Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
February 2026 Notes
Monthly Summary and Highlights
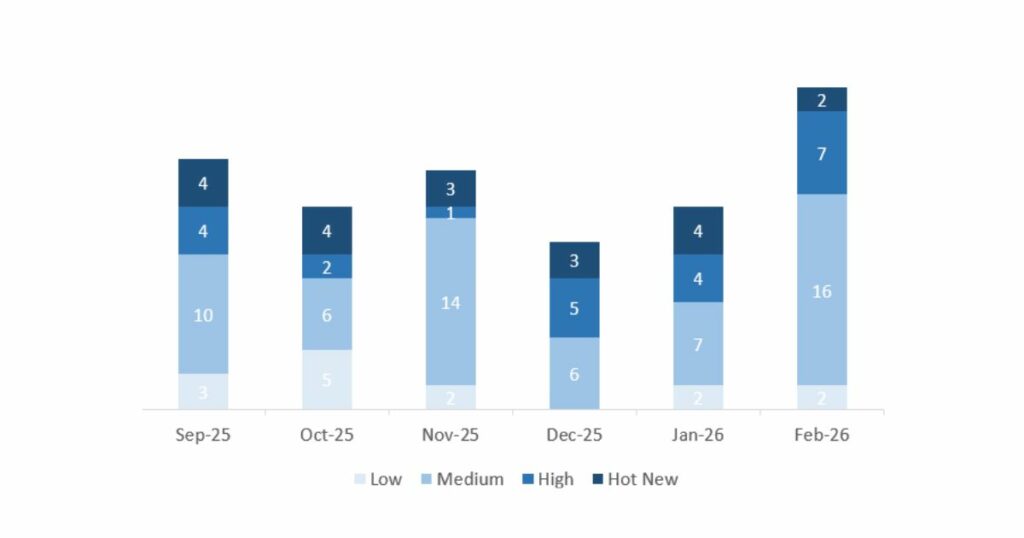
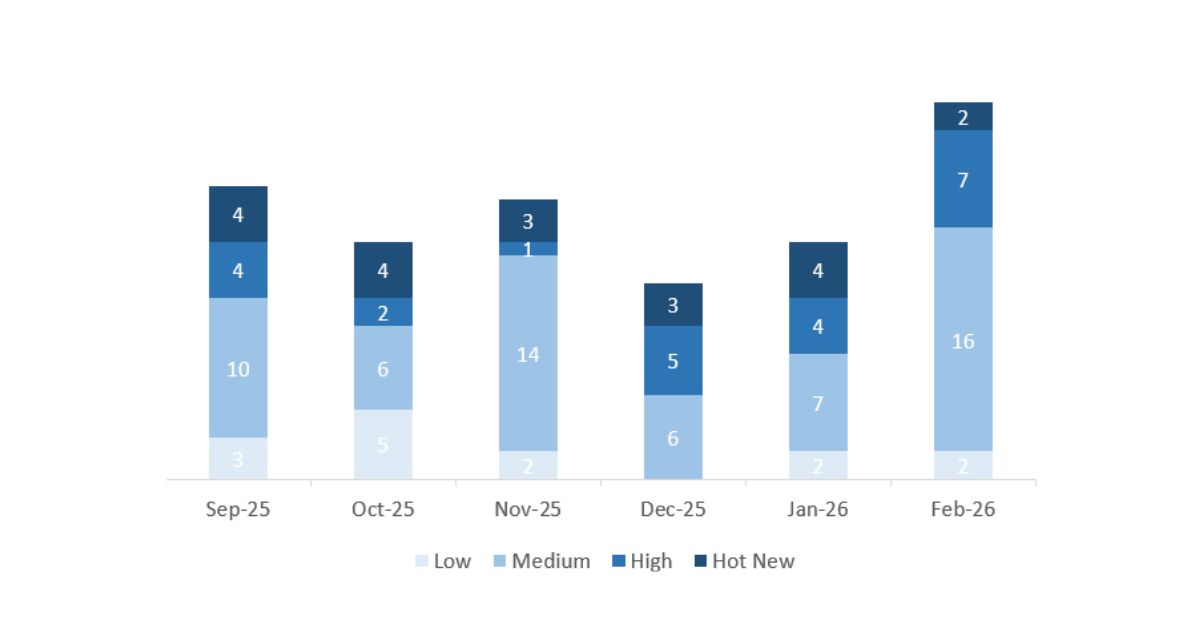
This month the total number was 27 notes (26 new and 1 update), 10 more than in January. This month, 2 Hot News were published, two fewer than in the previous period. Regarding high criticality notes, there are 7, three more compared to January. Medium and low notes will not be reviewed, so we will provide details on a total of 9 notes (all those with a CVSS of 7 or higher).
We have a total of 27 notes for the entire month (26 are new and 1 is an update of a note from previous months). We will review in detail a total of 9 notes, all of them high criticality and Hot News:
-
The highest criticality note of the month (CVSS 9.9) is a Hot News, related to “Code Injection vulnerability in SAP CRM and SAP S/4HANA (Scripting Editor)”.
-
The next in criticality (CVSS 9.6) is another Hot News, the second of the month, related to “Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform”.
-
The following is a high note (CVSS 8.8) related to “XML Signature Wrapping in SAP NetWeaver AS ABAP and ABAP Platform”.
-
The next in criticality (CVSS 7.7) are two high notes, one related to “Denial of service (DOS) in SAP Supply Chain Management” and the other to “Missing Authorization check in SAP Solution Tools Plug-In (ST-PI)”.
-
The next in criticality (CVSS 7.5) are two high notes related to “Denial of service (DOS) in SAP BusinessObjects BI Platform” and “Denial of service (DOS) vulnerability in SAP BusinessObjects BI Platform” (two different CVEs affecting the same product).
