Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Diciembre 2021
Resumen y highlights del Mes
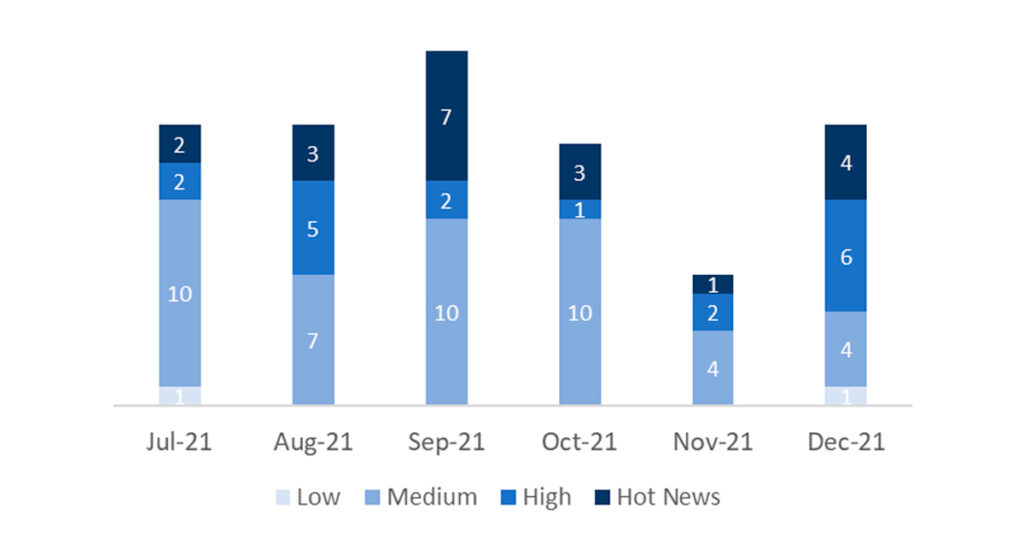
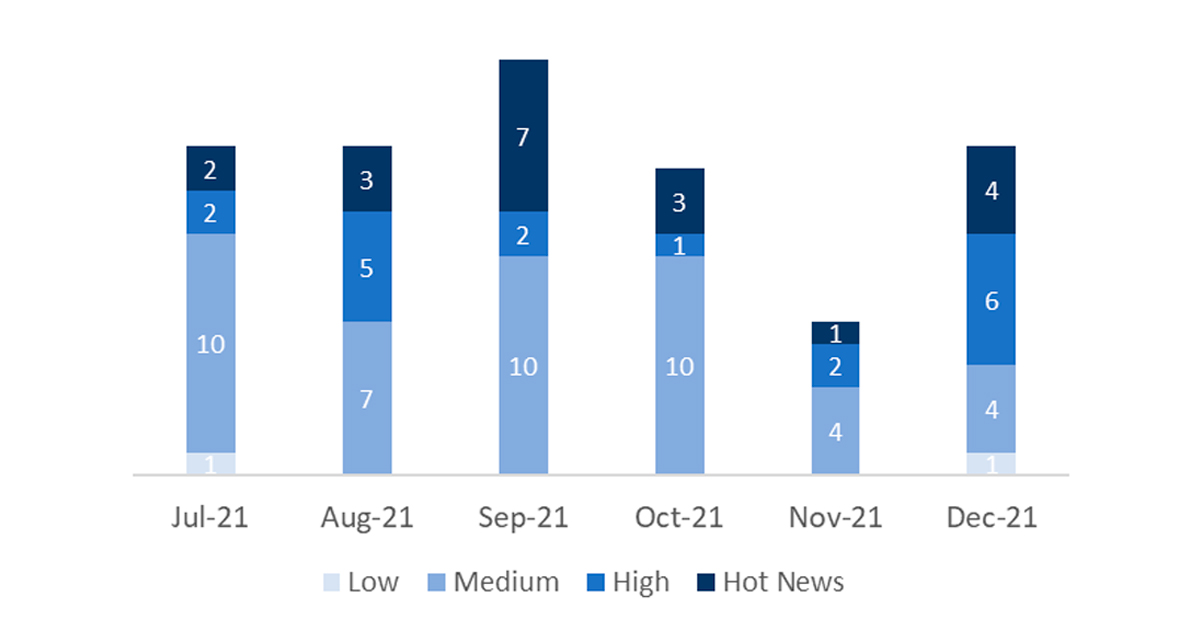
El número total de notas/parches ha aumentado con respecto al último mes. Además de esta subida en el número de notas totales, el número de Hot News también aumenta, siendo 1 la que encontrábamos el mes pasado con respecto a las 4 existentes en Diciembre. Por otro lado, cabe destacar, que aumentan el número de notas de criticidad alta pasando de 3 a 6 en este mes. Como siempre, dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 10 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 21 notas para todo el mes, 10 más que el pasado Noviembre (15 del patch Tuesday, 11 nuevas y 4 actualizaciones, siendo 8 más que el pasado mes).
