Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
March 2024 notes
Summary and highlights of the month
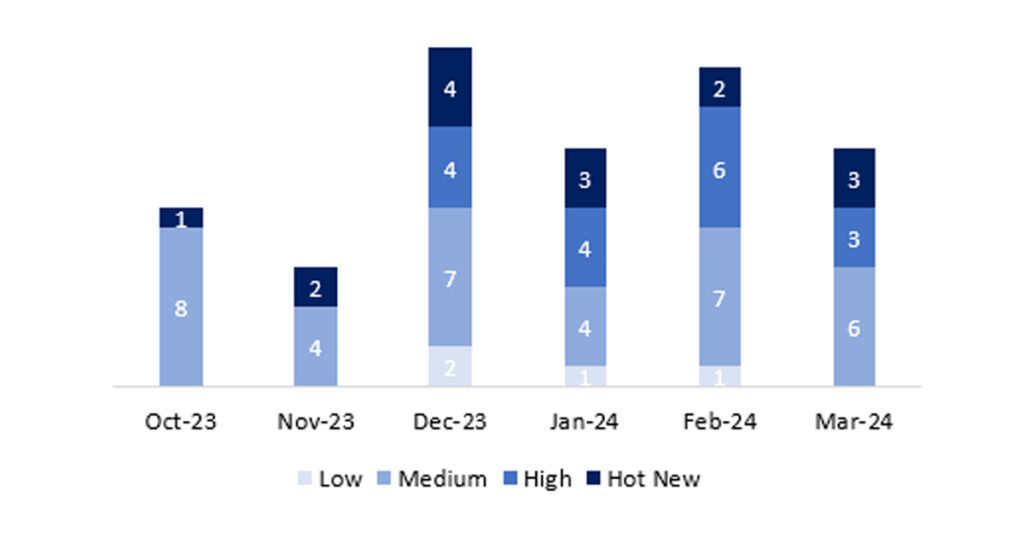
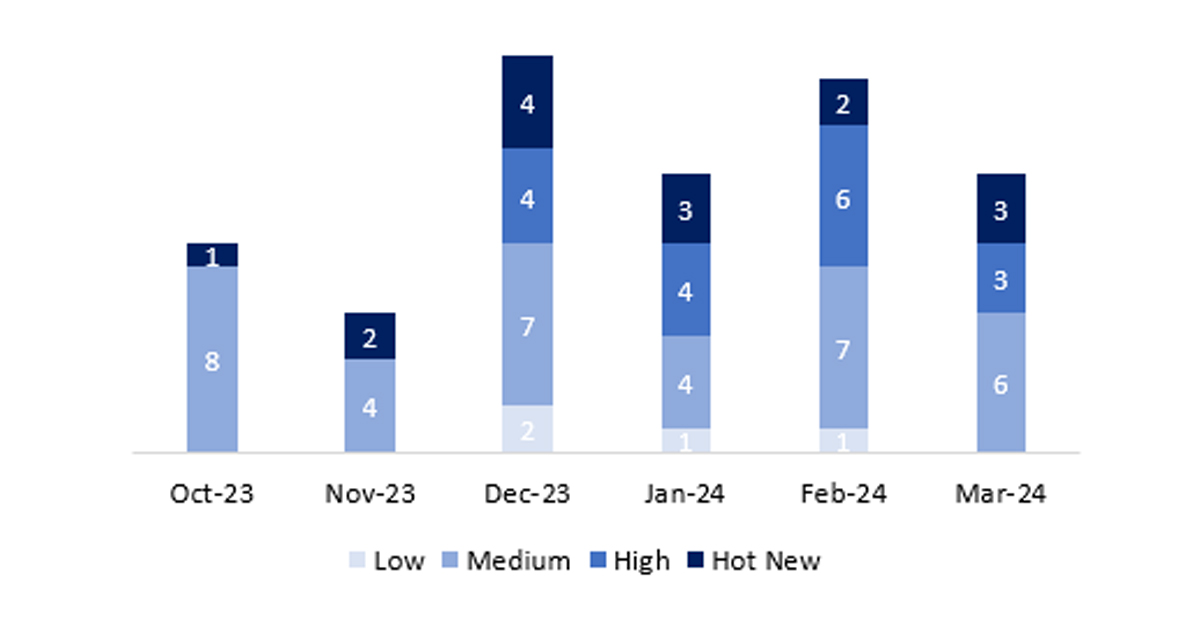
The total number of notes/patches was 12, which is 4 less than last month. The number of Hot News notes was 3, which is 1 more than the previous month. It is also worth mentioning that the number of high criticality notes has decreased compared to last month: 3 this month. As always, we will leave the medium and low severity notes unreviewed, but we will detail a total of 6 notes (all those with a CVSS of 7 or higher).
We have a total of 12 notes for the entire month (the 12 from Patch Tuesday, 10 new and 2 updates, which are 4 notes less than the last Patch Tuesday).
