Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
October 2025 Notes
Monthly Summary and Highlights
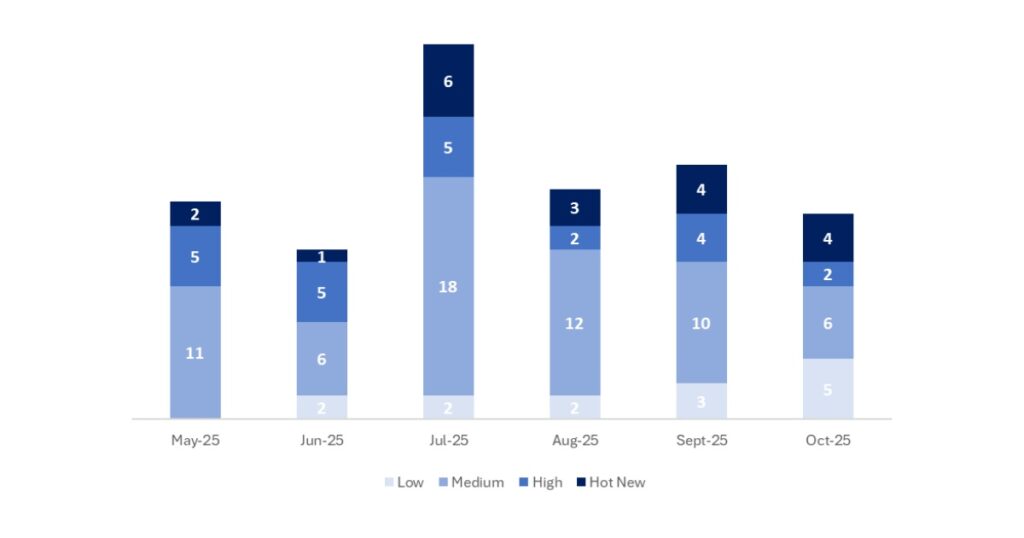
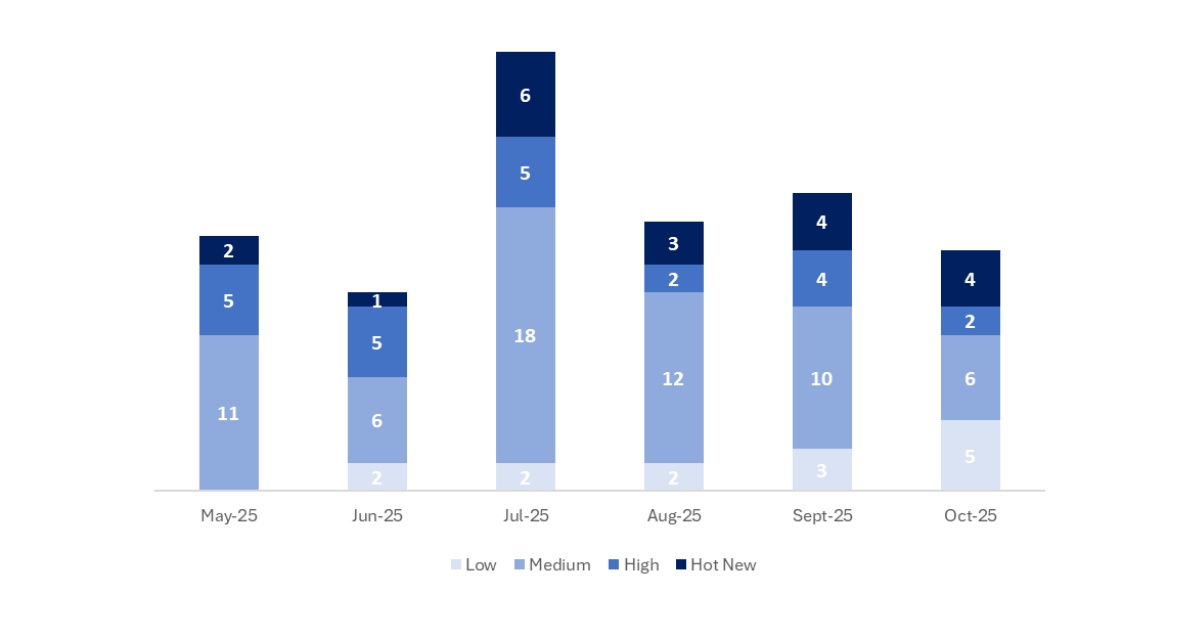
This month, the total number of notes is 17, which is 4 fewer than the previous month. We have 4 Hot News this month, the same as in the previous period. As for high-severity notes, there are 2, which is two fewer than last month. Medium and low-severity notes will not be reviewed, so we will provide details on a total of 6 notes (all those with a CVSS score of 7 or higher).
We have a total of 17 notes for the entire month (13 new and 4 updates to notes published in previous months).
