In many organizations, the plan to prevent data leaks can be summarized as “let’s implement a DLP.” Solutions such as Microsoft Purview, Zscaler, Netskope or other Data Loss Prevention technologies are essential, yes — but protecting data goes far beyond enabling DLP policies. It requires knowing who accesses it, from which device, in what context, how the user behaves and what happens when information leaves the corporate perimeter. That’s where a comprehensive strategy makes the difference.
Today, standards such as ISO/IEC 27001:2022 (Annex A: Control 8.12 – Data Leakage Prevention) include specific controls to implement a solid Data Leakage Prevention strategy. The key lies precisely in the word “strategy.” Technology is necessary, but not sufficient.
SASE and Zero Trust as the foundation for an effective DLP strategy
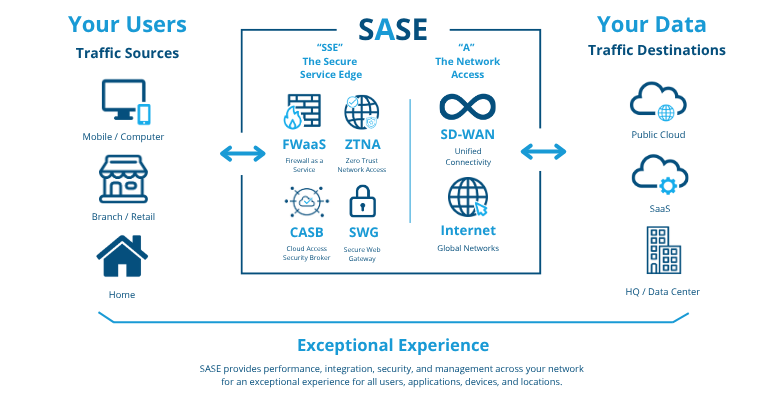
The most robust approach to data protection is SASE (Secure Access Service Edge): a framework that integrates networking and security, from SD-WAN to ZTNA, SWG, CASB, FWaaS, and DLP, to apply consistent policies across any user, device, or location.
A full SASE deployment may seem ambitious for some organizations; however, adopting it as a reference architecture delivers immediate benefits:
- Orchestrates identity, device, data, and threats under Zero Trust principles.
- Aligns existing solutions such as Entra, Intune, Purview, Defender, or IRM with network and cloud services.
- Enables a phased approach: visibility → conditional access → data protection → session control → network optimization.
- Reduces the risk surface, simplifies SOC operations, and creates a scalable foundation.
Even without a full SASE deployment, thinking in SASE terms helps build solid governance and a secure, consistent environment.
How Inprosec approaches Data Leakage Prevention
At Inprosec, leveraging our experience in Microsoft environments and leading technologies such as Zscaler — of which we are a partner — we help organizations design a 360° security framework to ensure data never leaves the corporate environment without proper safeguards (classification, encryption, DLP, and access control).
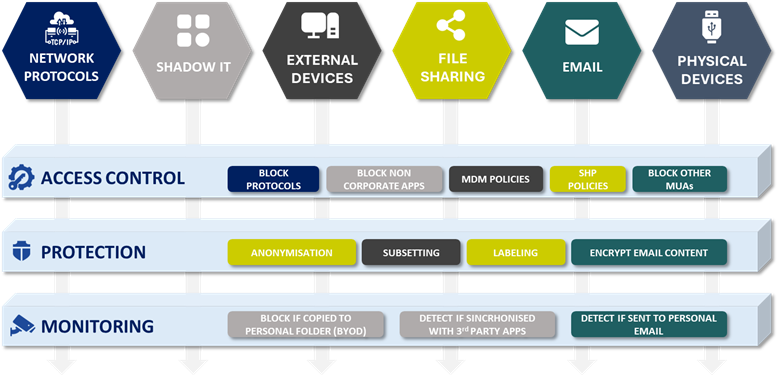
To achieve this, we analyze and control the main data exfiltration vectors, which are often repeated across organizations:
- Email: Still the main exfiltration channel and, in many companies, one of the least protected.
- Shadow IT: Unauthorized applications, services, and OAuth connections accessing corporate data without control.
- Network protocols: SMB, RDP, FTP/SFTP… still used by insiders and attackers to extract information.
- File sharing platforms: A critical area where operability and security must coexist. Public links, excessive permissions, or unauthorized repositories increase risk.
- External / unmanaged devices: Personal or non-corporate devices that fall outside IT control.
- Peripherals and removable media: USBs and external drives require controls such as whitelisting, selective blocking, and user awareness.
- Other alternative channels: AirDrop, Bluetooth, messaging, printers, etc., which can also be used for exfiltration.
Our 3-step DLP strategy
With this risk map, we build a strategy aligned with each company’s use cases:
- Control access (ZTNA): we define who accesses what information, when, from where, and with what permissions, applying conditional access and least privilege principles.
- Protect information: we implement data-level controls (encryption, tokenization, masking, anonymization, and labeling/IRM) so that protection travels with the content inside and outside the perimeter.
- Monitor and block: we monitor data flows (source, destination, type, and context), and upon detecting anomalous or malicious behavior, block the action and trigger automated response.
Practical example in Microsoft 365: “Highly Confidential” document
Access control (ZTNA and context)
- Restrict unauthorized clients: policies preventing sign-in from unsupported MUAs (e.g., Thunderbird, Gmail web with IMAP/POP), ensuring Purview safeguards are properly enforced. (Entra Conditional Access + Exchange Admin)
- Block non-corporate devices: allow access only from compliant devices; prevent “save as draft” from personal devices and subsequent downloads elsewhere. (Entra Conditional Access + Defender for Cloud Apps with session controls)
- BYOD under control: if personal devices are allowed, require Intune enrollment with MDM policies (corporate profile, encryption, compliance) and MAM (app protection) to isolate and secure corporate data.
Data protection (classification and encryption)
- Sensitivity labeling with Microsoft Purview Information Protection (formerly AIP) to classify content; apply encryption and persistent permissions (IRM/Azure RMS) and RBAC policies based on criticality.
- Mandatory encryption for the “Highly Confidential” label: restrict forwarding, printing, and downloading; set expiration and watermark when applicable.
Monitoring and blocking (DLP and response)
- External sharing monitoring with DLP in Purview: alert or block when the recipient is not on an allowed list; maintain blocklists for risky domains.
- Prevent DLP bypass: rules to block password-protected attachments (encrypted ZIP/PDF) or opaque, non-inspectable content; enforce use of corporate encryption (IRM) instead of ad-hoc encryption (7Zip, WinRar, etc.).
- Compliance action: when risk or policy dictates, configure Purview policy in “Block” mode and trigger an alert to the SOC; maintain traceability for eDiscovery and auditing.
This approach combines contextual access, protection that travels with the file, and outbound controls across all channels, minimizing both human error and intentional exfiltration.
Conclusion: a strategic DLP framework is key to minimizing data leaks
With this strategic approach, we protect information throughout its lifecycle, strengthen compliance, and reduce real leakage risk. The result is a more secure, manageable, and scalable environment for both our clients and Inprosec.
If your organization wants to move toward a solid, Zero Trust-based DLP strategy with Microsoft 365, Inprosec can help. Contact us here and take the next step toward comprehensive data protection.