Tenemos 4 notas críticas (Hot News), 2 nuevas y 2 actualizaciones, en este mes que destacan por su alto CVVS. Además revisaremos en detalle 6 del total de 6 notas altas (aquellas de CVSS mayor o igual a 7) donde este mes destaca que serían todas notas nuevas.
- La nota más crítica del mes (con CVSS 10) sería la actualización de “Browser Control Chromium Delivered with SAP Business Client (2622660)”.
- Por otro lado, localizamos también otras 3 notas de criticidad muy alta (Hot News), todas con un CVSS de 9.9, relacionadas con vulnerabilidades de Code Execution, Code Injection y SQL Injection, que afectan a SAP Commerce, SAP ABAP Server & ABAP Platform y SAP NZDT Mapping Table Framework, respectivamente.
- A partir de ahí, existen 6 notas de criticidad alta (high priority), ), siendo las más relevantes con un CVSS de 8.8 dos notas nuevas de SQL Injection y Cross-Site Scripting, que en este caso afectan a SAP Commerce y SAP Knowledge Warehouse. El resto (11) son de nivel medio y bajo, y no las veremos en detalle.
- Este mes el tipo más predominante es el de “Missing Authorization Check” (5/21 y 1/15 en patch day), seguido de Cross-Site Scripting (XSS) (3/21 y 2/15 en patch day).
En la gráfica (post Diciembre 2021 de SAP) podemos ver la clasificación de las notas de Diciembre además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): It provides a SAP Business Client Patch with the latest tested Chromium fixes. SAP Business Client customers already know that updates of this note always contain important fixes that must be addressed. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. CVSS v3 Base Score: 10 / 10 .
- Code Execution vulnerability in SAP Commerce, localization for China (3109577): SAP Commerce, localization for China uses open source software component versions having multiple vulnerabilities as mentioned below. Consequently, this functionality is potentially at risk of code execution attack. The solution would be to update the SAP Commerce to patch 1905.32 or above. If your installation of SAP Commerce, localization for China package is 2001, just download the SP00 patch level 01 for SAP Commerce, localization for China package. Otherwise, upgrade your SAP Commerce, localization for China package to 2001 first. CVSS v3 Base Score: 9.9 / 10 (Multiple CVEs).
- Code Injection vulnerability in SAP ABAP Server & ABAP Platform (Translation Tools) (3119365): This note patches a Code Injection vulnerability, where an attacker with low privileges can exploit the weakness in internally used text extraction reports (Translation Tools) which will enable the execution of arbitrary commands in the background. The attacker could thereby control the behaviour of the application compromising all its data. To fix the issue it is necessary to implement the note so coding is deactivated and there would be no impact on existing funcionality. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-44231).