We will review in detail a total of 6 notes, all of them classified as high severity and Hot News:
-
The two highest-severity notes of the month (CVSS 10) are Hot News with the maximum criticality score. One of the notes is new, and the other is an update to one published last month. They are related to “Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java” and “Insecure Deserialization vulnerability in SAP NetWeaver (RMI-P4)”, respectively.
-
The next one in severity (CVSS 9.8) is another Hot News related to “Directory Traversal vulnerability in SAP Print Service”.
-
The next one in severity (CVSS 9.0) is the last Hot News of the month and is an update to one published in March 2023. It is related to “Unrestricted File Upload Vulnerability in SAP Supplier Relationship Management”.
-
The next note in severity (CVSS 7.5) is the first high-severity note, and it concerns “Denial of Service (DoS) in SAP Commerce Cloud (Search and Navigation)”.
-
Finally, the last note we will analyze, with a severity of (CVSS 7.1), is related to “Security Misconfiguration vulnerability in SAP Data Hub Integration Suite”.
-
This month, the most predominant types have been “Directory Traversal vulnerability” and “Insecure Deserialization vulnerability” (2/13 on the patch day for both).
In the chart below, we can see the classification of the October notes, as well as the evolution and classification for the previous 5 months (only Security Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
-
Insecure Deserialization vulnerability in SAP Netweaver (RMI-P4) (update) (3634501): Due to a deserialization vulnerability in SAP NetWeaver (RMI-P4), an unauthenticated attacker could exploit the system by sending malicious payloads to an open port, potentially leading to arbitrary OS command execution and a full compromise of confidentiality, integrity, and availability. The issue has been fixed by updating the affected P4-Lib component to enforce secure deserialization handling and restrict untrusted Java objects via the RMI-P4 module. SAP recommends implementing the patches listed in the “Support Packages & Patches” section and ensuring the Java Virtual Machine version is higher than Java 8u121 (refer to Note 2695197), while also reviewing Note 1974464 to avoid incompatibilities. For additional information, see Note 3637718 and, for further hardening, apply Note 3660659. If patching is not immediately possible, a temporary workaround involves isolating the system at the network level so that P4 and P4S ports are not accessible from insecure networks, ensuring these ports are reachable only from trusted systems through firewall rules or IP filtering. Once the patch is applied, the workaround can be rolled back. CVSS v3 Base Score 10/ 10 [CVE-2025-42944]
-
Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java (3660659): SAP NetWeaver AS Java is vulnerable to remote code execution due to insecure deserialization of JDK and third-party classes, where specially crafted input could be deserialized by the AS Java runtime. Although no new CVE was issued, this advisory serves as a hardening measure linked to [CVE-2025-42944] with a CVSS score of 10.0 (Critical). The issue is resolved by blocking vulnerable JDK and third-party classes through a configuration-based patch that prevents insecure deserialization and enhances security for systems affected by the RMI/P4 vulnerability (SAP Note 3634501). To apply the fix, ensure a Java Virtual Machine version higher than Java 8u121 is installed (per KBA 2695197), and that the ‘
bootstrap.properties'file includes the property ‘element.resynch=DETECT'(SAP Note 710663). SAP also recommends checking Note 1974464 for compatibility guidance before applying the update. For more information, refer to FAQ KBA 3663688. A workaround may be considered depending on system applicability, though applying the patch remains the recommended permanent solution. CVSS v3 Base Score 10/ 10 [CVE-2025-42944] -
Directory Traversal vulnerability in SAP Print Service (3630595): SAP Print Service (SAPSprint) is affected by a path traversal vulnerability due to insufficient validation of user-provided path information. An unauthenticated attacker could exploit this flaw to traverse directories and overwrite system files, leading to a high impact on the confidentiality, integrity, and availability of the application (CVE-2025-42937). The issue has been resolved by introducing proper validation of path inputs within SAPSprint. Users are advised to implement the patches listed in the “Support Packages & Patches” section of this SAP Security Note. For further details, refer to FAQ Note 3636888. No workaround is available for this vulnerability. CVSS v3 Base Score 9,8/ 10 [CVE-2025-42937]
-
