Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
November 2025 Notes
Summary and Highlights of the Month
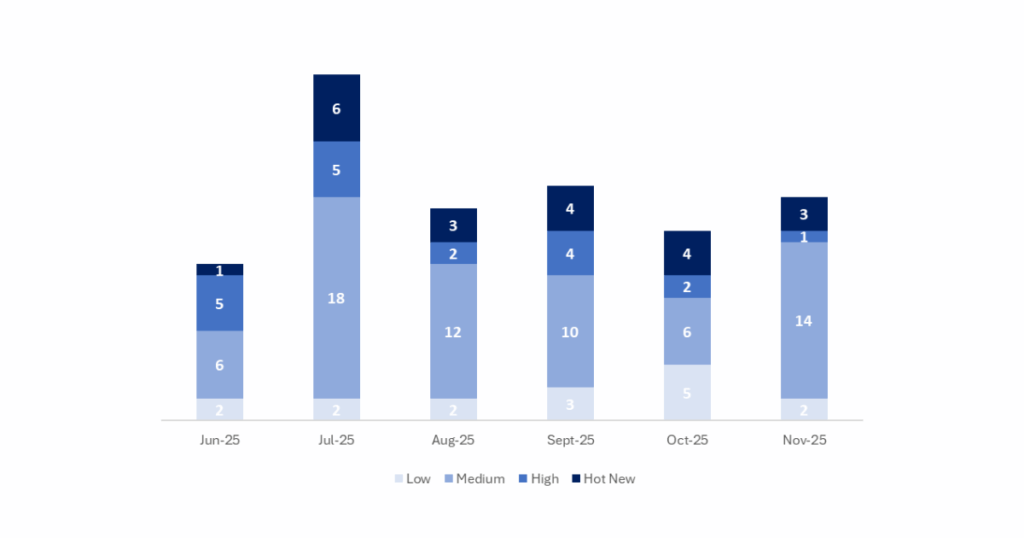
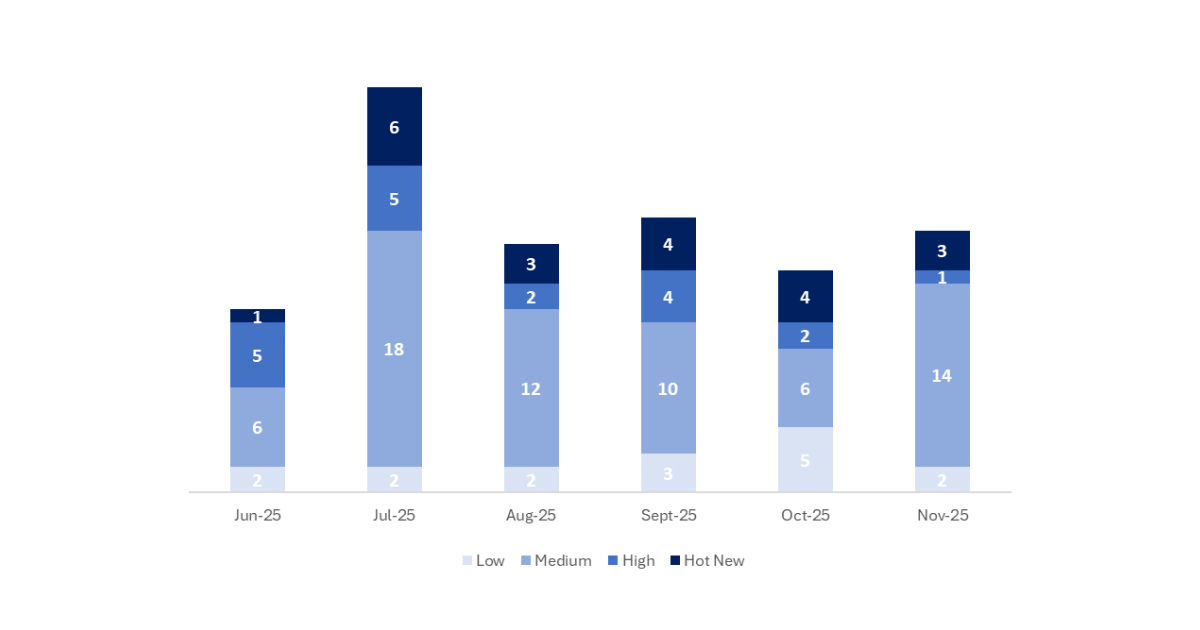
This month, the total number of notes was 20, which is 2 more than in the previous month. We had 3 Hot News this month, one less than in the previous period. As for high-criticality notes, there is 1, which is also one less than last month. Medium and low notes will not be reviewed, so we will provide details for a total of 4 notes (all those with a CVSS of 7 or higher).
We have a total of 20 notes for the entire month (18 new and 2 updates of notes published in previous months).
We will review in detail a total of 4 notes, all of them high-criticality and Hot News:
-
The 2 most critical notes of the month (CVSS 10) are Hot News with the maximum severity score. One of the notes is new, and the other is an update of one published last month. They are related to “Insecure key & Secret Management vulnerability in SQL Anywhere Monitor (Non-Gui)” and “Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java”, respectively.
