Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Marzo 2023
Resumen y highlights del Mes
El número total de notas/parches ha sido de 21, 5 menos que el mes pasado. El número de Hot News aumenta, pasando de 1 a 6 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta disminuye pasando de 5 a 4. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 7 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 21 notas para todo el mes (las 19 del patch Tuesday, las 19 nuevas, son 7 notas menos que el pasado mes).
Revisaremos en detalle las 4 notas altas, las 4 son nuevas y las 6 HotNews, 1 actualización y 5 nuevas:
- Las notas más críticas del mes (con CVSS 9,9) son 3 HotNews, una relacionada con “Code Injection vulnerability in SAP Business Objects Business Intelligence Platform” y otra relacionada con “Improper Access Control in SAP NetWeaver AS for Java”, la tercera, se trata de una actualización de una nota lanzada en diciembre de 2022 relacionada con “Improper access control in SAP NetWeaver AS Java (User Defined Search)”.
- Las siguientes en criticidad (con CVSS 9,6 ) son 2 HotNews, una relacionada con “Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform” y la otra relacionada con “Directory traversal vulnerability in SAP ERP and S4HANA”.
- La siguiente nota en criticidad (con CVSS 9,0) se trata de otra HotNews, relacionada con “OS command execution vulnerability in SAP Business Objects Business Intelligence Platform”
- La siguiente se trata de una nota alta (con CVSS 8,8) relacionada con “Arbitrary Code Execution in SAP Solution Manager and ABAP managed Systems”
- La siguiente nota en criticidad (con CVSS 8,7) se trata de una nota alta relacionada con “Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform”
- Las siguientes notas en criticidad (con CVSS 7,4 y 7,2) son 2 notas altas, la primera se trata de una nota relacionada con “Multiple vulnerabilities in SAP NetWeaver AS for ABAP and ABAP Platform”, la otra está relacionada con “Memory Corruption vulnerability in SAPOSCOL”
- Este mes el tipo más predominante es “Improper Access Control in SAP NetWeaver” (4/19 en patch day).
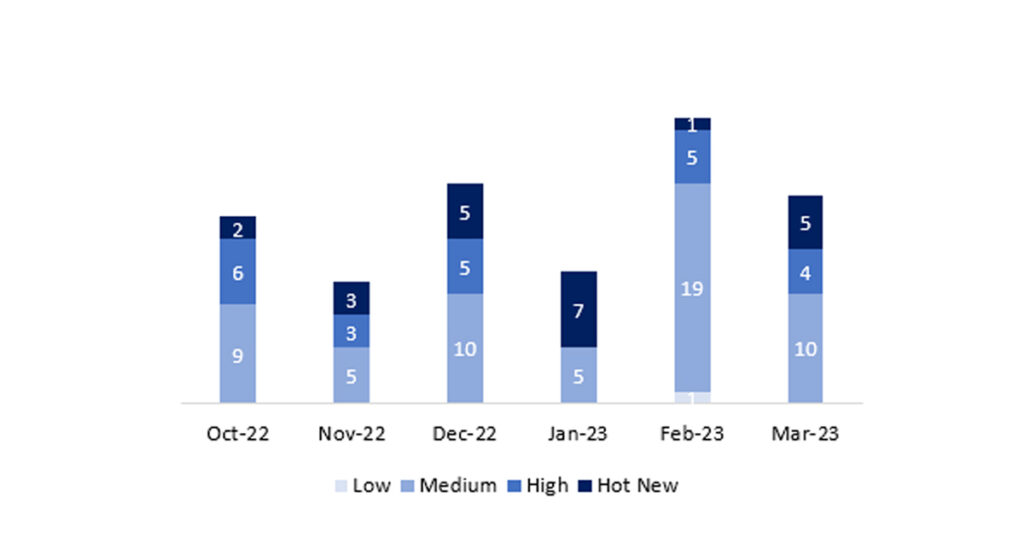
En la gráfica (post marzo 2023 de SAP) podemos ver la clasificación de las notas de marzo además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Code Injection vulnerability in SAP Business Objects Business Intelligence Platform (CMC) (3245526): In some scenarios, SAP Business Objects Business Intelligence Platform (CMC) Program Object execution can lead to code injection vulnerability which could allow an attacker to gain access to resources that are allowed by extra privileges. Successful attack could highly impact the confidentiality, Integrity, and Availability of the system. In addition to the solution provided by the patch upload the note contains a workaround. CVSS v3 Base Score: 9,9 / 10 [CVE-2023-25616].
- Improper Access Control in SAP NetWeaver AS for Java (3285757): Due to missing authentication check, SAP NetWeaver Application Server for Java allows an unauthenticated attacker to attach to an open interface and make use of an open naming and directory API to access services which can be used to perform unauthorized operations affecting users and services across systems. On a successful exploitation, the attacker can read and modify some sensitive information but can also be used to lock up any element or operation of the system making it unresponsive or unavailable. The solution provided by SAP interrupts public access to the LockingService by introducing the required authentication and authorization protection. CVSS v3 Base Score: 9,9 / 10 [CVE-2023-23857].
