Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
August 2021 notes
Summary and highlights of the month
The total number of notes/patches has increased compared to last month. In addition to this increase in the total number of notes, the number of Hot News has also increased, with 2 notes last month compared to 3 in August. On the other hand, it is worth mentioning that the number of high criticality notes has increased from 2 to 6 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 9 scores (all those with a CVSS of 7 or higher).
We have a total of 19 notes for the whole month, 3 more than last July (15 from Patch Tuesday, 14 new and 1 updates, being the same as last month).
We have 3 new Hot News, being the total of 3 in this month that stand out for their high CVVS. In addition we will review in detail 6 of the total of 6 high notes (those with CVSS greater than or equal to 7), all of them new notes.
- The most critical scores of the month (with CVSS 9.9) are two. One of Unrestricted File Upload vulnerability affecting SAP Business One and the other of Server Side Request Forgery vulnerability affecting SAP NetWeaver Development Infrastructure (Component Build Service).
- Next in criticality (CVSS 9.1) is a SQL Injection vulnerability in SAP NZDT Row Count Reconciliation.
- From there, we find the 6 notes of high priority, the most relevant with a CVSS of 8.8 being a new note of Missing Authentication check in SAP Web Dispatcher. The rest (10) are of medium and low level, and we will not see them in detail.
- This month the most predominant types are “Cross-Site Scripting (XSS)” (5/19 and 4/15 in patch day) and “Missing Authorization Check” (3/19 and 2/15 in patch day).
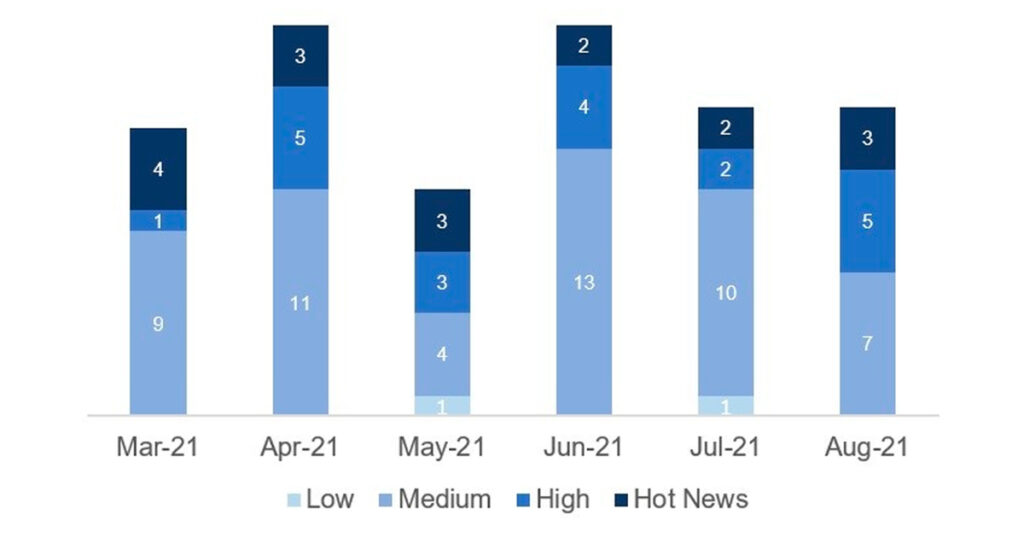
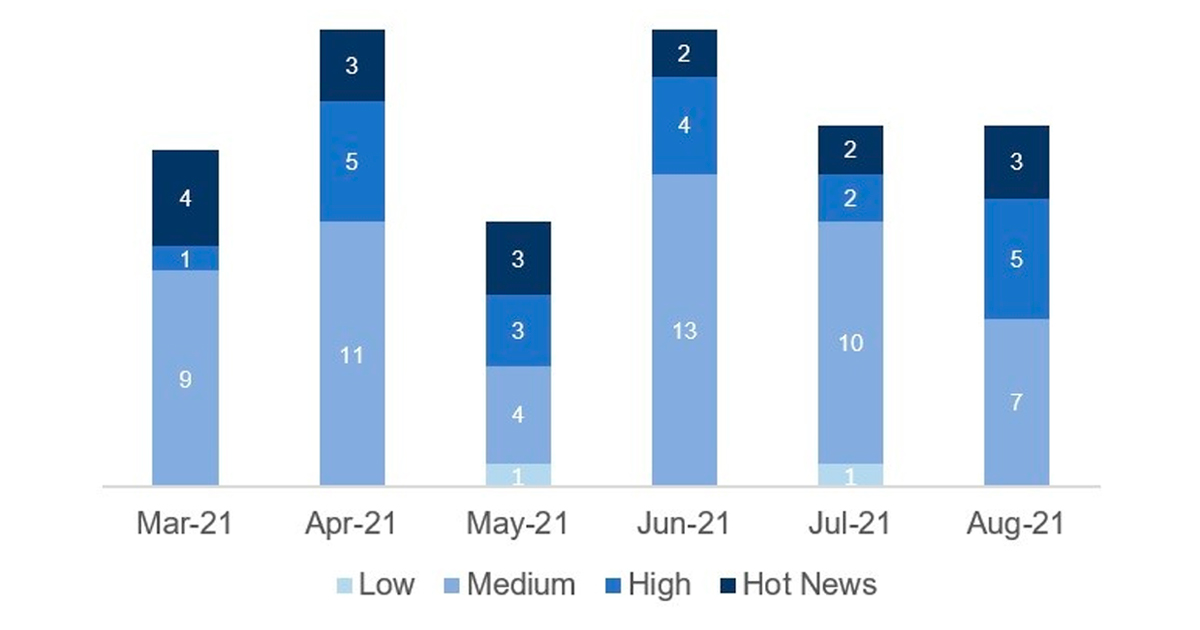
In the graph (post August 2021 from SAP) we can see the classification of the August notes in addition to the evolution and classification of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
 Full details
Full details
The full details of the most relevant notes are as follows:
