Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
May 2025 Notes
Summary and Highlights of the Month
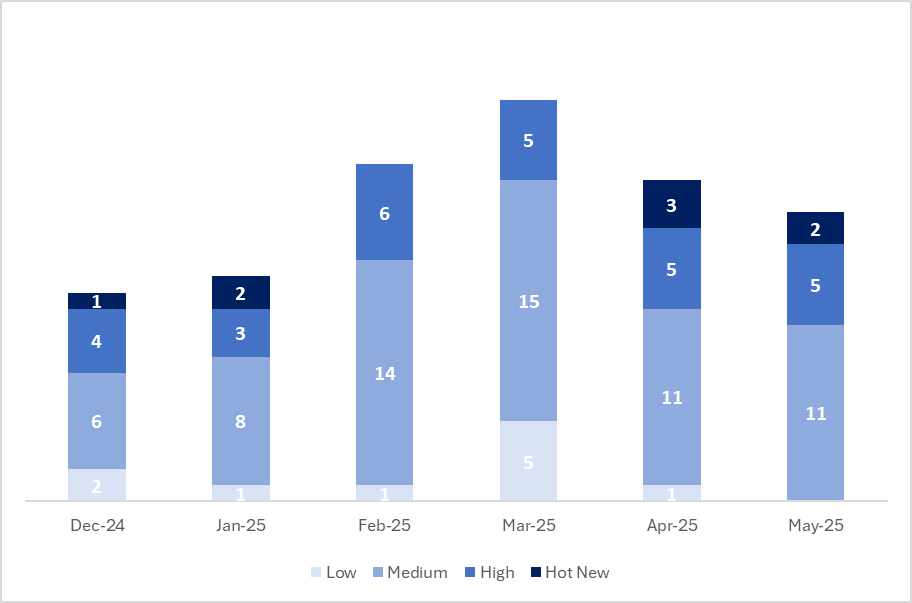
This month, the total number of notes was 18, which is 2 fewer than in the previous period. Two Hot News were published this month, one fewer than in the previous period. Regarding high-criticality notes, 5 were published— the same number as in the previous period. Medium- and low-criticality notes will not be reviewed, so we will detail a total of 7 notes (all with a CVSS score of 7 or higher).
We have a total of 18 notes for the entire month (16 new and 2 updates of notes published in previous months).
We will review in detail a total of 7 notes, all of which are high-criticality and Hot News:
- The most critical note of the month (CVSS 10,0) is a Hot News with the highest possible CVSS score. It is an update of a note released in April: “Missing Authorization Check in SAP NetWeaver (Visual Composer development server)”.
- The next in severity (CVSS 9,1) is a Hot News related to “Insecure Deserialization in SAP NetWeaver (Visual Composer development server)”.
-
The next (CVSS 8,6) is a note related to “Multiple vulnerabilities in SAP Supplier Relationship Management (Live Auction Cockpit)”.
- The following (CVSS 8,3) is a note related to “Code Injection Vulnerability in SAP S/4HANA Cloud Private Edition or On Premise (SCM Master Data Layer (MDL))”.
- The next (CVSS 7,9) concerns “Information Disclosure Vulnerability in SAP Business Objects Business Intelligence Platform (PMW)”.
- Finally, there are two high-criticality notes (CVSS 7,7): the first one related to “Missing Authorization Check in SAP Landscape Transformation (PCL Basis)”, and the second one is an update of a note originally released in July 2024, related to “Missing Authorization Check in SAP PDCE”.
-
This month, the most prevalent type is “Missing Authorization Check” (7 out of 18 on Patch Day).
The chart shows the classification of the May notes, as well as the trend and classification of the past 5 months (only notes from Security Tuesday / Patch Day – by SAP).