Unrestricted File Upload Vulnerability in SAP Supplier Relationship Management (3647332): SAP Supplier Relationship Management is affected by an unrestricted file upload vulnerability caused by missing verification of file type or content. An authenticated attacker could exploit this flaw to upload arbitrary files, including executables that might be downloaded and executed by users, potentially leading to malware infections. Successful exploitation could result in a high impact on the confidentiality, integrity, and availability of the application (CVE-2025-42910). The issue has been resolved by implementing proper validation of MIME types and file extensions. Users should apply the Correction Instructions or Support Packages referenced in this SAP Security Note. No workaround is available. CVSS v3 Base Score 9,0/ 10 [CVE-2025-42910]
-
Denial of service (DOS) in SAP Commerce Cloud (Search and Navigation) (3664466): SAP Commerce Cloud Search and Navigation is vulnerable to a denial-of-service (DoS) attack caused by a flaw in the HTTP/2 protocol within the Jetty library. A malicious client could send crafted requests that force the server to reset streams repeatedly, consuming excessive resources and leading to service disruption. This issue has a high impact on availability but does not affect confidentiality or integrity (CVE-2025-5115). The vulnerability is resolved by upgrading the Jetty http2-common library to the latest version, included in SAP Commerce Cloud Patch Releases 2211-jdk21.2, 2211.45, and 2205.43. Customers should install these or later patches, rebuild, and redeploy their SAP Commerce environments according to the deployment instructions provided in the SAP Support Portal. CVSS v3 Base Score 7,5/ 10 [CVE-2025-5115]
-
Security Misconfiguration vulnerability in SAP Data Hub Integration Suite (3658838): SAP Datahub Suite is affected by a vulnerability due to the use of Apache CXF 3.5.1 libraries with JMS/JNDI configurations, allowing an unauthenticated attacker to inject malicious RMI/LDAP endpoints (CVE-2025-48913). This could result in remote code execution, leading to a high impact on the confidentiality, integrity, and availability of the application. The issue is resolved by upgrading Apache CXF to version 3.6.8, which includes secure versions of multiple CXF components such as cxf-core, cxf-rt-bindings-soap, and cxf-rt-frontend-jaxws. Customers are advised to apply the SAP Commerce Integration Extension Pack Patch Release 2205.17, which contains the updated, non-vulnerable libraries. CVSS v3 Base Score 7,1/ 10 [CVE-2025-48913]
Reference links
Other references, from SAP and Onapsis (october):
SAP Security Patch Day – October 2025
SAP Patch Day: October 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
-
SAP NetWeaver AS Java – SERVERCORE 7.50, J2EE-APPS 7.50, ADSSAP 7.50, WD-RUNTIME 7.50
-
SAP NetWeaver AS ABAP – SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 816
-
SAP NetWeaver (Generic / RMI-P4 / Service Data Download / Background Processing) – SAP_ABA 700–75I, ST-PI 2008_1_700, 2008_1_710, 740
-
SAP NetWeaver Kernel Components – KRNL64UC 7.22, 7.22EXT, KRNL64NUC 7.22, 7.22EXT, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 9.12, 9.14, 9.15, 9.16
-
SAP NetWeaver Application Server ABAP (SAP GUI for HTML) – KRNL64UC 7.53, KERNEL 7.53, 7.54, 7.77, 7.89, 7.93, 9.12, 9.14
-
SAP Print Service – SAPSPRINT 8.00, 8.10
-
SAP S/4HANA (Private Cloud or On-Premise) – S4CORE 102, 103, 104, 105, 106, 107, 108, 109
-
SAP S/4HANA (Manage Processing Rules – For Bank Statements) – S4CORE 104–109
-
SAP S/4HANA (Manage Central Purchase Contract) – S4CORE 106–108
-
SAP S/4HANA (Fiori App – Manage Payment Blocks) – S4CORE 107–108
-
SAP Business One (SLD) – B1_ON_HANA 10.0, SAP-M-BO 10.0
-
SAP Landscape Transformation Replication Server – DMIS 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2011_1_752, 2020
-
SAP HCM (My Timesheet Fiori 2.0 Application) – GBX01HR5 605
-
SAP HCM (Approve Timesheets Fiori 2.0 Application) – GBX01HR5 605
-
SAP Fiori (Launchpad) – SAP_UI 754
-
SAP Fiori App (F4044 Manage Work Center Groups) – UIS4HOP1 600, 700, 800, 900
-
SAP Commerce Cloud – HY_COM 2205, COM_CLOUD 2211, 2211-JDK21
-
SAP Data Hub Integration Suite – CX_DATAHUB_INT_PACK 2205
-
SAP Datahub – HY_DHUB 2205, DHUB_CLOUD 2211
-
SAP BusinessObjects Business Intelligence Platform – ENTERPRISE 430, 2025, 2027
-
SAP BusinessObjects (Web Intelligence and Platform Search) – ENTERPRISE 430, 2025, 2027
-
SAP Supplier Relationship Management (SRM) – SRM_SERVER 700, 701, 702, 713, 714
-
SAP Supplier Relationship Management (Unrestricted File Upload) – SRMNXP01 100, 150
-
SAP Financial Service Claims Management – INSURANCE 803, 804, 805, 806, S4CEXT 107, 108, 109
-
SAP Cloud Appliance Library Appliances – TITANIUM_WEBAPP 4.0
-
SAP Business Planning and Consolidation – BPC4HANA 200, 300, SAP_BW 750–758, 816, 914, CPMBPC 810