Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
July 2025 Notes
Summary and Highlights of the Month
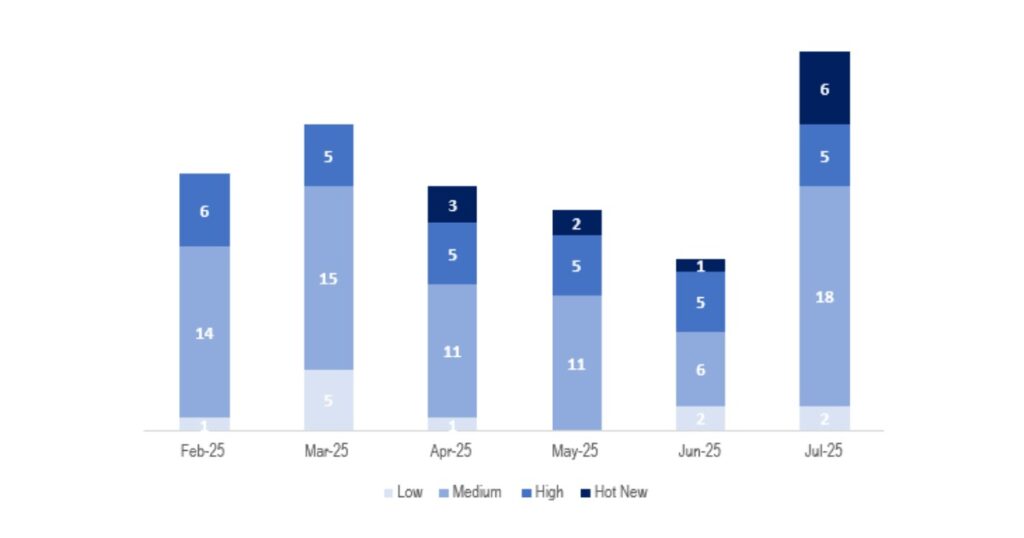
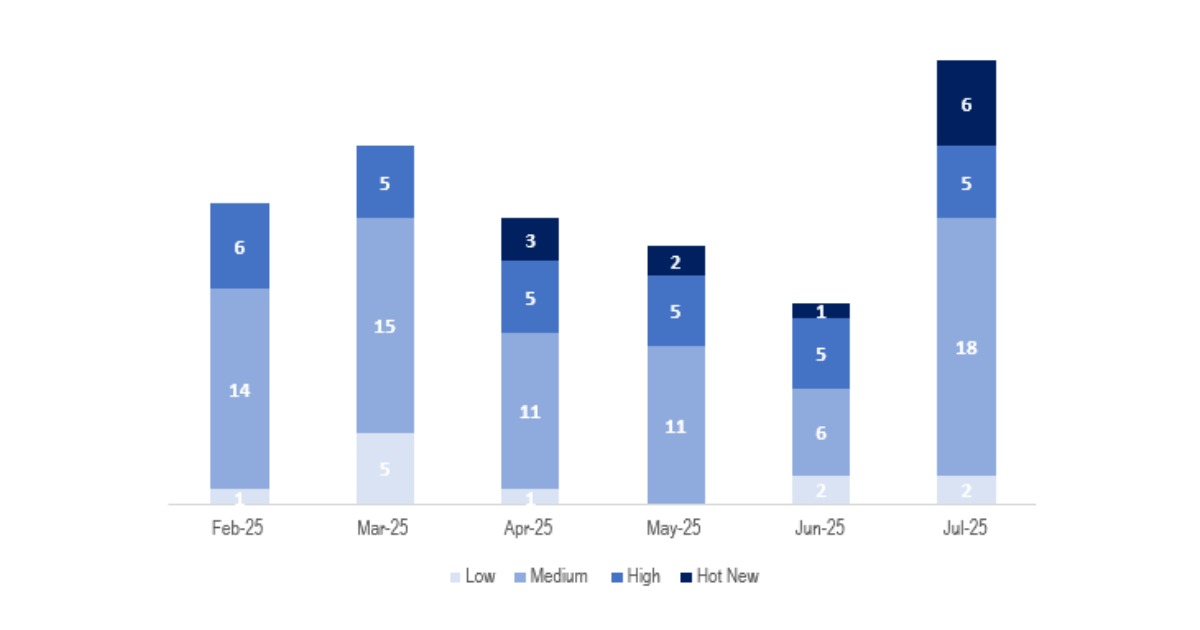
This month, the total number of notes was 31, which is 17 more than the previous month. This month we had 6 Hot News, 5 more than in the previous period. Regarding high-criticality notes, there are 5, the same as in the past 3 months. The medium and low notes will not be reviewed, so we will provide details for a total of 11 notes (all with a CVSS of 7 or higher).We have a total of 31 notes for the whole month (27 new ones and 4 updates of notes published in previous months).