Full details
The complete detail of the most relevant notes is as follows:
-
Update – Missing Authorization check in SAP NetWeaver (Visual Composer development server) (3594142): SAP NetWeaver Visual Composer Metadata Uploader is not protected with a proper authorization, allowing unauthenticated agent to upload potentially malicious executable binaries that could severely harm the host system. This could significantly affect the confidentiality, integrity, and availability of the targeted system. The solution is to apply authentication requirements and authorization restrictions reflected in this note. There is a workaround explained in KBA 3593336. CVSS v3 Base Score 10,0/ 10 [CVE-2025-31324]
-
Insecure Deserialization in SAP NetWeaver (Visual Composer development server) (3604119): SAP NetWeaver Visual Composer Metadata Uploader is vulnerable when a privileged user can upload untrusted or malicious content which, when deserialized, could potentially lead to a compromise of confidentiality, integrity, and availability of the host system. Applying this note removes the deserialization, which completely resolves this vulnerability. There is a workaround in KBA 3593336 CVSS v3 Base Score 9,1/ 10 [CVE-2025-42999]
-
Multiple vulnerabilities in SAP Supplier Relationship Management (Live Auction Cockpit) (3578900): Multiple critical vulnerabilities including Blind XXE, XSS, Open Redirect, Information Disclosure, and Insecure Deserialization affect the Live Auction Cockpit component of SAP SRM due to the use of a deprecated Java Applet, and are resolved by removing the applet through updates to versions that use only DHTML, as detailed in SAP Notes 2369341, 2171391, and 1715441. CVSS v3 Base Score 8,6/ 10 [CVE-2025-30018]
-
Code injection vulnerability in SAP S/4HANA Cloud Private Edition or On Premise (SCM Master Data Layer (MDL)) (3600859): A code injection vulnerability in SAP S/4HANA Cloud Private Edition or on-premise (SCM Master Data Layer) allows authenticated users to remotely replace ABAP programs due to missing input validation and authorization checks, and is resolved by deprecating the obsolete function module through a correction that disables its execution. CVSS v3 Base Score 8,3/ 10 [CVE-2025-43010]
-
Information Disclosure Vulnerability in SAP Business Objects Business Intelligence Platform (PMW): (3586013):An information exposure vulnerability in Promotion Management Wizard (PMW) allows unauthorized access to restricted data due to the ability to launch certain executables, and is resolved by restricting unnecessary information for end users through the implementation of the provided patches. There is a workaround in the note. CVSS v3 Base Score 7,9/ 10 [CVE-2025-43000]
-
Missing Authorization Check in SAP Landscape Transformation (PCL Basis) (3591978): A missing authorization check in SAP Landscape Transformation’s PCL Basis module allows authenticated users to access restricted data, impacting confidentiality, and is resolved by enhancing the affected remote-enabled function modules with proper authorization checks as detailed in the provided correction instructions or support packages. There isn’t workaround for this note. CVSS v3 Base Score 7,7/ 10 [CVE-2025-43011]
- Update – Missing Authorization check in SAP PDCE (3483344): A privilege escalation vulnerability in PDCE allows authenticated users to access sensitive information due to missing authorization checks, and is resolved in version 19 by deactivating the affected functions and providing updated correction instructions for SEM-BW 600 SP01 to SP015 to simplify implementation without complex prerequisites. There is not workaround. CVSS v3 Base Score 7,7/ 10 [CVE-2024-39592]
Reference links
Other references, from SAP and Onapsis (may):
SAP Security Patch Day – May 2025
SAP Patch Day: May 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
-
SAP NetWeaver (Visual Composer development server) Version – VCFRAMEWORK 7.50
-
SAP Supplier Relationship Management (Live Auction Cockpit) Version – SRM_SERVER 7.14
-
SAP S/4HANA Cloud Private Edition or on Premise (SCM Master Data Layer (MDL)) Versions – S4CORE 102, 103, 104, 105, 106, 107, 108, SCM_BASIS 700, 701, 702, 712, 713, 714
- SAP NetWeaver Application Server ABAP, Versions – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93
-
SAP Business Objects Business Intelligence Platform (PMW) Versions – ENTERPRISE 430, 2025, 2027
-
SAP Landscape Transformation (PCL Basis) Versions – DMIS 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2018_1_752, 2020, S4CORE 102, 103, 104, 105, 106, 107, 108
-
SAP PDCE Versions – S4CORE 102, 103, S4COREOP 104, 105, 106, 107, 108
-
SAP Gateway Client Versions – SAP_GWFND 752, 753, 754, 755, 756, 757, 758
-
SAP S/4HANA (Private Cloud & On-Premise) Versions – S4CRM 204, 205, 206, S4CEXT 107, 108, BBPCRM 702, 712, 713, 714
-
SAP Service Parts Management (SPM) Versions – SAP_APPL 600, 602, 603, 604, 605, 606, 616, 617, 618, SAPSCORE 111, SAPSCORE 116, S4CORE 100, 101, 102
-
SAP NetWeaver Application Server ABAP and ABAP Platform Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
-
SAP Supplier Relationship Management (Master Data Management Catalog Version – SRM_MDM_CAT 7.52
-
SAP S/4HANA HCM Portugal and SAP ERP HCM Portugal Versions – S4HCMCPT 100, 101, SAP_HRCPT 600, 604, 608
-
SAP Digital Manufacturing (Production Operator Dashboard) Version – CTNR-DME-PODFOUNDATION-MS 1.0
-
SAP Data Services Management Console Version – SBOP DS JOB SERVER 4.3
-
SAP S4/HANA (OData meta-data property) Versions – S4CORE 102, 103, 104, 105, 106
-
SAP GUI for Windows Version – BC-FES-GUI 8.00