- Update – SQL Injection vulnerability in SAP NZDT Mapping Table Framework (3089831): SAP has made minor textual change in the Symptom section. There have not been any changes done which require customer action. This note patches SQL Injection vulnerabilities in RFC-enabled function modules of the Near Zero Downtime (NZDT) Mapping Table framework used during system upgrades and migrations. An improper input sanitization allows an authenticated user with certain specific privileges to remotely call NZDT function modules listed in Solution Section to execute manipulated query or inject ABAP code to gain access to Backend Database. On successful exploitation the threat actor could completely compromise confidentiality, integrity and availability of the system. This note provides a patch for this vulnerability which leads to a complete or partial deactivation of the affected function modules. As a workaround, customers with activated Unified Connectivity (UCON) runtime checks can also deactivate the affected function modules manually. Important: Independent of which method is used to patch the vulnerabilities, they both result in making the product SAP Test Data Migration Server unusable. Please follow the steps described in SAP Note 3094474 in order to re-enable «SAP Test Data Migration Server». CVSS v3 Base Score: 9.9 / 10 (CVE-2021-38176]).
- SQL Injection vulnerability in SAP Commerce (3114134): If SAP Commerce is configured to use an Oracle database and if a query is created using the flexible search java api with a parametrized «in» clause, SAP Commerce allows attacker to execute crafted database queries, exposing backend database. The vulnerability is present if the parametrized «in» clause accepts more than 1000 values. The problem can affect any kind of extension using the flexible search api with an «in» clause with partially untrusted input and potentially some internal components of the platform when using an Oracle database. SAP Commerce addresses this vulnerability by properly escaping any value passed to parametrized «in» clause when handling flexible search queries having more than 1000 values used in this clause. CVSS v3 Base Score: 8.8 / 10. (CVE-2021-42064)
- Cross-Site Scripting (XSS) vulnerability in SAP Knowledge Warehouse (3102769): A security vulnerability has been discovered in the SAP Knowledge Warehouse (SAP KW). The usage of one SAP KW component within a Web browser enables unauthorized attackers to conduct XSS attacks, which might lead to disclose sensitive data. The displaying component of SAP KW did not sufficiently validate and encode input parameters, resulting in a reflected cross-site scripting issue. Important: The security breach might also occur if you do not actively use the displaying component of SAP KW at all. Simply the existence of the component on your landscape is sufficient. To solve the issue, please implement the Support Packages and Patches referenced by this SAP Note, so the parameters will be properly validated and encoded to prevent a successful XSS attack. CVSS v3 Base Score: 8.8 / 10. (CVE-2021-42063)
- Code Injection vulnerability in utility class for SAP NetWeaver AS ABAP (3123196): Two methods of a utility class in SAP NetWeaver AS ABAP allows an attacker with high privileges and has direct access to SAP System, to inject code when executing with transaction (SE24 – Class Builder). This could allow execution of arbitrary commands on the operating system, that could highly impact the Confidentiality, Integrity and Availability of the system. The issue appears if the user has permissions to use SE24/SE80 and execute development objects (authorization object = S_DEVELOP with fields OBJTYPE = CLAS and ACTVT = 16 ‘Execute’), and the compromised utility class is exclusively used for license bound SAP tool Post-Copy Automation (PCA) and has no impact on standard functionality. With the fix the functionality is completely removed and directly integrated into the class where it is executed without the possibility to pass any parameter. There are two options to fix the issue: the first one would be that no action is needed when the user has no permission to execute development objects (authorization object = S_DEVELOP with fields OBJTYPE = CLAS and ACTVT = 16 ‘Execute’) through transactions SE24/SE80, the other one would be to implement the note with SNOTE to remove the coding. As the functionality is used for Post-Copy Automation (PCA) which is integated into SAP Basis for older releases/sps some dependent notes have to be implemented. CVSS v3 Base Score: 8.4 / 10. (CVE-2021-44235)
- Denial of service (DOS) in the SAP SuccessFactors Mobile Application for Android devices (3077635): A vulnerability has been identified in SAP SuccessFactors Mobile Application for Android, which allows an attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service, which can lead to denial of service. The vulnerability is related to Android implementation methods that are widely used across Android mobile applications, and such methods are embedded into the SAP SuccessFactors mobile application. These Android methods begin executing once the user accesses their profile on the mobile application. While executing, it can also pick up the activities from other Android applications that are running in the background of the user’s device and are using the same types of methods in the application. Such vulnerability can also lead to phishing attack that can be used for staging other types of attacks. This vulnerability impacts users who are using the Android mobile application version released previous to 6.32.1. To fix the issue, download the latest version of the SAP SuccessFactors Android mobile application so the organization is not at risk of any threats highlighted from this vulnerability. CVSS v3 Base Score: 7.8 / 10 (CVE-2021-40498).
