Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Enero 2023
Resumen y highlights del Mes
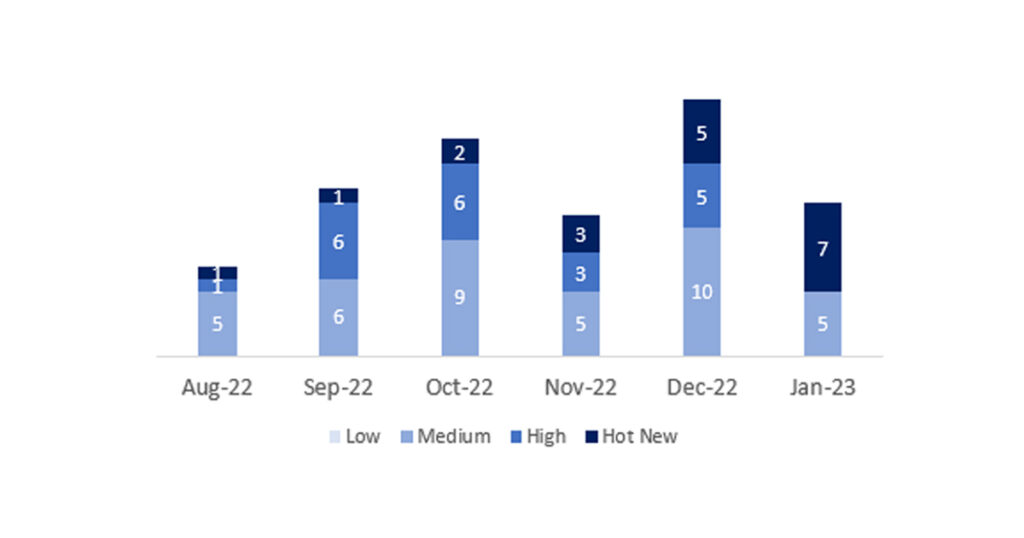
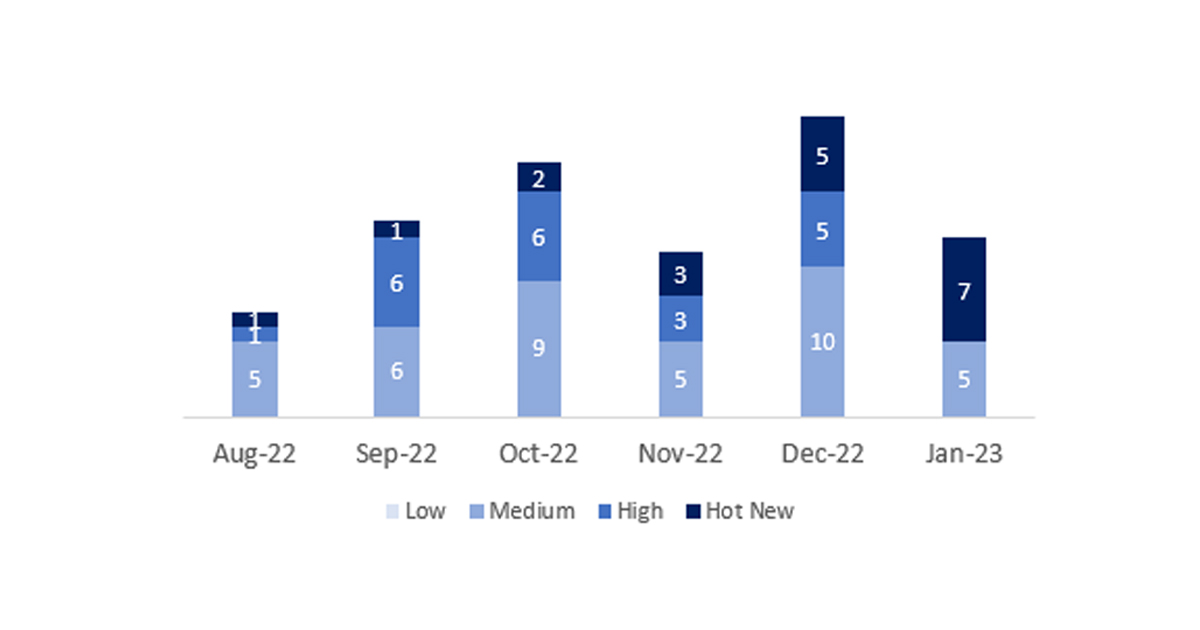
El número total de notas/parches ha sido de 12, 8 menos que el mes pasado. El número de Hot News aumenta, pasando de 5 a 7 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta disminuye, ya que, no hay ninguna este mes. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 7 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 12 notas para todo el mes (las 12 del patch Tuesday, 9 nuevas y 3 actualizaciones, son 7 notas menos que el pasado mes).
