622): This security note is related to SAP MII allows users to create dashboards and save them as JSP through the SSCE (Self Service Composition Environment). An attacker can intercept a request to the server, inject malicious JSP code in the request and forward to server. When this dashboard is opened by users having atleast SAP_XMII_Developer role, malicious content in the dashboard gets executed, leading to remote code execution in the server, which allows privilege escalation. The update indicates that this solution is now obsolete and for the complete fix please implement the SAP security note 3158613 . CVSS v3 Base Score: 9,9 / 10 (CVE-2021-21480).
- Central Security Note for Remote Code Execution vulnerability associated with Spring Framework (3170990): This security note will be the central document to consolidate all SAP Security Notes released for the Remote Code Execution vulnerability associated with Spring Framework (CVE-2022-22965).. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Remote Code Execution vulnerability associated with Spring Framework used in SAP HANA Extended Application Services (3189428): SAP HANA Extended Application Services uses a version of Spring Framework which has Remote Code Execution vulnerability (CVE-2022-22965). The solution would be to update SAP HANA XS, advanced model to version 1.0.145 or greater. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Remote Code Execution vulnerability associated with Spring Framework used in SAP Customer Checkout (3187290): SAP Customer Checkout uses a version of Spring Framework which has Remote Code Execution vulnerability (CVE-2022-22965). To prevent exploiting this vulnerability, update to one of the following versions mentioned below which uses a newer version of Spring Framework:SAP Customer Checkout 2.0 FP13 PL01 or higher, SAP Customer Checkout 2.0 FP12 PL10 or higher, SAP Customer Checkout 2.0 FP11 PL09 or higher . CVSS v3 Base Score: 9.8 / 10 (CVE-2022-22965).
- Remote Code Execution vulnerability associated with Spring Framework used in PowerDesigner Web (upto including 16.7 SP05 PL01) (3189429): PowerDesigner Web uses a version of Spring Framework which has Remote Code Execution vulnerability (CVE-2022-22965).. CVSS v3 Base Score: 9,8 / 10 (CVE-2022-22965).
- Update – Code injection vulnerability in SAP Manufacturing Integration and Intelligence (3158613): This security note is an update to the security note 3022622. Fix provided in the security note 3022622 is no longer valid. SAP MII allows users to create dashboards and save them as JSP through the SSCE(Self Service Composition Environment). An attacker can intercept a request to the server, inject malicious JSP code in the request and forward to server. When this dashboard is opened by users having at least SAP_XMII_Developer role, malicious content in the dashboard gets executed, leading to remote code execution in the server, which allows privilege escalation. Virus Scan interface has been implemented for all file upload/import scenarios within MII. A NetWeaver Administrator should configure and enable Virus Scan profile «XMII_VSI» which will then be used by MII. MII will support BLOCKEXTENSIONS and BLOCKMIMETYPES parameters provided by the profile. Using the virus scanner profile the NetWeaver Administrator can restrict the jsp creation by a XMII developer. . CVSS v3 Base Score: 9.1 / 10 (CVE-2021-21480).
- Update – HTTP Request Smuggling in SAP Web Dispatcher (3080567): An unauthenticated attacker can submit a malicious crafted request over a network to a front-end server which may, over a number of attempts, result in a back-end server confusing the boundaries of malicious and legitimate messages. This can result in the back-end server executing a malicious payload which can be used to read or modify any information on the server or consume server resources making it temporarily unavailable. Update your SAP Web Dispatcher. This correction is delivered with the kernel archive SAPWEBDISP.SAR. . CVSS v3 Base Score: 8.9 / 10 (CVE-2021-38162).
- CSRF token visible in one of the URL in SAP Business Intelligence Platform. (3130497): A CSRF token visible in the URL may possible lead to information disclosure vulnerability. This issue is fixed in the patches listed in the «Support Packages & Patches» section in the note. CVSS v3 Base Score: 8.2 / 10 (CVE-2022-27671).
- Update – Cross-Site Scripting (XSS) vulnerability in SAP Fiori launchpad (3149805): It patches a Cross-Site Scripting (XSS) vulnerability in SAP Fiori launchpad. Our research team detected that SAP Fiori launchpad allows an unauthenticated attacker to manipulate the SAP-theme URL parameter — and inject HTML code — and create a link over the network for a user to click on. Once the link is clicked, successful exploitation allows the attacker to hijack user privileges that can be used to exfiltrate data and craft a CSRF attack to manipulate data. This can limit the application’s confidentiality and pose risks to its integrity, as well as increase the likelihood of it being completely compromised. CVSS v3 Base Score: 8.2 / 10 (CVE-2022-26101).
