Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Julio 2023
Resumen y highlights del Mes
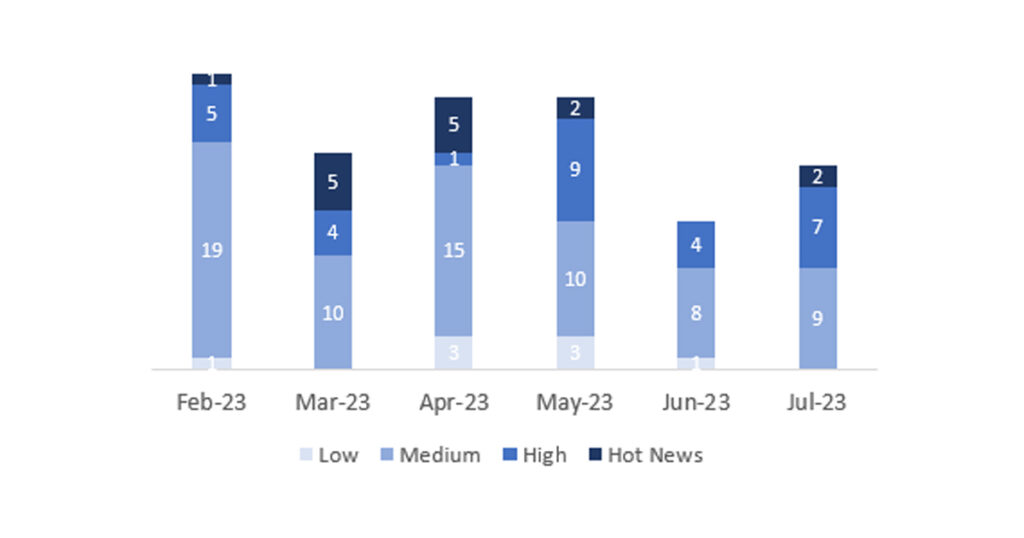
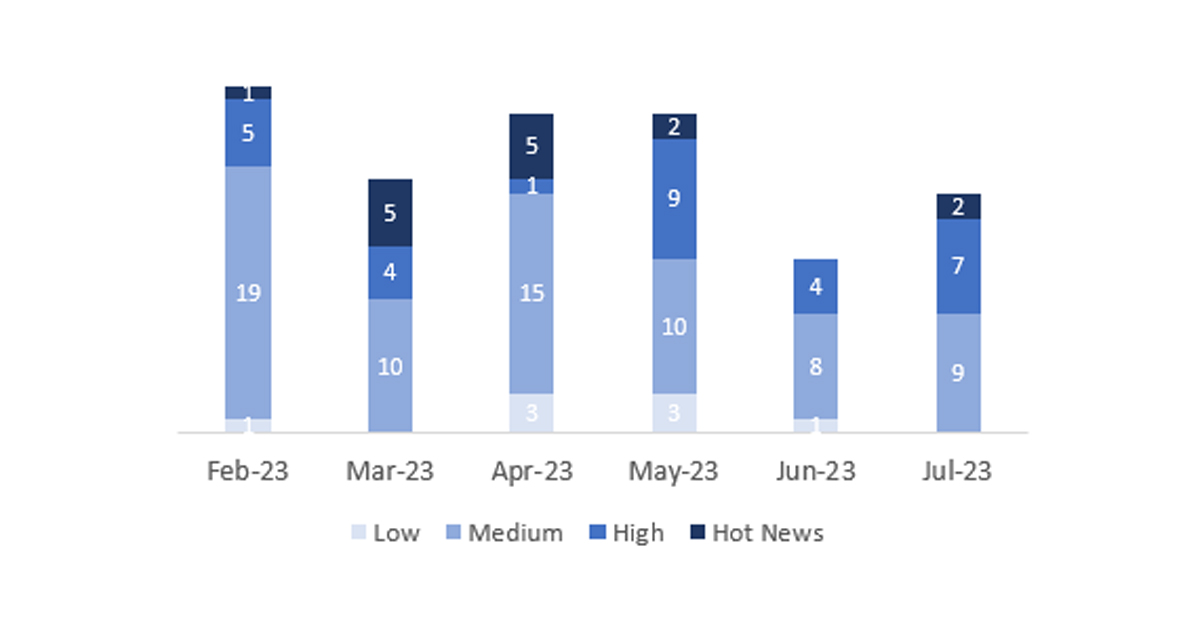
El número total de notas/parches ha sido de 18, 5 más que el mes pasado. El número de Hot News aumenta, pasando de 0 a 2 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta aumenta, pasando 4 a 7. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 9 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 18 notas para todo el mes (las 18 del patch Tuesday, 16 nuevas y 2 actualizaciones, son 5 notas más que el pasado patch Tuesday).