- Unrestricted File Upload vulnerability in SAP Business One (3071984): It patches a vulnerability in SAP Business One that allows an attacker to upload files, including script files, to the server. The only reason it does not have a CVSS 10 rating is because it needs a minimum set of authorizations. Fortunately, there is a workaround available for customers who can not immediately apply the related hotfix—they can simply deactivate the affected functionality. But, as always, SAP emphasizes that this workaround should be considered a temporary fix rather than a permanent solution. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-33698).
- Server Side Request Forgery vulnerability in SAP NetWeaver Development Infrastructure (Component Build Service) (3072955): A servlet of the Component Build Service in SAP NetWeaver Development Infrastructure (SAP NWDI) was exposed to the outside, allowing attackers to perform proxy attacks by sending crafted queries. According to SAP, the impact of this vulnerability depends on whether or not SAP NetWeaver Development Infrastructure (NWDI) runs on the intranet or Internet. If it is running on the Internet, this vulnerability “could completely compromise sensitive data residing on the server, and impact its availability”. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-33690).
- SQL Injection vulnerability in SAP NZDT Row Count Reconciliation (3078312): It patches an SQL Injection vulnerability in the Near Zero Downtime (NZDT) tool of the DMIS Mobile Plug-In or SAP S/4HANA. The tool is used by SAP’s corresponding nZDT service for time-optimized system upgrades and system conversions. When using the nZDT service, the maintenance is performed on a clone of the production system. All changes are recorded and transferred to the clone after the maintenance tasks are completed. During the final downtime, only a few activities are executed, including a switch of the production to the new system (clone). In addition to the correction instructions that come with the note, there is also a workaround available for all customers who have activated the Unified Connectivity (UCON) runtime check. The workaround for the vulnerability within the tool used by the nZDT service is to not assign the used remote-enabled function module to any communication assembly (CA) in UCON. CVSS v3 Base Score: 9.1 / 10 (CVE-2021-33701).