-
The next one in terms of criticality (CVSS 9.9) is another Hot News and the last one of the month, related to “Code Injection vulnerability in SAP Solution Manager“.
-
The last note of the month we will review (CVSS 7.5) is the only one with high criticality, and it is related to “Memory Corruption vulnerability in SAP CommonCryptoLib”.
-
This month, 75% of the notes to be analyzed are Hot News (3/4), so even though there are few high-criticality notes, they are highly relevant.
-
This month, the most predominant type was “Information Disclosure vulnerability” (3/20 on the patch day), followed by “Code Injection vulnerability” and “Missing Authorization check” (2/20 each).
In the chart below, we can see the classification of the November notes, as well as the trend and classification over the past 5 months (only the Sec. Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
-
Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java (update) (3660659): SAP NetWeaver AS Java is vulnerable to remote code execution due to insecure deserialization of JDK and third-party classes. This update (v40 – November 11, 2025) strengthens security hardening for CVE-2025-42944 (CVSS 10.0 – Critical) by adding new prerequisites (SAP Note 3670067), removing outdated optional class disclaimers, and expanding hardening guidance. The fix blocks vulnerable classes and enforces deserialization restrictions in the AS Java runtime. Customers must ensure JVM version > 8u121, set
element.resynch=DETECTinbootstrap.properties, and apply the referenced notes. A temporary workaround is to add thejdk.serialFilterparameter at JVM level, though SAP recommends applying the full correction. CVSS v3 Base Score 10/ 10 [CVE-2025-42944] -
Insecure key & Secret Management vulnerability in SQL Anywhere Monitor (Non-Gui) (3666261): A vulnerability in SQL Anywhere Monitor (Non-GUI) involved hard-coded credentials embedded within the code, potentially allowing unauthorized users to gain access and execute arbitrary code, impacting confidentiality, integrity, and availability. The issue arose because the Monitor, originally intended to replace Adobe Flash functionality, provided default database access that some environments failed to secure properly. The solution completely removes the SQL Anywhere Monitor and deletes associated databases in default locations, with historical data unloaded. The fix is available in SQL Anywhere 17.0 SP1 PL20 Build 8039. As a workaround, administrators should discontinue and delete any existing SQL Anywhere Monitor instances (samonitor.db) and transition to SQL Anywhere Cockpit for monitoring functionality. CVSS v3 Base Score 10/ 10 [CVE-2025-42890]
-
Code Injection vulnerability in SAP Solution Manager (3668705): An authenticated attacker could exploit missing input sanitation in a remote-enabled function module of SAP Solution Manager, enabling ABAP code injection (CVE-2025-42887) and potentially gaining full system control, resulting in high impact on confidentiality, integrity, and availability. The vulnerability is resolved by adding input sanitization logic that rejects non-alphanumeric characters. SAP recommends applying the provided correction instructions or support packages, as no workaround is available. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42887]
-
Memory Corruption vulnerability in SAP CommonCryptoLib (3633049): A vulnerability in SAP CommonCryptoLib allows an attacker to send specially crafted ASN.1 data during pre-authentication, causing memory corruption and application crashes due to missing boundary checks (CVE-2025-42940). This flaw impacts availability but not confidentiality or integrity. The issue is resolved by enhancing boundary validation — users should upgrade to CommonCryptoLib version 8.5.60 or higher. Refer to SAP Notes 3628110 and 3677814 for patch details. No workaround is available. CVSS v3 Base Score 7,5/ 10 [CVE-2025-42940]
Reference links
Other references, from SAP and Onapsis (november):
SAP Security Patch Day – November 2025
SAP Patch Day: November 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
- SQL Anywhere Monitor (Non-GUI) – SYBASE_SQL_ANYWHERE_SERVER 17.0
- SAP NetWeaver AS Java – SERVERCORE 7.50, ENGINEAPI 7.50, EP-BASIS 7.50, EP-RUNTIME 7.50
- SAP Solution Manager – ST 720
- SAP CommonCryptoLib – CRYPTOLIB 8
- SAP HANA JDBC Client – HDB_CLIENT 2.0
- SAP Business Connector – SAP BC 4.8
- SAP NetWeaver Enterprise Portal – EP-BASIS 7.50, EP-RUNTIME 7.50
- SAP S/4HANA (E-Recruiting BSP) – S4ERECRT 100, 200, ERECRUIT 600, 603, 604, 605, 606, 616, 617, 800, 801, 802
- SAP HANA 2.0 (hdbrss) – HDB 2.00
- SAP GUI for Windows – BC-FES-GUI 8.00, 8.10
- SAP Starter Solution (PL SAFT) – SAP_APPL 600, 602, 603, 604, 605, 606, 616, SAP_FIN 617, 618, 700, 720, 730, S4CORE 100, 101, 102, 103, 104
- SAP Business One (SLD) – B1_ON_HANA 10.0, SAP-M-BO 10.0
- SAP S/4HANA (Manage Journal Entries) – S4CORE 104, 105, 106, 107, 108
- SAP NetWeaver Application Server for ABAP – SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 816
- SAP Fiori for SAP ERP – SAP_GWFND 740, 750, 751, 752, 753, 754, 755, 756, 757, 758