We will review in detail a total of 11 notes, all of them high-criticality and Hot News:
-
The most critical note of the month (CVSS 10) is a Hot News and it is an update of a note published in May related to “Multiple vulnerabilities in SAP Supplier Relationship Management (Live Auction Cockpit)”.
-
The next one in terms of criticality (CVSS 9.9) is a note related to “Code Injection vulnerability in SAP S/4HANA and SAP SCM (Characteristic Propagation)”.
-
The next ones in terms of criticality (CVSS 9.1) are 4 Hot News related to “Insecure Deserialization in SAP NetWeaver Enterprise Portal Federated Portal Network”, “Insecure Deserialization in SAP NetWeaver Enterprise Portal Administration”, “Insecure Deserialization vulnerability in SAP NetWeaver (XML Data Archiving Service)” and “Insecure Deserialization in SAP NetWeaver Application Server for Java (Log Viewer)”.
-
The next ones in terms of criticality (CVSS 8.1) are two high-criticality notes related to “Missing Authentication check after implementation of SAP Security Note 3007182 and 3537476” and “Missing Authorization check in SAP NetWeaver Application Server for ABAP”.
-
The next one in terms of criticality (CVSS 8.0) is a note related to “Insecure File Operations vulnerability in SAP Business Objects Business Intelligence Platform (CMC)”.
-
The next one in terms of criticality (CVSS 7.7) is a note related to “Missing Authorization check in SAP Business Warehouse and SAP Plug-In Basis”.
-
Finally, the last note we will analyze and the lowest in criticality (CVSS 7.6) is an update of a note from last month related to “Directory Traversal vulnerability in SAP NetWeaver Visual Composer”.
-
This month the most predominant type is “Missing Authorization Check” (8/31 on patch day).
In the chart, we can see the classification of the July notes, as well as the evolution and classification for the past 5 months (only the Sec. Tuesday / Patch Day notes – by SAP).
Full details
The complete detail of the most relevant notes is as follows:
-
Multiple vulnerabilities in SAP Supplier Relationship Management (Live Auction Cockpit) (update) (3578900): This SAP Security Note addresses five critical vulnerabilities in SRM Live Auction Cockpit, including a critical insecure deserialization flaw (CVE-2025-30012) with a CVSS score of 10.0. The issues stem from deprecated Java Applet components, now fully removed or replaced in newer versions. SAP recommends migrating to DHTML-based SRM Live Auction or removing legacy components using deployment tools. Refer to Notes 2369341, 2171391, and 1715441 for remediation steps. CVSS v3 Base Score 10/ 10 [CVE-2025-30012]
-
Code Injection vulnerability in SAP S/4HANA and SAP SCM (Characteristic Propagation) (3618955): A remote code execution vulnerability in SAP S/4HANA and SCM Characteristic Propagation allows authenticated internal users to inject and execute OS-level commands, risking full system compromise. The issue is mitigated by blocking the injection of malicious code from external systems. Apply the relevant correction instructions or support packages to resolve the vulnerability. There is no workaround. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42967]
-
Insecure Deserialization in SAP NetWeaver Enterprise Portal Federated Portal Network (3620498) SAP NetWeaver Enterprise Portal (FPN) has an insecure deserialization vulnerability that may allow privileged users to execute malicious code, compromising system security. The deserialization logic has been improved to validate input. SAP recommends applying the provided patches, as the optional workaround is only a temporary measure and the vulnerable endpoint is already access-restricted to admin users. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42980]
-
Insecure Deserialization in SAP NetWeaver Enterprise Portal Administration) (3621236): A vulnerability in SAP NetWeaver Enterprise Portal Administration allows privileged users to upload and deserialize malicious content, potentially leading to remote code execution. Input validation during deserialization has been enhanced. SAP recommends applying the relevant patches, as the workaround is only temporary and the vulnerable endpoint is already limited to highly privileged administrators. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42964]
-
Insecure Deserialization vulnerability in SAP NetWeaver (XML Data Archiving Service) (3610892): SAP NetWeaver XML Data Archiving Service (XML DAS) contains an insecure Java deserialization vulnerability that can be exploited by authenticated admin users, potentially compromising system confidentiality, integrity, and availability. The deserialization logic has been strengthened. Apply the corresponding patch and follow SAP Note 952402 for full remediation. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42966]
-