Revisaremos en detalle las 7 HotNews, 4 de las 7 HotNews son nuevas:
- Las notas más críticas del mes (con CVSS 9,9) son 4 HotNews, 2 nuevas, una relacionada con Business Planning and Consolidation, “SQL Injection vulnerability in SAP Business Planning and Consolidation MS” y la otra con Business Intelligence Platform,“Code Injection vulnerability in SAP BusinessObjects Business Intelligence platform”, las siguientes 2 notas, son actualizaciones, una relacionada con “Improper access control in SAP NetWeaver Process Integration”, actualización de una nota publicada en el Patch Day de diciembre 2022, la otra nota actualizada está relacionada con Business Intelligence Platform “Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad)”, actualización de una nota publicada en el Patch Day de noviembre de 2022.
- Las siguientes en criticidad (con CVSS 9,4) son 2 HotNews, una relacionada con “Improper access control in SAP NetWeaver AS for Java” y la otra relacionada con “Improper access control in SAP NetWeaver Process Integration (Messaging System), esta última nota se trata de una actualización de una nota lanzada en el Patch Day Diciembre de 2022.
- La siguiente nota en criticidad (con CVSS 9,0) está relacionada con “Capture-replay vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform”.
- Este mes el tipo más predominante es “Cross-Site Scripting (XSS)” ( 3/12 en patch day).
En la gráfica (post enero 2023 de SAP) podemos ver la clasificación de las notas de enero además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- SQL Injection vulnerability in SAP Business Planning and Consolidation MS (3275391) AP Business Planning and Consolidation MS allows an unauthorized attacker to execute crafted database queries. An exploitation of this issue could allow an attacker to access, modify, and/or delete data from the backend database.. CVSS v3 Base Score: 9,9 / 10 [CVE-2023-0016].
- Code Injection vulnerability in SAP BusinessObjects Business Intelligence platform (3262810): SAP BusinessObjects Business Intelligence Analysis edition for OLAP allows an authenticated attacker to inject malicious code that can be executed by the application over the network. On successful exploitation, attacker can perform operations that may completely compromise the application causing high impact on confidentiality, integrity and availability of the application. . CVSS v3 Base Score: 9,9 / 10 [CVE-2023-0022].
- Update – Improper access control in SAP NetWeaver Process Integration (User Defined Search) (3273480): An unauthenticated attacker over the network can attach to an open interface exposed through JNDI by the User Defined Search (UDS) of SAP NetWeaver Process Integration (PI) and make use of an open naming and directory api to access services which can be used to perform unauthorized operations affecting users and data across the entire system. This allows the attacker to have full read access for user data, to make limited modifications to user data and to degrade performance of the system, leading to high impact on confidentiality and limited impact on availability and integrity of the application. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41272].
- Update – Insecure Deserialization of Untrusted Data in SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad) (3243924): There is no verification in the de-serialization process, in some workflow of SAP BusinessObjects BI Platform (Central Management Console and BI LaunchPad), an authenticated attacker with low privileges can intercept a serialized object in the parameters and substitute with malicious serialized one, which leads to deserialization of untrusted data vulnerability. Note update includes a workaround. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41203].
- Update – Improper access control in SAP NetWeaver Process Integration (Messaging System) (3267780): An unauthenticated user can attach to an open interface exposed through JNDI by the Messaging System of SAP NetWeaver Process Integration (PI). This user can make use of an open naming and directory api to access services which could perform unauthorized operations. The vulnerability affects local users and data, leading to considerable impact on confidentiality as well availability and also limited impact on integrity of the application. These operations can be used to read any information ,modify sensitive information ,Denial of Service attacks (DoS) and SQL injection. This note has been reissued with the correction of SP017 and SP018 of version 7.50. CVSS v3 Base Score: 9,4 / 10 [CVE-2022-41271].
- Improper access control in SAP NetWeaver AS for Java (3268093): An unauthenticated attacker can attach to an open interface and make use of an open naming and directory API to access services which can be used to perform unauthorized operations affecting users and data on the current system. This could allow the attacker to have full read access for user data, to make modifications to user data and to make particular services within the system unavailable. CVSS v3 Base Score: 9,4 / 10 [CVE-2023-0017].
- Capture-replay vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform (3089413): The system identification hash is not unique, SAP NetWeaver ABAP Server and ABAP Platform creates information about system identity in an ambiguous format. This may be exploited by malicious users to obtain illegitimate access to the system, with this note the system ID will become unique. CVSS v3 Base Score: 9,0 / 10 [CVE-2023-0014].
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (enero):
SAP Patch Day: January 2023 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP BPC MS 10.0, Versions -800, 810
- SAP BusinessObjects Business Intelligence platform (Analysis edition for OLAP), Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform (Central Management Console and BI Launchpad), Versions -4.2, 4.3
- SAP NetWeaver ABAP Server and ABAP Platform, Versions-SAP_BASIS 700, 701, 702,710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, KERNEL 7.22, 7.53, 7.77, 7.81, 7.85, 7.89, KRNL64UC 7.22, 7.22EXT, 7.53, KRNL64NUC 7.22, 7.22EXT
- SAP NetWeaver AS for Java, Version –7.50
- SAP NetWeaver Process Integration, Version –7.50