Revisaremos en detalle 9 del total de 9 notas altas y HotNews, 1 de las 2 HotNews es nueva y 6 de 7 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es una actualización de la nota habitual relacionada con “Google Chromium”.
- La siguiente nota en criticidad (con CVSS 9,1) es una HotNew relacionada con” OS command injection vulnerability in SAP ECC and SAP S/4HANA”
- La siguiente nota en criticidad (con CVSS 8,7) está relacionada con “Directory Traversal vulnerability in SAP NetWeaver (BI CONT ADD ON)”
- La siguiente nota en criticidad (con CVSS 8,6), “Request smuggling and request concatenation vulnerability in SAP Web Dispatcher”
- La siguiente nota en criticidad (con CVSS 8,2), se trata de una actualización de una nota publicada el pasado mes de junio, relacionada con “Stored Cross-Site Scripting vulnerability in SAP UI5 (Variant Management)”
- Las siguientes notas en criticidad (con CVSS 7,8 y 7,7), se trata de dos notas altas, una relacionada con “Denial of service (DOS) vulnerability in SAP SQL Anywhere” y la otra con “Memory Corruption vulnerability in SAP Web Dispatcher”
- Las siguientes notas en criticidad (con CVSS 7,2), se trata de dos notas altas, una relacionada con “Unauthenticated blind SSRF in SAP Solution Manager (Diagnostics agent) y la otra con “Header Injection in SAP Solution Manager (Diagnostic Agent)”
- Este mes el tipo más predominante es “Injection vulnerability” (3/18 en patch day).
En la gráfica (post julio 2023 de SAP) podemos ver la clasificación de las notas de julio además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas SAP más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- OS command injection vulnerability in SAP ECC and SAP S/4HANA (IS-OIL) (3350297): Due to programming error in function module and report, IS-OIL component in SAP ECC and SAP S/4HANA allows an authenticated attacker to inject an arbitrary operating system command into an unprotected parameter in a common (default) extension. On successful exploitation, the attacker can read or modify the system data as well as shut down the system. CVSS v3 Base Score: 9,1 / 10 [CVE-2023-36922].
- Directory Traversal vulnerability in SAP NetWeaver (BI CONT ADD ON) (3331376): An attacker with non-administrative authorizations can exploit a directory traversal flaw to over-write system files. Data from confidential files cannot be read but potentially some OS files can be over-written leading to system compromise. CVSS v3 Base Score: 8,7 / 10 [CVE-2023-33989].
- Request smuggling and request concatenation vulnerability in SAP Web Dispatcher (3233899): This note has two attack scenarios:
Scenario 1: CVSS Score: 8,6/10: In SAP NetWeaver AS ABAP and SAP Web Dispatcher an unauthenticated attacker can submit a maliciously crafted request over a network to a front-end server which may, over a number of attempts, result in a back-end server confusing the boundaries of malicious and legitimate messages resulting in execution of malicious payloads which can be used to make it temporarily unavailable, leading to considerable impact on availability.
Scenario 2: CVSS Score: 8,1/10: In SAP NetWeaver AS ABAP and SAP Web Dispatcher an unauthenticated attacker can submit a maliciously crafted request over a network to a front-end server which may, over non-predictive number of attempts, result in a back-end server confusing the boundaries of malicious and legitimate messages resulting in execution of malicious payloads which can be used to read or modify information on the server or make it temporarily unavailable, leading to a limited impact on confidentiality and availability but considerable impact on availability.
