Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
June 2025 Notes
Summary and Highlights of the Month
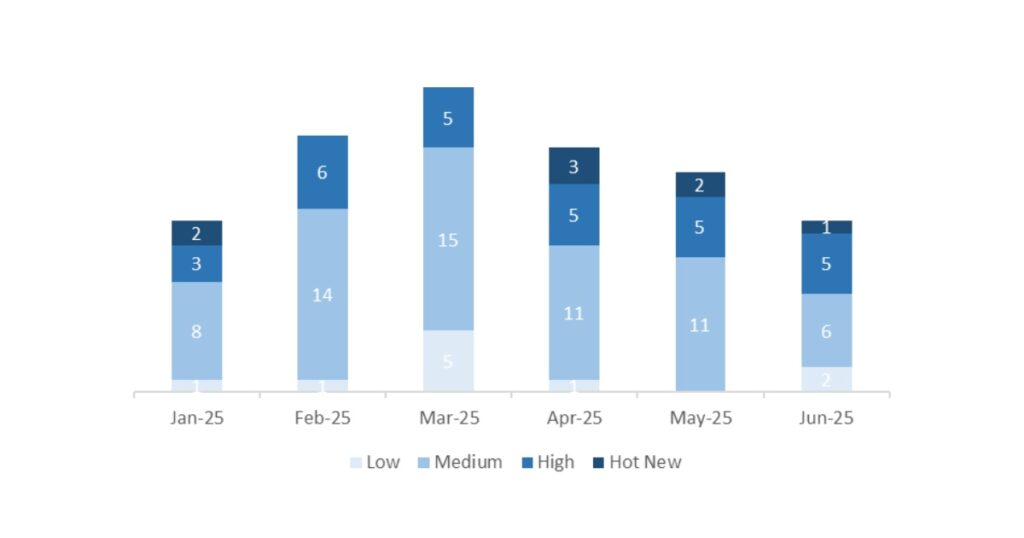
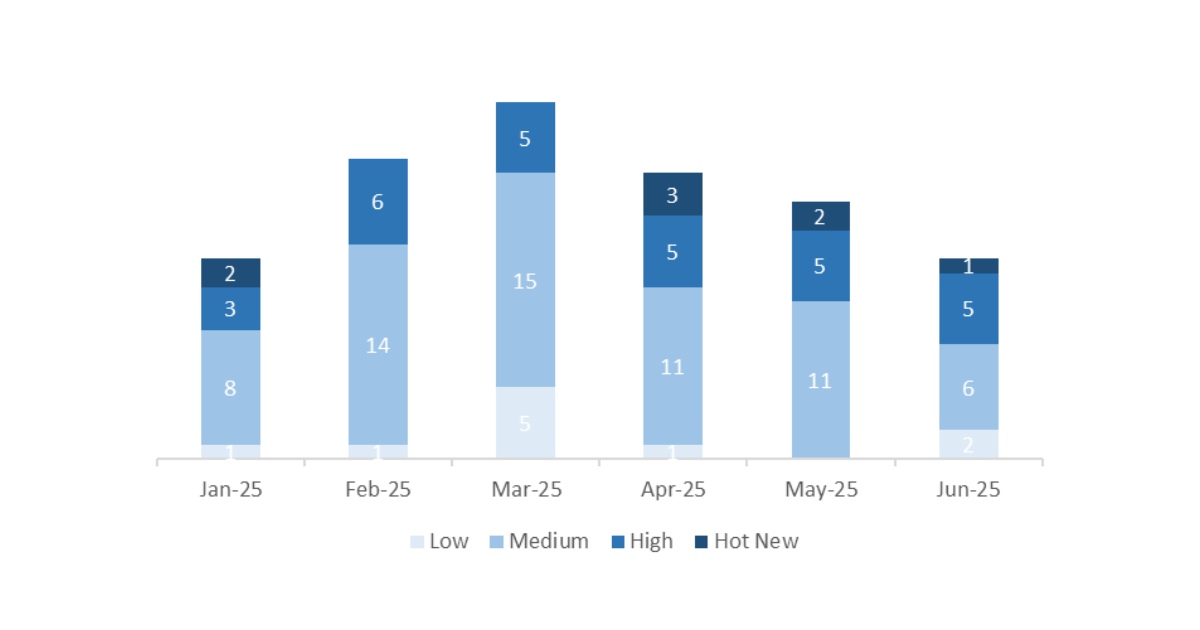
This month, the total number of notes was 14, which is 4 fewer than the previous month. We had 1 Hot News this month, 1 less than in the previous period. Regarding high-criticality notes, there are 5, the same as last month. Medium and low-criticality notes will not be reviewed, so we will detail a total of 6 notes (all with a CVSS of 7 or higher).
We have a total of 14 notes for the entire month (14 new ones).