- Directory Traversal vulnerability in SAF-T Framework (3124094): SAF-T Framework Transaction SAFTN_G allows an attacker to exploit insufficient validation of path information provided by normal user, leading to full server directory access. The attacker can see the whole filesystem structure but cannot overwrite, delete, or corrupt arbitrary files on the server. To fix this issue, the F4 search help of field File Name in transaction SAFTN_G will be removed. Nevertheless, there are still other three possibilities for end-users to enter the file name. CVSS v3 Base Score: 7.7 / 10 (CVE-2021-44232).
- Denial of service (DOS) in SAP Commerce (3113593): The library jsoup used in SAP Commerce may be vulnerable to DOS attacks. jsoup is used to sanitize various product related metadata in b2caccelerator. A user with write access to product metadata could exploit this vulnerability. The impacts of the vulnerability would be long response delays and service interruptions, thus degrading the service quality experienced by legitimate users and a direct impact on availability. This vulnerability affects any SAP Commerce installation using the B2C Accelerator. SAP Commerce addresses this vulnerability by upgrading jsoup, which does not contain the vulnerability. The Software Downloads of these or later patches are available in the SAP Support Portal. As a workaround (not permanent solution), to minimize the impact, restrictions to product related field length could be implemented to limit the size of inputs sent to jsoup. CVSS v3 Base Score: 7.5 / 10.
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para el mes de Diciembre:
Otras referencias, en inglés de SAP y Onapsis (Diciembre):
https://wiki.scn.sap.com/wiki/display/PSR/SAP+Security+Patch+Day+-+December+2021
https://onapsis.com/blog/sap-security-patch-day-december-2021-patch-day-shadow-log4j
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAF-T Framework, versiones SAP_FIN 617, 618, 720, 730, SAP_APPL 600, 602, 603, 604, 605, 606, S4CORE 102, 103, 104 y 105;
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP ABAP Server & ABAP Platform (Translation Tools), versiones 701, 740,750,751,752,753,754,755,756 y 804;
- SAP Business Client, versión 6.5;
- SAP BusinessObjects Business Intelligence Platform, versión 420;
- SAP Commerce, localization for China, versión 2001;
- SAP Commerce, versiones 1905, 2005, 2105 y 2011;
- SAP GRC Access Control, versiones V1100_700, V1100_731 y V1200_750.
- SAP Knowledge Warehouse, versiones 7.30, 7.31, 7.40 y 7.50;
- SAP Landscape Transformation, versión 2.0;
- SAP LT Replication Server, versiones 2.0 y 3.0;
- SAP LTRS for S/4HANA, versión 1.0;
- SAP NetWeaver AS ABAP, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755 y 756;
- SAP S/4HANA, versiones 1511, 1610, 1709, 1809, 1909, 2020 y 2021;
- SAP SuccessFactors Mobile Application (para Android), versiones <2108;
- SAP Test Data Migration Server, versión 4.0;
- SAP UI 700, versiones 2.0;
- SAP UI, versiones 7.5, 7.51, 7.52, 7.53 y 7.54;
- SAP Web Dispatcher and Internet Communication Manager, versiones KRNL32NUC 7.21, 7.21EXT, 7.22, 7.22EXT, KRNL32UC 7.21, 7.21EXT, 7.22, 7.22EXT, KRNL64NUC 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49, KRNL64UC 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49, 7.53, 7.73, WEBDISP 7.53, 7.73, 7.77, 7.81, 7.82, 7.83, KERNEL 7.21, 7.22, 7.49, 7.53, 7.73, 7.77, 7.81, 7.82 y 7.83;