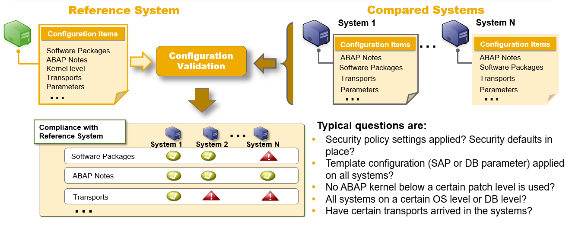
Configuration Validation is an SAP Solution Manager tool that checks if SAP systems are configured consistently with the company’s established requirements.
The tool works by comparing one or more systems against a reference system, which can be an existing real system or a virtual system called Target System.
Target System
A Target System is a virtual system containing configuration data used as a reference for comparison with other systems.
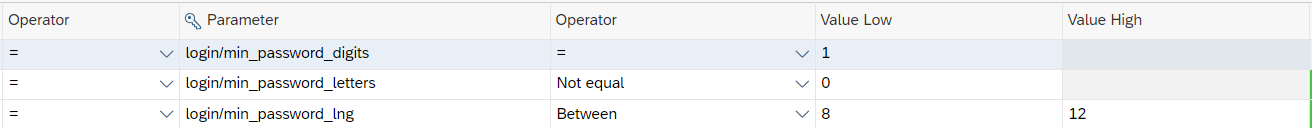
These data are stored in Configuration Stores, which collect fields or parameters for Configuration Validation to analyze systems. Stores are configurable, allowing selection of fields or parameters to review, the value to check, and the operator to apply to the parameter (equal to, between, different from, etc.).
Configuration Validation offers several options for creating a new Target System. They can be created as a copy of an existing system, meaning they will contain the same Stores and values as the original.
Another option is to import preconfigured Target Systems from the SAP SECURITY BASELINE, which has SAP-recommended values based on best practices. These preconfigured Target Systems are also modifiable to suit specific organizational environments and requirements.
The Target Systems provided by SAP are classified by a unique indicator, consisting of three parts. The first is the level of criticality defined by a numeric value from 1 to 3. The most critical value (1) refers to high-impact security needs, the standard requirements (2) recommended by SAP that should be covered in all systems, and finally, the so-called Extended (3), which are more specific requirements that organizations should evaluate for inclusion.
The second part of the structure provides information about the type of technology, such as ABAP (A), JAVA (J), HANA (H), BTP Platform (P), and Other (O) referring to Web Dispatcher or SAPGUI.
The third part consists of a unique mnemonic identifier for the requirement.
In the example image, a Critical Target System (1) for an ABAP (A) system and referred to the Password Policy (PWDPOL) is shown.
The tool also offers the possibility of creating a broader single Target System from the union of individual Target Systems of the SAP Security Baseline. This union is done by running the DIAGCV_MERGE_TARGET_SYSTEMS program in the Solution Manager backend system. It is also possible to transport Target Systems between environments using the DIAGCV_TRANSPORT_TARGET_SYSTEM program.
Comparison Lists
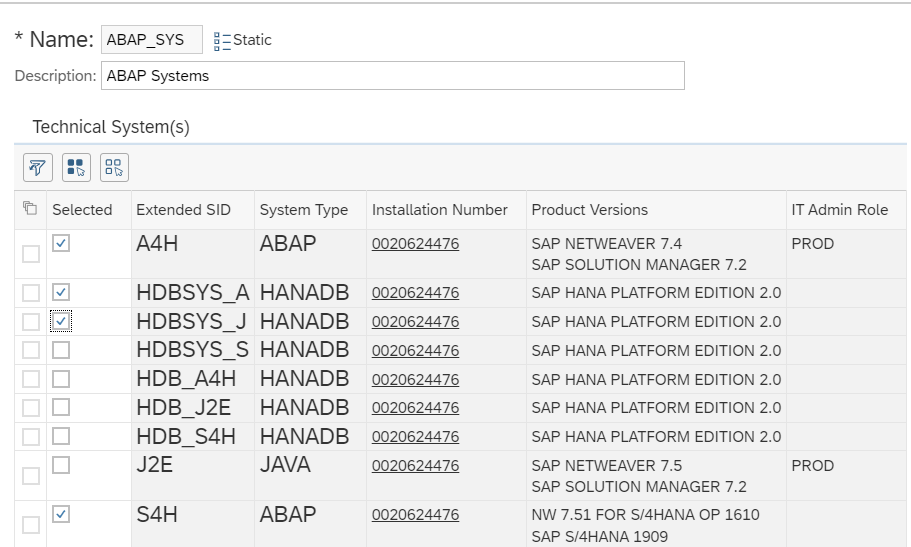
Comparison lists allow grouping different systems to simultaneously obtain configuration information from all of them. It’s necessary to define the systems that should be periodically compared with the reference systems. These lists contain the comparison systems, not the reference system.