- Update – Improper access control in SAP NetWeaver Process Integration (User Defined Search) (3273480): An unauthenticated attacker over the network can attach to an open interface exposed through JNDI by the User Defined Search (UDS) of SAP NetWeaver Process Integration (PI) and make use of an open naming and directory api to access services which can be used to perform unauthorized operations affecting users and data across the entire system. This allows the attacker to have full read access for user data, to make limited modifications to user data and to degrade performance of the system, leading to high impact on confidentiality and limited impact on availability and integrity of the application. This note has been re-released with updated ‘Causes – Side Effects’ section. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41272].
- Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform (3294595): SAP NetWeaver Application Server for ABAP and ABAP Platform allows an attacker with non-administrative authorizations to exploit a directory traversal flaw in an available service to overwrite the system files. In this attack, no data can be read but potentially critical OS files can be overwritten making the system unavailable. In addition to the solution provided by the patch upload the note contains a workaround. CVSS v3 Base Score: 9,6 / 10 [CVE-2023-27269].
- Directory traversal vulnerability in SAP ERP and S4HANA (SAPRSBRO Program) (3302162): An attacker with non-administrative authorizations can exploit a directory traversal flaw in program SAPRSBRO to over-write system files. In this attack, no data can be read but potentially critical OS files can be over-written making the system unavailable. CVSS v3 Base Score: 9,6 / 10 [CVE-2023-27269].
- OS command execution vulnerability in SAP Business Objects Business Intelligence Platform (Adaptive Job Server)(3283438): Due to incorrectly escaped parameters in Unix, SAP Business Objects Business Intelligence Platform (Adaptive Job Server) allows an authenticated attacker to execute arbitrary commands over the network. On successful exploitation, the attacker can completely compromise the application, causing high impact of confidentiality, integrity and availability of the application. In addition to the solution provided by the patch upload the note contains a workaround. CVSS v3 Base Score: 9,0 / 10 [CVE-2023-25617].
- Arbitrary Code Execution in SAP Solution Manager and ABAP managed systems (ST-PI) (3296476): An attacker authenticated as a user with a non-administrative role and a common remote execution authorization can use a vulnerable interface to execute an application function to perform actions which they would not normally be permitted to perform. Depending on the function executed, the attacker can read or modify any user or application data and can make the application unavailable, hence affecting the ABAP managed systems and SAP Solution Manager system. This vulnerability affects systems with Addon ST-PI due to an enhancement concept of AP Solution Manager, Custom Code Lifecycle Management. CVSS v3 Base Score: 8,8 / 10 [CVE-2023-27893].
- Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform (3294954): SAP NetWeaver AS for ABAP and ABAP Platform allows an attacker to exploit insufficient validation of path information provided by users, thus exploiting a directory traversal flaw in an available service to delete system files. In this attack, no data can be read but potentially critical OS files can be deleted making the system unavailable, causing significant impact on both availability and integrity. The problem arises because the input parameter dir_name in function EPS_SEEK_OUTPUT_FILE was not properly checked in case no content was fulfilled. CVSS v3 Base Score: 8,7 / 10 [CVE-2023-27501]].
- Multiple vulnerabilities in SAP NetWeaver AS for ABAP and ABAP Platform (3296346): In SAP NetWeaver AS for ABAP and ABAP Platform, due to improper input controls an attacker authenticated as a non-administrative user can craft a request which will trigger the application server to send a request to an arbitrary url which can reveal, modify or make non-sensitive information unavailable, leading to low impact on Confidentiality, Integrity and Availability. CVSS v3 Base Score: 7,4 / 10 [CVE-2023-26459].
- Memory Corruption vulnerability in SAPOSCOL (3275727): SAPOSCOL allows an unauthenticated attacker with network access to a server port assigned to the SAP Start Service to submit a crafted request which results in a memory corruption error. This error can be used to reveal but not modify any technical information about the server. It can also make a particular service temporarily unavailable. By this correction the length of input parameter values is checked. CVSS v3 Base Score: 7,0 / 10 [CVE-2023-27498].
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (marzo):
SAP Patch Day: March 2023 | Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Objects (Adaptive Job Server), Versions –420, 430
- SAP Business Objects Business Intelligence Platform (CMC),Versions–420, 430
- SAP Host Agent, Versions –7.22
- SAP NetWeaver Application Server for ABAP and ABAP Platform, Versions -700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 791
- SAP NetWeaver AS for ABAP and ABAP Platform (SAPRSBRO Program), Versions –700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757
- SAP NetWeaver AS for ABAP and ABAP Platform, Versions -SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 791
- SAP NetWeaver AS for Java,Version –7.50
- SAP Solution Manager and ABAP managed systems(ST-PI), Versions -2008_1_700, 2008_1_710 and 740