- Missing Authentication check in SAP Web Dispatcher (3057378): SAP Web Dispatcher does not perform any authentication checks for functionalities that require user identity. It contains a programming error that affects authentication in all SAP application systems that are accessed through the SAP Web Dispatcher if authentication based on X.509 client certificates is used. In such scenarios, an attacker with network access can execute functions in SAP application systems with any user identity that has a mapping to an X.509 certificate. Impacts of Missing Authentication check are: read, modify or delete sensitive information and access administrative or other privileged functionalities. CVSS v3 Base Score: 8.8 / 10.
- Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Enterprise Portal (3073681): It patches a Cross-Site Scripting (XSS) vulnerability caused by one of the portal’s servlets. An insufficient sanitization allows the injection of Javascript into the corresponding web page. If a victim navigates to an infected servlet, the vulnerable script is executed in their browser. Although the impact on the system’s confidentiality, integrity and availability is high, the fact that it is highly complex and requires user interaction for the exploit to succeed, merits a lower CVSS score. CVSS v3 Base Score: 8.3 / 10 (CVE-2021-33702).
- Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Enterprise Portal (3072920): It patches a very similar vulnerability in another servlet of the SAP Enterprise Portal. So, it’s no surprise that it has also the same CVSS value and vector assigned as note #3073681. CVSS v3 Base Score: 8.3 / 10 (CVE-2021-33703).
- Server-Side Request Forgery (SSRF) vulnerability in SAP NetWeaver Enterprise Portal (3074844): It patches a Server Side Request Forgery (SSRF) vulnerability in one of the design time components of the SAP Enterprise Portal. It allows an unauthenticated attacker to craft a malicious url which, when clicked by a user, can make any type of request (e.g. POST, GET) to any internal or external server. CVSS v3 Base Score: 8.1 / 10 (CVE-2021-33705).
- Task Hijacking in SAP Fiori Client Native Mobile for Android (3067219): Task Hijacking in SAP Fiori client affects the applications running on Android devices due to a misconfiguration in their AndroidManifest.xml with their Task Control features. This allows attackers/malware to takeover legitimate apps and steal user’s sensitive information. The Solution: SAP will provide the new version of Kapsel SDK and Fiori Client to fix this issue. CVSS v3 Base Score: 7.6 / 10 (CVE-2021-33699).
- Missing Authentication check in SAP Business One (3073325): SAP Business One allows a local attacker with access to the victim’s browser under certain circumstances to login as the victim without knowing his/her password. The attacker could so obtain highly sensitive information which the attacker could use to take substantial control of the vulnerable application. The Solution: Disable the related vulnerability function. Customers need implement or upgrade to SAP Business One 10.0 PL2105 Hotfix1. CVSS v3 Base Score: 7.0 / 10 (CVE-2021-33700).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for August:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-agosto-2021
Other references, from SAP and Onapsis (August):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=582222806
https://onapsis.com/blog/sap-security-patch-day-august-2021
Resources affected
- DMIS Mobile Plug-In, versiones DMIS 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 710, 2011_1_731, 710, 2011_1_752 y 2020.
- SAP Business One, versión 10.0;
- SAP BusinessObjects Business Intelligence Platform (Crystal Report, SAPUI5), versiones 420 y 430;
- SAP Cloud Connector, versión 2.0;
- SAP Fiori Client Native Mobile para Android, versión 3.2;
- SAP NetWeaver:
-
- (Knowledge Management), versiones 7.30, 7.31, 7.40 y 7.50;
- AS ABAP and ABAP Platform (SRM_RFC_SUBMIT_REPORT), versiones 700, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754 y 755 ;
- Development Infrastructure (Component Build Service), versiones 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- Development Infrastructure (Notification Service), versiones 7.31, 7.40 y 7.50;
- Enterprise Portal (Application Extensions), versiones 7.30, 7.31, 7.40 y 7.50;
- Enterprise Portal, versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP S/4HANA, versiones SAPSCORE 125, S4CORE 102, 102, 103, 104 y 105;