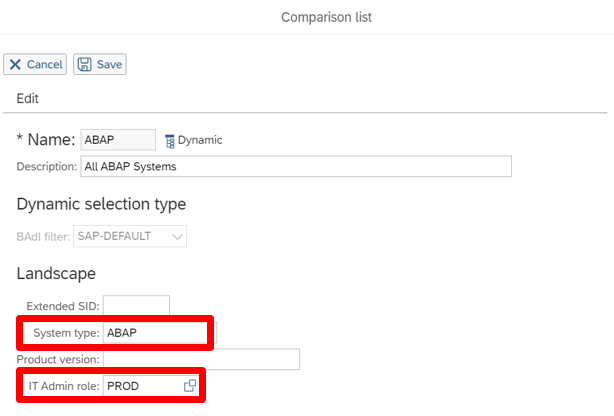
There are 2 types of comparison lists:
Static lists, where systems to include in a closed list are selected:
Dynamic lists, usually containing systems from the same environment (e.g., production environments) or of the same type (e.g., ABAP), allowing the list to be automatically updated to incorporate new systems each time a security analysis is launched.
Report Creation and Results Visualization
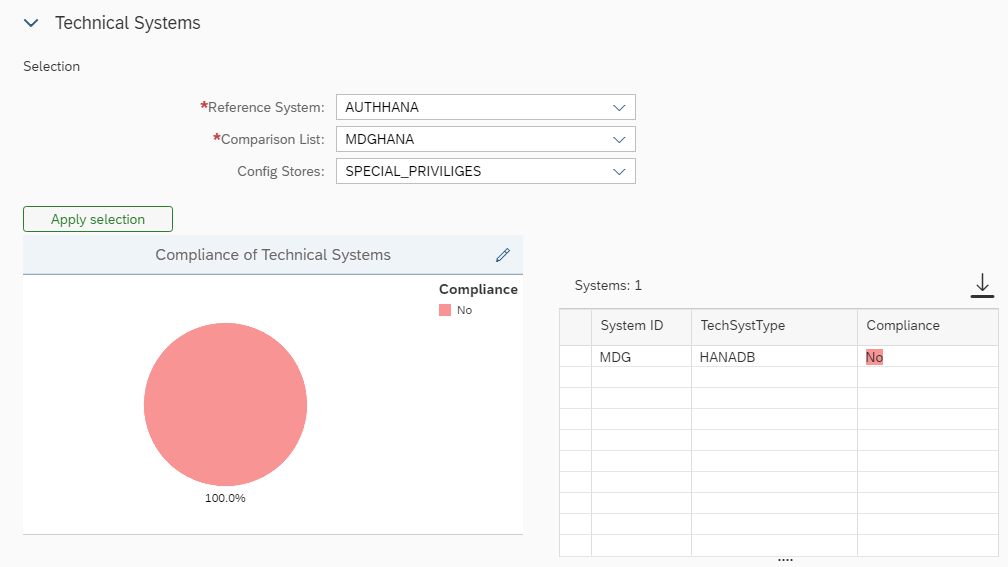
Reports will show compliant or non-compliant results based on the set of rules defined in the Target Systems.
The Configuration Validation Reporting application allows real-time analysis to verify the current status of a Target System or a comparison list.