Insecure Deserialization in SAP NetWeaver Application Server for Java (Log Viewer ) (3621771): A critical vulnerability in SAP NetWeaver AS Java Log Viewer allows authenticated admin users to exploit unsafe Java deserialization, potentially leading to full OS compromise. The patch eliminates the issue by removing the vulnerable RM module. SAP recommends applying the relevant support packages and reviewing SAP Note 1974464 to avoid dependency issues. As a temporary workaround, the LogViewer component can be disabled via a startup filter, with logs still accessible through SAP MMC or the file system. Full details are provided in FAQ note 3626657. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42963]
-
Missing Authentication check after implementation of SAP Security Note 3007182 and 3537476 (3600846): A replay attack vulnerability allows an unauthenticated attacker to reuse a Hashed Message Authentication Code (HMAC) credential from a system missing specific security patches, potentially compromising a fully patched target system. The solution involves deleting and regenerating the HMAC key, with careful validation of system state to avoid issues with tRFC, qRFC, bgRFC, or recorded HTTP calls. Follow the steps outlined to delete the old HMAC key and regenerate it during a short downtime, ensuring secure system operations. CVSS v3 Base Score 8,1/ 10 [CVE-2025-42959]
-
Missing Authorization check in SAP NetWeaver Application Server for ABAP (3623440): A privilege escalation vulnerability in SAP NetWeaver System Configuration allows authenticated users to bypass necessary authorization checks, potentially compromising the system’s integrity and availability. The solution involves implementing an authorization check for the ‘S_RZL_ADM’ profile with Activity ’01’. SAP recommends applying the support package or correction instructions provided. As a temporary workaround, restrict the use of the S_RFC authorization to specific functions or function groups, though the permanent fix is preferred. CVSS v3 Base Score 8,1/ 10 [CVE-2025-42953]
-
Insecure File Operations vulnerability in SAP Business Objects Business Intelligence Platform (CMC) (3565279): SAP Business Objects Business Intelligence Platform (CMC) uses an older version of Apache Struts (2.5.33) with the vulnerability, which allows for unrestricted file uploads and potential malicious file execution by administrators. The solution is to update Apache Struts to a secure version. SAP recommends applying the necessary patches listed in the security note. For additional details, refer to Knowledge Base Article 2144559 regarding maintenance strategy. There is no workaround. CVSS v3 Base Score 8,0/ 10 [CVE-2024-53677]
-
Missing Authorization check in SAP Business Warehouse and SAP Plug-In Basis (3623255): A vulnerability in SAP Business Warehouse and SAP Plug-In Basis allows authenticated attackers to add fields to SAP database tables or structures, potentially causing system short dumps and impacting availability. The issue stems from missing authorization checks in a report comparing middleware structures between CRM and ERP. The solution involves adding an authorization check (SCRMMW) to the affected RFC function module. SAP recommends implementing the correction instructions or support packages provided in the security note. CVSS v3 Base Score 7,7/ 10 [CVE-2025-42952]
-
Directory Traversal vulnerability in SAP NetWeaver Visual Composer (update) (3610591): SAP NetWeaver Visual Composer has a Directory Traversal vulnerability caused by insufficient validation of input paths from high-privileged users, allowing arbitrary file access and compromising confidentiality. The issue has been addressed by improving URL parameter validation. The update reintroduces a workaround for versions without a patch, which involves un-deploying the VisualComposerServerEar05.ear file (part of VCBASE.SCA). SAP recommends applying the relevant support packages or patches and reviewing KBA 3619959 for more information on the workaround. CVSS v3 Base Score 7,6/ 10 [CVE-2025-42977]
Reference links
Other references, from SAP and Onapsis (july):
SAP Security Patch Day – July 2025
SAP Patch Day: July 2025 – Onapsis
Resources affected
The full list of affected systems/components is as follows:
-
SAP Supplier Relationship Management (Live Auction Cockpit) Version – SRM_SERVER 7.14
-
SAP S/4HANA and SAP SCM (Characteristic Propagation) Versions – SCMAPO 713, 714, S4CORE 102, 103, 104, S4COREOP 105, 106, 107, 108, SCM 700, 701, 702, 712
-
SAP NetWeaver Enterprise Portal Federated Portal Network Version – EP-RUNTIME 7.50
-
SAP NetWeaver Enterprise Portal Administration Version – EP-RUNTIME 7.50
-
SAP NetWeaver (XML Data Archiving Service) Version – J2EE-APPS 7.50
-
SAP NetWeaver Application Server for Java (Log Viewer) Version – LMNWABASICAPPS 7.50
-
SAP NetWeaver ABAP Server and ABAP Platform Versions – SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 914, 915
-
SAP Business Objects Business Intelligence Platform (CMC) Versions – ENTERPRISE 430, 2025
-
SAP Business Warehouse and SAP Plug-In Basis Versions – PI_BASIS 2006_1_700, 701, 702, 731, 740, SAP_BW 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 816
-
SAP NetWeaver Visual Composer Version – VCBASE 7.50