Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
January 2024 notes
Summary and highlights of the month
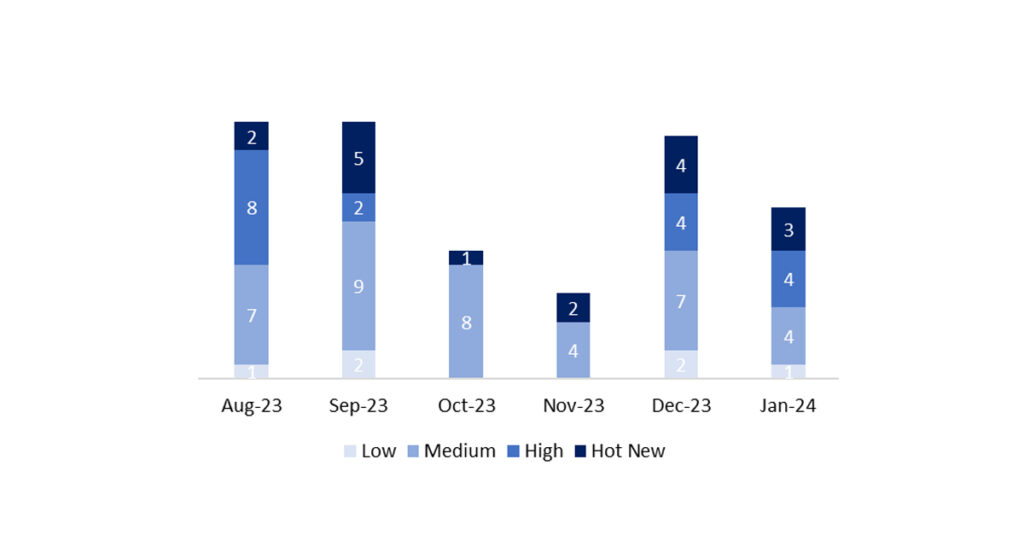
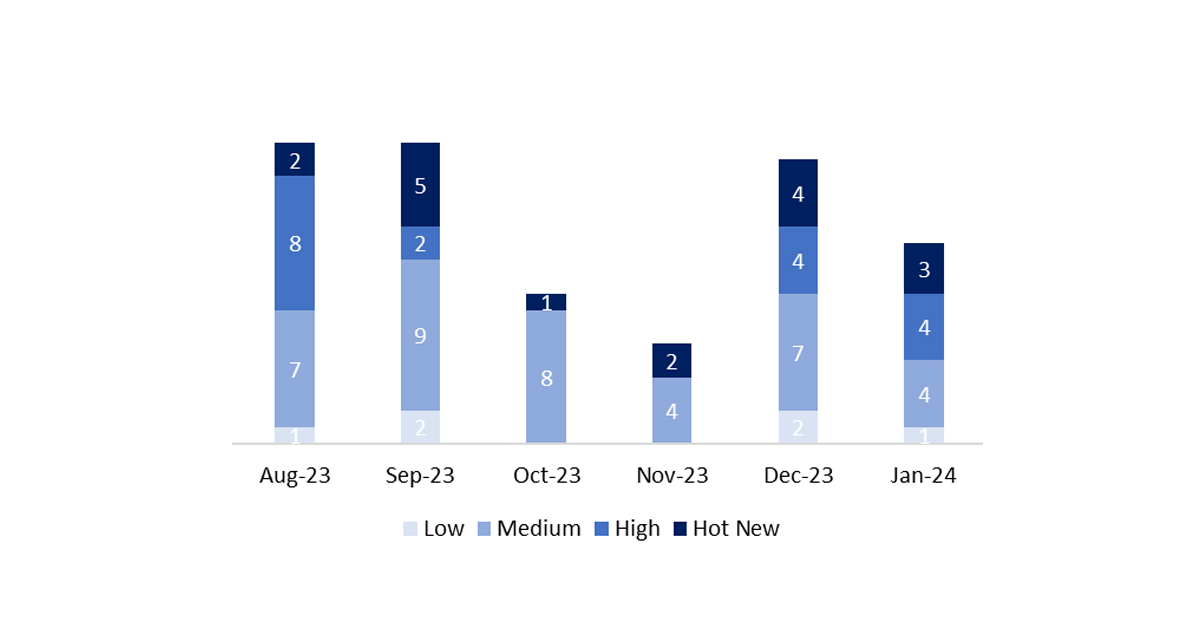
The total number of notes/patches this month was 12, which is 5 less than last month. The number of Hot News was 3, 1 less than last month. It’s also important to note that the number of high criticality notes remains the same as last month: 4 this month. As usual, we will leave the medium and low severity notes unreviewed, but we will detail a total of 7 notes (all those with a CVSS of 7 or higher).
We have a total of 12 notes for the entire month (the 12 from Patch Tuesday, 10 new and 2 updates, which are 5 notes fewer than the previous Patch Tuesday).
We will review in detail a total of 7 notes, the 3 HotNews of this month, 2 new and 1 update, and the 4 high notes, all 4 new (those with a CVSS score equal to or greater than 7).
- The most critical notes of the month (with a CVSS of 9,1) are 3 HotNews, 2 new and one update, one related to “Escalation of Privileges in SAP Business Technology Platform (BTP) Security Services Integration Libraries”, another with “Escalation of Privileges in applications developed through SAP Business Application Studio, SAP Web IDE Full-Stack and SAP Web IDE for SAP HANA” and the third with “Escalation of Privileges in SAP Edge Integration Cell“.