CVSS v3 Base Score: 8,6 / 10 [CVE-2023-33987].
- Update – Stored Cross-Site Scripting (Stored XSS) vulnerability in UI5 Variant Management (3324285): UI5 Variant Management does not sufficiently encode user-controlled inputs on reading data from the server, resulting in Stored Cross-Site Scripting (Stored XSS) vulnerability. After successful exploitation, an attacker with user level access can cause high impact on confidentiality, modify some information and also can cause unavailability of the application at user level. This note requires manual activities for implementation. This note has been re-released with updated ‘Solution’ information CVSS v3 Base Score: 8,2 / 10 [CVE-2023-33991].
- Denial of service (DOS) vulnerability in SAP SQL Anywhere (3331029): SAP SQL Anywhere allows an attacker to prevent legitimate users from accessing the service by crashing the service. An attacker with low privileged account and access to the local system can write into the shared memory objects. This can be leveraged by an attacker to perform a Denial of Service. Further, an attacker might be able to modify sensitive data in shared memory objects. CVSS v3 Base Score: 7,8 / 10 [CVE-2023-33990].
- Memory Corruption vulnerability in SAP Web Dispatcher (3340735): The SAP Web Dispatcher has a vulnerability that can be exploited by an unauthenticated attacker to cause memory corruption through logical errors in memory management this may leads to information disclosure or system crashes, which can have low impact on confidentiality and high impact on the integrity and availability of the system. The issue affects the standalone SAP Web Dispatcher, the SAP Web Dispatcher integrated in the ASCS instance, the Internet Communication Manager (ICM) in SAP NetWeaver Application Server ABAP and the Web Dispatcher integrated in SAP HANA. The vulnerability affects only the HTTP/2 protocol. CVSS v3 Base Score: 7,7 / 10 [CVE-2023-35871].
- Unauthenticated blind SSRF in SAP Solution Manager (Diagnostics agent) (3352058): SAP Solution Manager (Diagnostics agent) allows an unauthenticated attacker to blindly execute HTTP requests. On successful exploitation, the attacker can cause a limited impact on confidentiality and availability of the application and other applications the Diagnostics Agent can reach.. CVSS v3 Base Score: 7,2 / 10 [CVE-2023-36925].
- Header Injection in SAP Solution Manager (Diagnostic Agent) (3348145): SAP Solution Manager(Diagnostics agent) allows an attacker to tamper with headers in a client request. This misleads SAP Diagnostics Agent to serve poisoned content to the server. On successful exploitation, the attacker can cause a limited impact on confidentiality and availability of the application. CVSS v3 Base Score: 7,2 / 10 [CVE-2023-36921].
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (julio):
SAP Security Patch Day: July 2023 | Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions -6.5, 7.0, 7.70
- SAP ECC and SAP S/4HANA (IS-OIL), Versions -600, 602, 603, 604, 605, 606, 617, 618, 800, 802, 803, 804, 805, 806, 807
- SAP NetWeaver (BI CONT ADD ON), Versions –707, 737, 747, 757
- SAP Solution Manager (Diagnostic Agent), Versions –7.20
- SAP SQL Anywhere, Version-17.0
- SAP UI5 Variant Management, Versions –SAP_UI 750, SAP_UI 754, SAP_UI 755, SAP_UI 756, SAP_UI 757, UI_700 200
- SAP Web Dispatcher, Versions-WEBDISP 7.53, WEBDISP 7.54, WEBDISP 7.77, WEBDISP 7.85, WEBDISP7.89, WEBDISP 7.91, WEBDISP 7.92, WEBDISP 7.93, KERNEL 7.53, KERNEL 7.54,KERNEL 7.77, KERNEL 7.85, KERNEL 7.89, KERNEL 7.91, KERNEL 7.92, KERNEL 7.93, KRNL64UC 7.53, HDB 2.00, XS_ADVANCED_RUNTIME 1.00, SAP_EXTENDED_APP_SERVICES 1