Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
November 2023 notes
Summary and highlights of the month
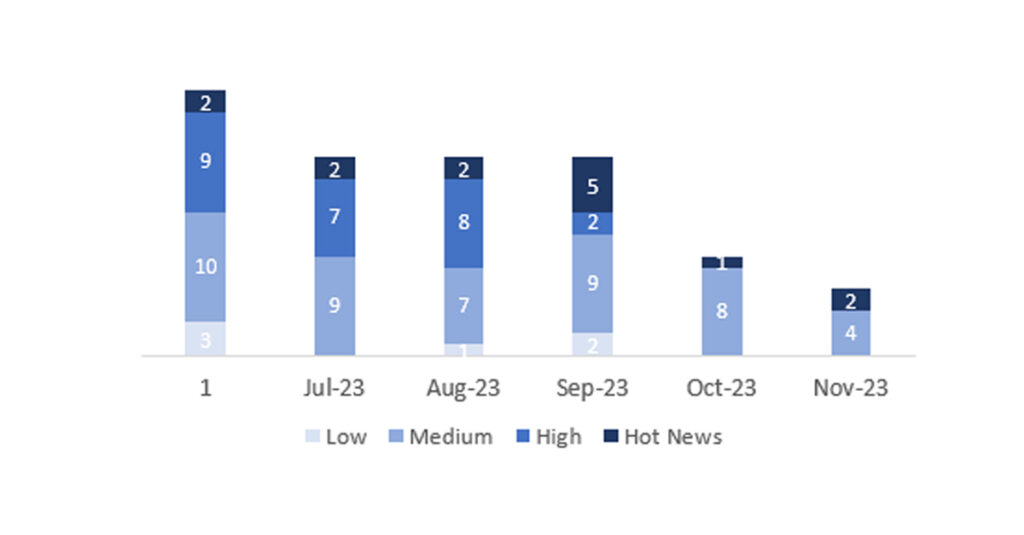
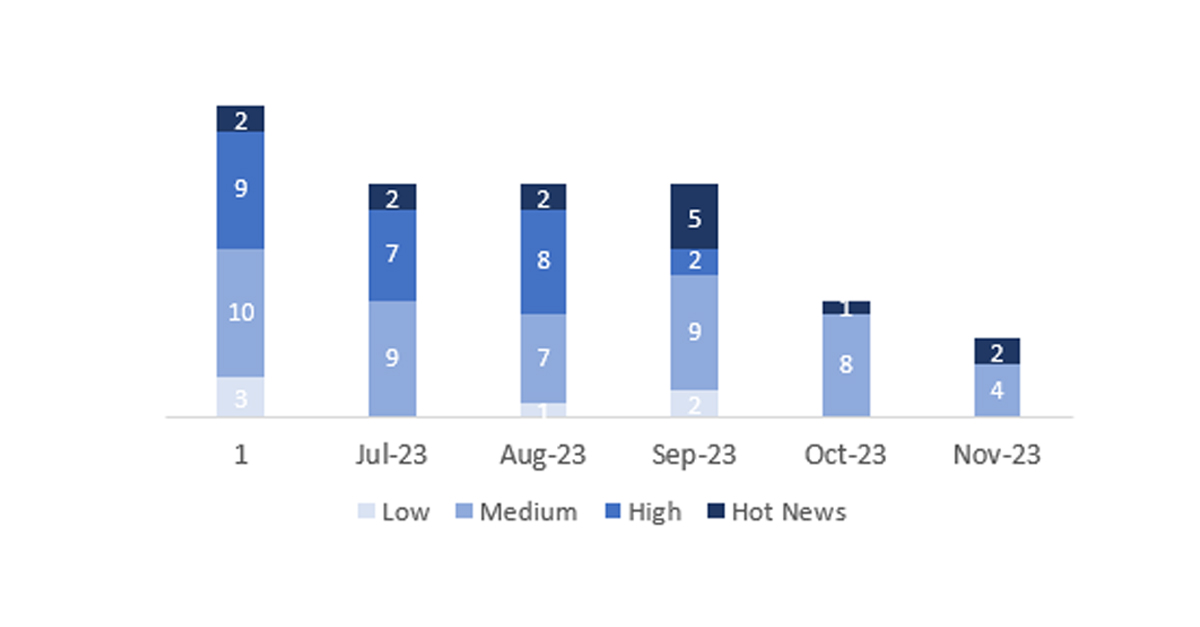
The total number of notes/patches this month has been 6, which is 3 less than last month. The number of Hot News is 2, 1 more than last month. It’s also worth noting that the number of high criticality notes remains at 0. As usual, we will leave the medium and low severity notes unchecked this month, but we will detail a total of 2 notes (all those with a CVSS of 7 or higher).