- The next in criticality (with a CVSS of 8,4), is a high note related to “Code Injection vulnerability in SAP Application Interface Framework (File Adapter)“.
- The next in criticality (with a CVSS of 7,5) is a high note related to “Denial of service (DOS) in SAP Web Dispatcher, SAP NetWeaver Application server ABAP, and ABAP Platform“.
- The following in criticality (with CVSS of 7,3 and 7,3 respectively) are related to “Information disclosure vulnerability in Microsoft Edge browser extension (SAP GUI connector for Microsoft Edge)” and “Improper Authorization check in SAP LT Replication Server“.
- This month, the most predominant type is related to “Escalation of Privileges” (3/12 on patch day).
In the graph, we can see the classification of the January notes, as well as the evolution and classification of the last 5 months (only the notes from Sec. Tuesday / Patch Day – by SAP).
Full details
The complete detail of the most relevant notes is as follows:
- Escalation of Privileges in applications developed through SAP Business Application Studio, SAP Web IDE Full-Stack and SAP Web IDE for SAP HANA (3412456): Under certain conditions, node.js applications created through SAP Business Application Studio, SAP Web IDE Full-Stack and SAP Web IDE for SAP HANA:, which are intended to be deployed in the SAP BTP or Cloud Foundry environment allow an escalation of privileges. CVSS v3 Base Score: 9,1/ 10 [CVE-2023-49583].
- Escalation of Privileges in SAP Edge Integration Cell Related CVEs (3413475): SAP BTP Security Services Integration Libraries and Programming Infrastructures using these libraries listed below allow under certain conditions an escalation of privileges. On successful exploitation, an unauthenticated attacker can obtain arbitrary permissions within the application. CVSS v3 Base Score: 9,1/ 10 (Multiple CVE´s).
- Update – Escalation of Privileges in SAP Business Technology Platform (BTP) Security Services Integration Libraries (3411067):SAP BTP Security Services Integration Libraries and Programming Infrastructures using these libraries listed below allow under certain conditions an escalation of privileges. On successful exploitation, an unauthenticated attacker can obtain arbitrary permissions within the application. CVSS v3 Base Score: 9,1 / 10 (Multiple CVE´s).
- Code Injection vulnerability in SAP Application Interface Framework (File Adapter) (3411869): In SAP Application Interface Framework File Adapter, a user with elevated privileges can use a function module to traverse multiple layers and execute operating system commands directly, being able to control the behavior of the application, impacting confidentiality, integrity and availability. CVSS v3 Base Score: 8,4/ 10 [CVE-2024-21737].
- Denial of service (DOS) in SAP Web Dispatcher, SAP NetWeaver Application server ABAP, and ABAP Platform (3389917):NetWeaver Application Server ABAP, and ABAP Platform allow an unauthenticated user to perform a DOS attack. This action may lead to flooding the memory and cause a high impact on the availability of the application. The vulnerability affects only the HTTP/2 protocol. CVSS v3 Base Score: 7,5 / 10 [CVE-2023-44487].
- Information Disclosure vulnerability in Microsoft Edge browser extension (SAP GUI connector for Microsoft Edge) (3386378): Under certain conditions the Microsoft Edge browser extension (SAP GUI connector for Microsoft Edge) allows an attacker to access highly sensitive information which would otherwise be restricted causing high impact on confidentiality.CVSS v3 Base Score: 7,4 / 10 [CVE-2024-22125].
- Improper Authorization check in SAP LT Replication Server (3407617): SAP LT Replication Server does not perform the required authorization checks. This could allow an attacker with elevated privileges to perform unwanted actions. This issue may occur for SAP LT Replication Server running on SAP S/4HANA 1809 to 2023. CVSS v3 Base Score: 7,3/ 10 [CVE-2024-21735].
Reference links
Other references, from SAP and Onapsis (January):
SAP Patch Day: January 2024 | Onapsis
Resources affected
- @sap/approuter, Versions –14.4.2
- @sap/xssec, Versions –< 3.6.0
- cloud-security-services-integration-library, Versions –< 2.17.0 & from 3.0.0 before 3.3.0
- github.com/sap/cloud-security-client-go, Versions -< 0.17.0
- Microsoft Edge browser extension (SAP GUI connector for Microsoft Edge),Version -1.0
- SAP Application Interface Framework (File Adapter), Version –702
- SAP Edge Integration Cell, Versions >= 8.9.13
- SAP LT Replication Server,Versions–S4CORE 103, S4CORE 104, S4CORE 105, S4CORE 106, S4CORE 107, S4CORE 108
- SAP NetWeaver AS ABAP and ABAP Platform, Versions-KRNL64UC 7.53, KERNEL 7.53, KERNEL 7.77, KERNEL 7.85, KERNEL 7.89, KERNEL 7.54, KERNEL 7.94, KERNEL 7.93, KERNEL 7.95
- SAP Web Dispatcher, Versions–WEBDISP 7.53, WEBDISP 7.54, WEBDISP 7.77, WEBDISP 7.85, WEBDISP 7.89, WEBDISP 7.90, WEBDISP 7.94, WEBDISP 7.95,