We will review in detail a total of 6 notes, the 3 HotNews of this month: 2 new and 1 update, and the 3 high severity notes: 2 of them new and 1 update (those with a CVSS equal to or greater than 7).
- The most critical note of the month (with a CVSS of 10) is an update to a usual HotNews related to “Google Chromium“.
- The next in criticality (with a CVSS of 9.4) is a HotNews related to “Code Injection vulnerability in applications built with SAP Build Apps“.
- The next in criticality (with a CVSS of 9.1) is a HotNews related to “Code Injection vulnerability in SAP NetWeaver AS Java“.
- The next in criticality (with a CVSS of 8.8) is an update of a note related to “Improper authentication in SAP Commerce Cloud“.
- The next in criticality (with CVSS of 7,5 and 7,2 , respectively) are related to “Denial of service (DOS) in SAP HANA XS Classic and HANA XS Advanced” and “Path Traversal Vulnerability in SAP BusinessObjects Business Intelligence Platform (Central Management Console)“.
- This month, the most predominant type is related to “Information Disclosure vulnerability” (3/12 on patch day).
In the graph, we can see the classification of the March notes, as well as the evolution and classification of the last 5 months (only the notes from Sec. Tuesday / Patch Day – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- Update -Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Code Injection vulnerability in applications built with SAP Build Apps (3425274): SAP Build Apps applications have a code injection vulnerability, allowing attackers to execute unauthorized commands. This can affect the confidentiality (low impact) and the integrity and availability (high impact) of the application. The solution is to rebuild the application in SAP Build Apps with version 4.9.145 or later. CVSS v3 Base Score: 9,4 / 10 [CVE-2019-10744].
- Code Injection vulnerability in SAP NetWeaver AS Java (Administrator Log Viewer plug-in) (3433192): The SAP NetWeaver Administrator AS Java Log Viewer add-on has a vulnerability that allows an attacker with elevated privileges to load potentially dangerous files, which can result in a command injection, leading to data compromise and impacting system availability. The solution involves restricting the types of files that can be uploaded after applying the Note. It is recommended to scan each file for threats and upgrade NW Application Server Java to a version or SP that addresses this issue.CVSS v3 Base Score: 9,1 / 10 [CVE-2024-22127].
- Update – Improper authentication in SAP Commerce Cloud (3346500): Certain configurations of SAP Commerce Cloud may accept an empty passphrase for user ID and passphrase authentication, allowing users to log into the system without a passphrase. This vulnerability only affects active user accounts that have an empty passphrase. Other user accounts that have a valid passphrase set are not affected. Note contains a workaround.CVSS v3 Base Score: 8,8 / 10 [CVE-2023-39439].
- Denial of service (DOS) in SAP HANA XS Classic and HANA XS Advanced (3410615): SAP HANA XS Classic and HANA XS Advanced are vulnerable to a denial of service (DOS) attack through a flood of HTTP/2 requests by an unauthenticated user. This attack can cause a significant impact on application availability, without affecting the confidentiality or integrity of the application. The solution for SAP HANA Database 2.0 is to implement revision 2.00.59.12 or newer, while for SAP HANA Extended Application Services Advanced (XS Advanced), it is recommended to implement version 1.1.8 or newer. CVSS v3 Base Score: 7,5 / 10 [CVE-2023-44487].
- Code Injection vulnerability in SAP IDES Systems (3414195):SAP BusinessObjects Business Intelligence Platform CMC employs a vulnerable version of Apache Struts, susceptible to CVE-2023-50164. A user with elevated privileges could exploit this vulnerability, causing a high impact on the confidentiality, integrity and availability of the application. The solution involves upgrading the affected open-source library to a non-vulnerable version. CVSS v3 Base Score: 7,2 / 10 [CVE-2023-50164].
Reference links
Other references, from SAP and Onapsis (March):
SAP Patch Day: March 2024 – Onapsis
Resources affected
- SAP Business Client, Versions – 6.5, 7.0, 7.70
- SAP Build Apps, Versions < 4.9.145
- SAP NetWeaver AS Java (Administrator Log Viewer plug-in), Version – 7.50
- SAP Commerce, Versions – HY_COM 2105, HY_COM 2205, COM_CLOUD 2211
- SAP HANA Database, Version – 2.0
- SAP HANA Extended Application Services Advanced (XS Advanced), Version – 1.0
- SAP BusinessObjects Business Intelligence Platform (Central Management Console), Versions – 4.3
- SAP NetWeaver AS ABAP applications based on SAPGUI for HTML (WebGUI), Versions – 7.89, 7.93
- NetWeaver (WSRM), Versions – 7.50
- SAP NetWeaver (Enterprise Portal), Version – 7.50
- SAP NetWeaver Process Integration (Support Web Pages), Versions – 7.50
- SAP Fiori Front End Server, Version – 605
- SAP ABAP Platform, Versions – 758, 795