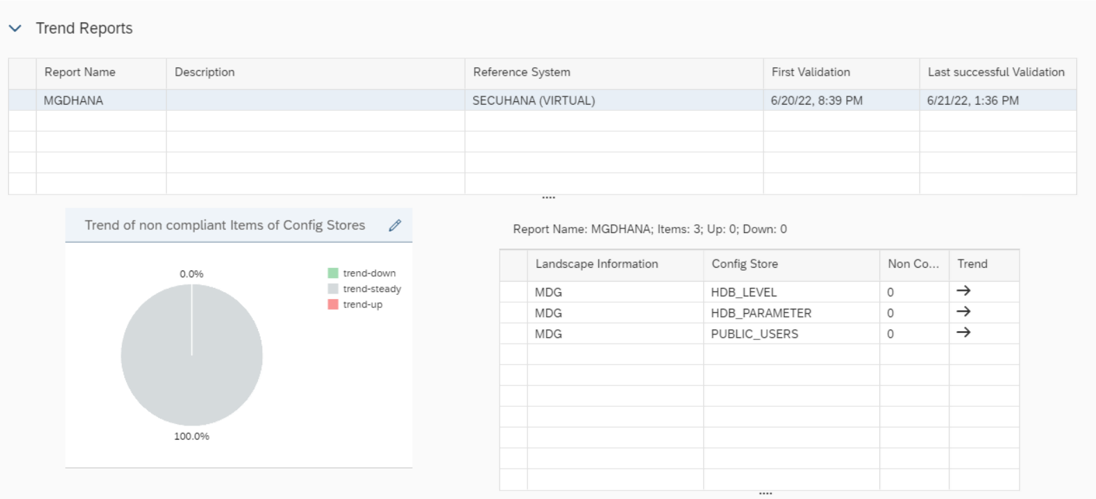
Configuration Validation enables the creation of ad-hoc reports to compare the configuration of a system or a list of systems with a Target System, allowing regular scheduling of report execution for subsequent trend analysis and compliance checking over time.
Email Notification
Configuration Validation can send results via email.
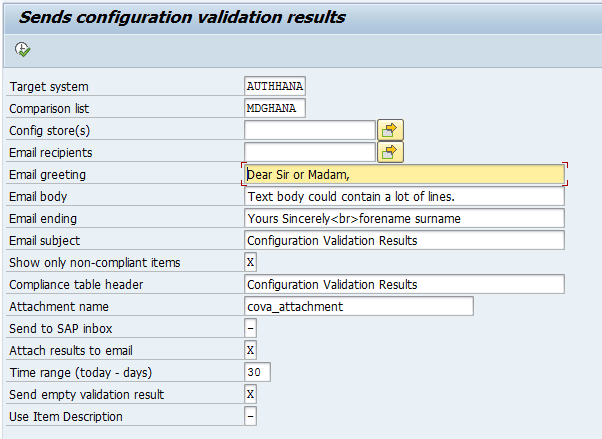
To set this up, the DIAGCV_SEND_CONFIG_VALIDATION program must be run in the backend.
The program has the following fields:
- Target System: Select any of the previously created Target Systems.
- Comparison List: Select the corresponding comparison list.
- Config store(s): Select Stores, allows multiple selection.
- Email recipients: Recipient, email of the person receiving the report, allows multiple selection.
- Email greeting: Email header, can be customized with HTML code.
- Email body: Message body, can be customized with HTML code.
- Email ending: Email closing, can be customized with HTML code.
- Compliance table header: Report table header, can be customized with HTML code.
- Attachment name: Name of the attachment.
- Send to SAP inbox: Send to SAP inbox, several possible values, “-” (default), does not send, “x” send to the sender.
- Attach results to email: “x” (default), results attached, ‘ ‘ results in the body of the email.
- Time range (today – days): Number of days (only valid for System Recommendations).
- Send empty validation result: “x” (default) sends all controls, ‘ ‘ does not send empty ones.
- Use Item Description: “-” (default) uses the Store Group name, “x” displays the description and criticality defined in the Store configuration.
- The field Only non-compliant items: allows configuring the type of report to be sent, the value “+” implies a complete result (controls that comply, controls that do not comply, controls not found, and controls not evaluated, the value “X” (controls that comply) and the value ” ” (controls that comply and controls that do not comply).
For a complete analysis, it was necessary to use the value “+”, which includes unevaluated controls from other Target Systems. Following a consultation Inprosec made to SAP, an improvement was published through note 3149011 – Report DIAGCV_SEND_CONFIG_VALIDATION ignores the input field “Only non-compliant items” . Now, the value “V” can be used to show controls that comply, controls that do not comply, and controls not found.