- Update – HTTP Request Smuggling in SAP NetWeaver Application Server Java (3123427): SAP NetWeaver Application Server Java is vulnerable to HTTP request smuggling. Due to this vulnerability, an unauthenticated attacker could submit a crafted HTTP server request which triggers improper shared memory buffer handling, which could allow the malicious payload to be executed and hence execute functions that could be impersonating the victim or even steal the victim’s logon session. Besides, due to improper error handling, an attacker could submit multiple HTTP server requests resulting in errors, such that it consumes the memory buffer, which could result in system shutdown rendering the system unavailable. These vulnerabilities have been fixed by proper memory handling for HTTP pipeline requests. This correction is contained in all patch levels that are equal to or higher than the patch level listed in the «Support Package Patches» section of this SAP Note for the desired kernel release. CVSS v3 Base Score: 8.1 / 10 (CVE-2022-22532).
- Privilege escalation vulnerability in Apache Tomcat server component of SAP Commerce (3155609): SAP Commerce contains an Apache Tomcat application server that has a known vulnerability (CVE-2022-23181). Configuring Tomcat to use FileStore to persist sessions can expose your SAP Commerce system to a time of check, time of use vulnerability that allows attackers to perform actions with the privileges of the user that the Tomcat process is using. The following SAP Commerce patch releases contain the upgraded Tomcat:SAP Commerce Cloud Patch Release 2105.10, SAP Commerce Cloud Patch Release 2011.20, SAP Commerce Cloud Patch Release 2005.25, SAP Commerce Cloud Patch Release 1905.41 . CVSS v3 Base Score: 7.5 / 10 (CVE-2022-28772).
- Denial of service (DOS) in SAP Web Dispatcher and SAP Netweaver (Internet Communication Manager) (3111311): By overlong input values an attacker may force overwrite of the internal program stack in SAP Web Dispatcher or Internet Communication Manger, which makes these programs unavailable. Use SAPWEBDISP.SAR to patch standalone SAP Web Dispatcher. Use dw.sar or SAPEXE.SAR and SAPEXEDB.SAR to patch both ICM and embedded SAP Web Dispatcher. The correction is contained in all patch levels that are equal to or higher than the patch level listed in the «Support Package Patches» section of this SAP Note for the desired kernel release.. CVSS v3 Base Score: 7.0 / 10 (CVE-2022-28772).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for April:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-abril-2022
Other references, from SAP and Onapsis (April):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
https://onapsis.com/blog/sap-security-patch-day-april-2022-focus-spring4shell-and-sap-mii
Resources affected
- Fiori Launchpad, versions 754, 755 y 756;
- SAP 3D Visual Enterprise Viewer, version 9;
- SAP Business Client, version 6.5;
- SAP BusinessObjects Business Intelligence Platform (BI Workspace), version 420;
- SAP BusinessObjects Business Intelligence Platform, versions 420 y 430;
- SAP BusinessObjects Enterprise (Central Management Server), versions 420 y 430;
- SAP Commerce, versions 1905, 2005, 2105 y 2011;
- SAP Content Server, version 7.53;
- SAP Customer Checkout, version 2.0;
- SAP Customer Checkout_SVR, version 2.0;
- SAP Focused Run (Simple Diagnostics Agent), version 1.0;
- SAP HANA Extended Application Services, version 1;
- SAP Innovation Management, version 2;
- SAP Manufacturing Integration and Intelligence, versions 15.1, 15.2, 15.3 y 15.4;
- SAP NetWeaver:
- ABAP Server and ABAP Platform, versions 740, 750 y 787;
- Application Server for Java, version 7.50;
- Application Server Java, versions KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC, 7.22, 7.22EXT, 7.49, 7.53, KERNEL 7.22, 7.49 y 7.53;
- Enterprise Portal, versions 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- EP Web Page Composer, versions 7.20, 7.30, 7.31, 7.40 y 7.50;
- Internet Communication Manager, versions KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53, KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85 y 7.86;
- SAP NetWeaver and ABAP Platform, versions KERNEL 7.22, 8.04, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, KRNL64UC 8.04, 7.22, 7.22EXT, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT y 7.49;
- SAP NetWeaver Application Server ABAP and ABAP Platform, versions 700, 710, 711, 730, 731, 740 y 750-756;
- SAP NetWeaver Application Server for ABAP (Kernel) and ABAP Platform (Kernel), versions KERNEL 7.22, 8.04, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, KRNL64UC 8.04, 7.22, 7.22EXT, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT y 7.49;
- SAP SQL Anywhere Server, version 17.0;
- SAP Web Dispatcher, versiones 7.22, 7.22EXT, 7.49, 7.53, 7.77, 7.81, 7.83, 7.85, 7.86 y 7.87;
- SAPS/4HANA(Supplier Factsheet and Enterprise Search for Business Partner, Supplier and Customer), versions 104, 105 y 106;
- SAPUI5 (vbm library), versions 750, 753, 754, 755 y 756;
- SAPUI5, versions: 750, 753, 754, 755, 756 y 200.