-
The next in criticality (CVSS 7.4) is a high note related to “Race Condition in SAP Commerce Cloud”.
-
The last note we will review (CVSS 7.3) is high criticality and concerns “Open Redirect vulnerability in SAP BusinessObjects Business Intelligence Platform”.
This month the most predominant type was “Missing Authorization check” (9/27 on patch day).
In the chart you can see the classification of the February notes, as well as the evolution and classification of the previous 5 months (only Sec. Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
-
Code Injection vulnerability in SAP CRM and SAP S/4HANA (Scripting Editor) (3697099): An authenticated attacker in SAP CRM and SAP S/4HANA (Scripting Editor) could exploit a flaw in a generic function module call and execute unauthorized critical functionalities, which includes the ability to execute an arbitrary SQL statement. This leads to a full database compromise with high impact on confidentiality, integrity, and availability. A temporary workaround is available. CVSS v3 Base Score 9,9/10 [CVE-2026-0488]
-
Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform (3674774): SAP NetWeaver Application Server ABAP and ABAP Platform allows an authenticated, low-privileged user to perform background Remote Function Calls without the required S_RFC authorization in certain cases. This can result in a high impact on integrity and availability, and no impact on the confidentiality of the application. CVSS v3 Base Score 9,6/10 [CVE-2026-0509]
-
XML Signature Wrapping in SAP NetWeaver AS ABAP and ABAP Platform (3697567): SAP NetWeaver Application Server ABAP and ABAP Platform allows an authenticated attacker with normal privileges to obtain a valid signed message and send modified signed XML documents to the verifier. This may result in acceptance of tampered identity information, unauthorized access to sensitive user data and potential disruption of normal system usage. A temporary workaround is available. CVSS v3 Base Score 8,8/10 [CVE-2026-23687]
-
Denial of service (DOS) in SAP Supply Chain Management (3703092): Due to an uncontrolled resource consumption (Denial of Service) vulnerability, an authenticated attacker with regular user privileges and network access can repeatedly invoke a remote-enabled function module with an excessively large loop-control parameter. This triggers prolonged loop execution that consumes excessive system resources, potentially rendering the system unavailable. Successful exploitation results in a denial-of-service condition that impacts availability, while confidentiality and integrity remain unaffected. CVSS v3 Base Score 7,7/10 [CVE-2026-23689]
-
Missing Authorization check in SAP Solution Tools Plug-In (ST-PI) (3705882): SAP Solution Tools Plug-In (ST-PI) contains a function module that does not perform the necessary authorization checks for authenticated users, allowing sensitive information to be disclosed. This vulnerability has a high impact on confidentiality and does not affect integrity or availability. CVSS v3 Base Score 7,7/10 [CVE-2026-24322]
-
Denial of service (DOS) in SAP BusinessObjects BI Platform (3654236): SAP BusinessObjects BI Platform allows an unauthenticated attacker to craft a specific network request to the trusted endpoint that breaks the authentication, which prevents the legitimate users from accessing the platform. As a result, it has a high impact on the availability but no impact on the confidentiality and integrity. A temporary workaround is available. CVSS v3 Base Score 7,5/10 [CVE-2026-0490]
-
Denial of service (DOS) vulnerability in SAP BusinessObjects BI Platform (3678282): SAP BusinessObjects BI Platform allows an unauthenticated attacker to send specially crafted requests that could cause the Content Management Server (CMS) to crash and automatically restart. By repeatedly submitting these requests, the attacker could induce a persistent service disruption, rendering the CMS completely unavailable. Successful exploitation results in a high impact on availability, while confidentiality and integrity remain unaffected. A temporary workaround is available. CVSS v3 Base Score 7,5/10 [CVE-2026-0485]
-
Race Condition in SAP Commerce Cloud (3692405): Under certain conditions, SAP Commerce Cloud allows an authenticated user to bypass SSL trust validation for outbound connections due to a race condition in the Eclipse Jersey library (CVE-2025-12383), leading to a High impact on confidentiality and integrity, and no impact on the availability of the application. CVSS v3 Base Score 7,4/10 [CVE-2025-12383]
-
Open Redirect vulnerability in SAP BusinessObjects Business Intelligence Platform (3674246): The SAP BusinessObjects Business Intelligence Platform allows an authenticated attacker with high privileges to insert malicious URL within the application. Upon successful exploitation, the victim may click on this malicious URL, resulting in an unvalidated redirect to the attacker-controlled domain and subsequently download the malicious content. This vulnerability has a high impact on the confidentiality and integrity of the application, with no effect on the availability of the application. CVSS v3 Base Score 7,3/10 [CVE-2026-0508]
Reference links
Other references, from SAP and Onapsis (February):
Resources affected
The full list of affected systems/components is as follows:
-
SAP CRM and SAP S/4HANA (Scripting Editor): S4FND 102-109, SAP_ABA 700, WEBCUIF 700, 701, 730, 731, 746, 747, 748, 800, 801
-
SAP NetWeaver Application Server ABAP and ABAP Platform: KRNL64NUC 7.22, KRNL64UC 7.22, 7.53, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 9.16, 9.18, 9.19; SAP_BASIS 700-702, 731, 740, 750-758, 804, 816, 916-918
-
SAP Supply Chain Management: SCMAPO 713, 714, SCM 700, 701, 702, 712
-
SAP Solution Tools Plug-In (ST-PI): ST-PI 2008_1_700, 2008_1_710, 740, 758
-
SAP BusinessObjects BI Platform: ENTERPRISE 430, 2025, 2027
-
SAP Commerce Cloud: HY_COM 2205, COM_CLOUD 2211, COM_CLOUD 2211-JDK21