We have a total of 6 notes for the entire month (the 6 from Patch Tuesday, 3 new and 3 updates, which are 3 less than the previous Patch Tuesday).
We will review in detail the 2 HotNews of this month, 1 new and 1 update (those with a CVSS score equal to or greater than 7).
- The most critical note of the month (with a CVSS of 9.8) is an update of a note published on September 2023 Patch Day, related to “Missing Authorization check in SAP CommonCryptoLib”.
- The next note in terms of criticality (with a CVSS of 9.6) is related to “Improper Access Control vulnerability in SAP Business One product installation”.
- This month, the most predominant type is “Information Disclosure vulnerability” (2 out of 6 on Patch Day).
In the graph (SAP’s November 2023 post), we can see the classification of the November notes, as well as the evolution and classification of the last 5 months (only notes from Sec. Tuesday / Patch Day – by SAP).
Full details
The complete detail of the most relevant notes is as follows:
- Update – Missing Authorization check in SAP CommonCryptoLib (3340576): SAP CommonCryptoLib does not perform necessary authentication checks, which may result in missing or wrong authorization checks for an authenticated user, resulting in escalation of privileges. Depending on the application and the level of privileges acquired, an attacker could abuse functionality restricted to a particular user group as well as read, modify or delete restricted data. CVSS v3 Base Score: 9,8 / 10 [CVE-2023-40309].
- Improper Access Control vulnerability in SAP Business One product installation (3355658): SAP Business One installation does not perform proper authentication and authorization checks for SMB shared folder. As a result any malicious user can read and write to the SMB shared folder. Additionally, the files in the folder can be executed or be used by the installation process leading to considerable impact on confidentiality, integrity and availability. The impacted components are Crystal Report (CR) shared folder, Traditional Mobile app (attachment path), RSP (log folder logic), Job Service and BAS (file upload folder).CVSS v3 Base Score: 9,6 / 10 [CVE-2023-31403].
Reference links
Other references, from SAP and Onapsis (November):
SAP Security Patch Day for November 2023| Onapsis
Resources affected
- SAP CommonCryptoLib, Version–8
- SAP NetWeaver AS ABAP, SAP NetWeaver AS Java and ABAP Platform of S/4HANA on-premise Versions -KERNEL 7.22, KERNEL 7.53, KERNEL 7.54, KERNEL 7.77, KERNEL 7.85, KERNEL 7.89, KERNEL 7.91, KERNEL 7.92, KERNEL 7.93, KERNEL 7.22, KERNEL 8.04, KERNEL64UC 7.22, KERNEL64UC 7.22EXT, KERNEL64UC 7.53, KERNEL64UC 8.04, KERNEL64NUC 7.22, KERNEL64NUC 7.22EXT
- SAP Web Dispatcher, Versions -7.22EXT, 7.53, 7.54, 7.77, 7.85, 7.89
- SAP Content Server, Versions -6.50, 7.53, 7.54
- SAP HANA Database, Version–2.0
- SAP Host Agent, Version–722
- SAP Extended Application Services and Runtime (XSA), Versions -SAP_EXTENDED_APP_SERVICES 1, XS_ADVANCED_RUNTIME 1.00
- SAPSSOEXT, Version–17
- SAP Business One, Version –10.0