We will review in detail a total of 6 notes, all of high criticality and Hot News:
- One of the most critical notes of the month (CVSS 9.6) is a High note, related to “Missing Authorization Check in SAP NetWeaver Application Server for ABAP”
- The next one in criticality (CVSS 8.8) is a note related to “Information Disclosure in SAP GRC (AC Plugin)”
- The next one in criticality (CVSS 8.5) is a note related to “Missing Authorization Check in SAP Business Warehouse and SAP Plug-In Basis”
- The next one in criticality (CVSS 8.2) is a note related to “Cross-Site Scripting (XSS) vulnerability in SAP BusinessObjects Business Intelligence (BI Workspace)”
- The next ones in criticality are 2 medium notes (CVSS 7.6 and CVSS 7.5), one related to “Directory Traversal vulnerability in SAP NetWeaver Visual Composer” and the other related to “Multiple vulnerabilities in SAP MDM Server”
-
This month, the most predominant type is “Missing Authorization Check” (6/14 on patch day)
In the chart, we can see the classification of the June notes, as well as the evolution and classification of the previous 5 months (only Security Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
-
Missing Authorization check in SAP NetWeaver Application Server for ABAP) (3600840): RFC inbound processing fails to perform the necessary authorization checks for an authenticated user, resulting in privilege escalation. A successful exploit could have a critical impact on both the integrity and availability of the application. The way to eliminate this risk is by the authorization checks which are now added to initiate S_RFC authorization for tRFC and qRFC calls. Apply the kernel patch and set the profile parameter indicated in the note. CVSS v3 Base Score 9,6/ 10 [CVE-2025-42989]
-
Missing Authorization check in SAP Business Warehouse and SAP Plug-In Basis (3609271): SAP GRC allows a non-administrative user to access and initiate a transaction that could allow them to modify or control transmitted system credentials. This has a significant impact on the confidentiality, integrity, and availability of the application. This problem is solved by preventing the report from running. CVSS v3 Base Score 8,8/ 10 [CVE-2025-42982]
-
Authentication Bypass Vulnerability in SAP Financial Consolidation (3606484) SAP Business Warehouse and SAP Plug-In Basis allow an authenticated attacker to drop arbitrary SAP database tables, potentially resulting in data loss or system inoperability. A successful exploit can completely delete database entries, but cannot read any data. The problem is solved by removing the code in the RFC function module. CVSS v3 Base Score 8,5/ 10 [CVE-2025-42983]
-
Cross-Site Scripting (XSS) vulnerability in SAP BusinessObjects Business Intelligence (BI Workspace) (3560693): SAP BusinessObjects Business Intelligence (BI workspace) allows an unauthenticated attacker to create and store malicious scripts within a workspace. When the victim accesses the workspace, the script will execute in their browser, potentially allowing the attacker to access sensitive session information, modify the session information, or make it unavailable. This results in a high confidentiality impact and a low integrity and availability impact. CVSS v3 Base Score 8,2/ 10 [CVE-2025-23192]
-
Directory Traversal vulnerability in SAP NetWeaver Visual Composer (3610591): SAP NetWeaver Visual Composer contains a Directory Traversal vulnerability caused by insufficient validation of input paths provided by a high-privilege user. This allows an attacker to read or modify arbitrary files, which has a high confidentiality impact and a low integrity impact. CVSS v3 Base Score 7,6/ 10 [CVE-2025-42977]
-
Multiple vulnerabilities in SAP MDM Server (3610006): This security advisory addresses three vulnerabilities in SAP MDM Server:
-
- Memory Corruption [CVE-2025-42994]: The SAP MDM Server ReadString feature allows an attacker to send specially crafted packets that could trigger a memory read access violation in the server process that would crash and exit unexpectedly causing a large availability impact with no impact on the confidentiality and integrity of the application.
-
- Memory Corruption [CVE-2025-42995] : The SAP MDM server read function allows an attacker to send specially crafted packets that could trigger a memory read access violation in the server process which would crash and exit unexpectedly causing a large impact on availability with no impact on the confidentiality and integrity of the application.
-
- Insecure Session Management [CVE-2025-42996] : SAP MDM Server allows an attacker to gain control of existing client sessions and execute certain functions without re-authentication, allowing access to or modification of non-sensitive information or consuming sufficient resources that could degrade server performance, resulting in minimal impact to the confidentiality, integrity, and availability of the application.
This problem is solves by implementing random generation of session tokens. Apply the latest patch by effectively replacing the main server executable and restarting it. CVSS v3 Base Score 7,5/ 10 [CVE-2025-42994]
Reference links
Other references, from SAP and Onapsis (june):
SAP Security Patch Day – June 2025
SAP Patch Day: June 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
- SAP NetWeaver Application Server for ABAP Versions – KERNEL 7.89, 7.93, 9.14, 9.15
- SAP GRC (AC Plugin) Versions – GRCPINW V1100_700, V1100_731
- PI_BASIS 2006_1_700, 701, 702, 731, 740, SAP_BW 750, 751, 752, 753, 754, 755, 756, 757, 758, 914, 915
- SAP BusinessObjects Business Intelligence (BI Workspace) Versions – ENTERPRISE 430, 2025, 2027
- SAP NetWeaver Visual Composer Version – VCBASE 7.50
- SAP MDM Server Versions – MDM_SERVER 710.750
- SAP S/4HANA (Enterprise Event Enablement) Versions – SAP_GWFND 757, 758
- SAP NetWeaver (ABAP Keyword Documentation) Version – SAP_BASIS 758
- SAP S/4HANA (Manage Central Purchase Contract application) Versions – S4CORE 106, 107, 108
- SAP Business One Integration Framework Versions – B1_ON_HANA 10.0, SAP-M-BO 10.0
- SAP S/4HANA (Manage Processing Rules – For Bank Statement) Versions – S4CORE 104, 105, 106, 107, 108
- SAP S/4HANA (Bank Account Application) Version – S4CORE 108
- SAP Business Objects Business Intelligence Platform Versions – ENTERPRISE 430, 2025, 2027
- SAPUI5 applications Versions – SAP_UI 750, 754, 755, 756, 757, 758, UI_700 200