Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Diciembre 2023
Resumen y highlights del Mes
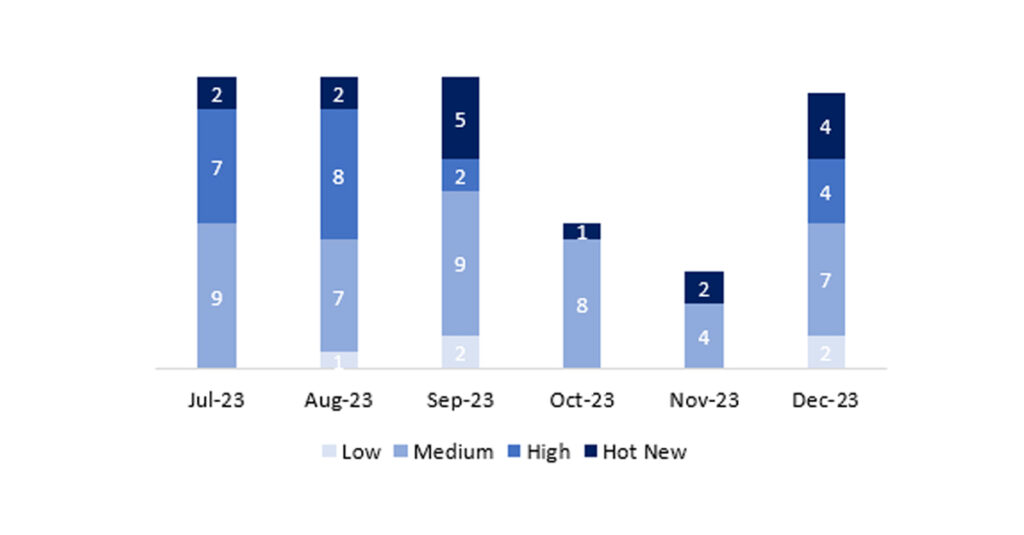
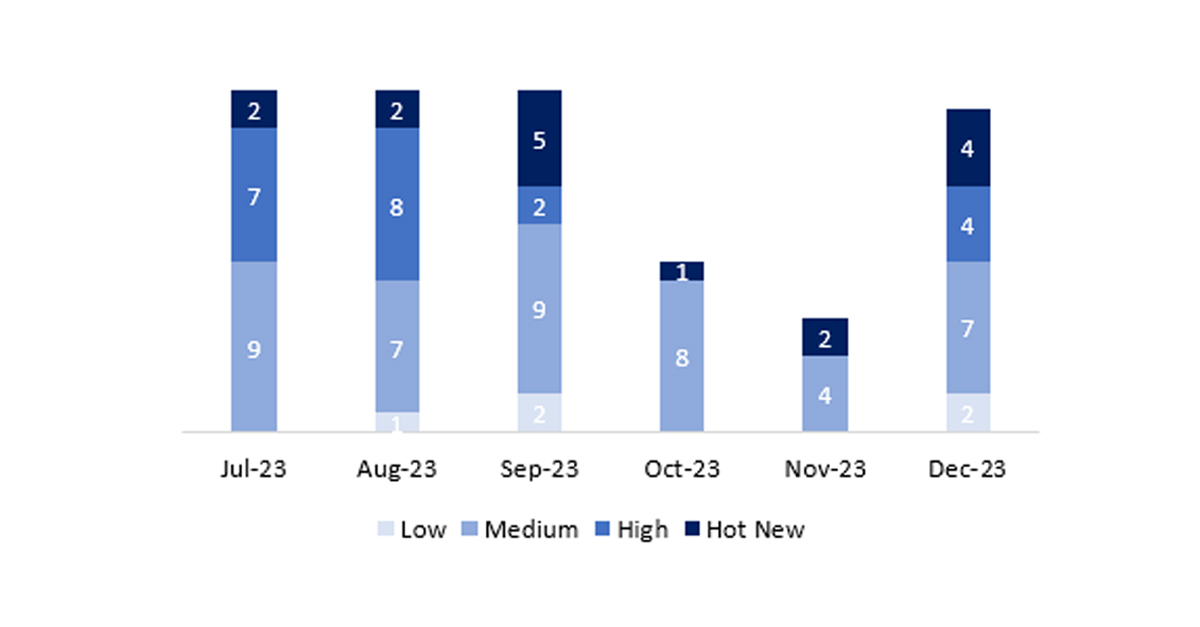
El número total de notas/parches ha sido de 17, 11 más que el mes pasado. El número de Hot News ha sido de 4, 2 más que el mes pasado. Por otro lado, cabe destacar que el número de notas de criticidad alta también aumenta pasando de 0 a 4 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar, pero daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 17 notas para todo el mes (las 17 del patch Tuesday, 15 nuevas y 2 actualizaciones, son 11 notas más que el pasado patch Tuesday).
Revisaremos en detalle un total de 8 notas, las 4 HotNews de este mes, 2 nuevas y 2 actualizaciones y las 4 notas altas, las 4 nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es una actualización de la nota habitual relacionada con “Google Chromium”.
- Las siguientes notas en criticidad (con CVSS 9,1) son 3 HotNews, 2 nuevas y una actualización, una relacionada con “Escalation of Privileges in SAP Business Technology Platform (BTP) Security Services Integration Libraries” y las otras dos con “OS command injection vulnerability in SAP ECC and SAP S/4HANA (IS-OIL)”
- La siguiente en criticidad (con CVSS 8,1), es una nota alta relacionada con “Improper Access Control vulnerability in SAP Commerce Cloud”
- Las siguiente en criticidad (con CVSS 7,5) se trata de una nota alta relacionada con “Cross site scripting vulnerability in SAP BusinessObjects Business Intelligence Platform”
- Las siguientes en criticidad (con CVSS 7,3 y 7,1 respectivamente) están relacionadas con “Information disclosure vulnerability in SAP GUI for WIndows and SAP GUI for Java” y “Missing Authorization Check in SAP EMARSYS SDK ANDROID”
- Este mes el tipo más predominante es “Cross site scripting vulnerability” (4/17 en patch day).
En la gráfica podemos ver la clasificación de las notas de diciembre, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Escalation of Privileges in SAP Business Technology Platform (BTP) Security Services Integration Libraries (3411067): SAP BTP Security Services Integration Libraries and Programming Infrastructures using these libraries listed below allow under certain conditions an escalation of privileges. On successful exploitation, an unauthenticated attacker can obtain arbitrary permissions within the application. CVSS v3 Base Score: 9,1 / 10 (Multiple CVE´s).
- Update – OS command injection vulnerability in SAP ECC and SAP S/4HANA (IS-OIL) (3350297): Due to programming error in function module and report, IS-OIL component in SAP ECC and SAP S/4HANA allows an authenticated attacker to inject an arbitrary operating system command into an unprotected parameter in a common (default) extension. On successful exploitation, the attacker can read or modify the system data as well as shut down the system. The update indicates that the fix provided in this security note is incomplete. For the complete correction, please refer to security note 3399691. CVSS v3 Base Score: 9,1 / 10 [CVE-2023-36922].
- Update 1 to 3350297 – OS command injection vulnerability in SAP ECC and SAP S/4HANA (IS-OIL)( 3399691): Due to programming error in function module and report, IS-OIL component in SAP ECC and SAP S/4HANA allows an authenticated attacker to inject an arbitrary operating system command into an unprotected parameter in a common (default) extension. On successful exploitation, the attacker can read or modify the system data as well as shut down the system. This security note is an update to the security note 3350297. Fix provided in the security note 3350297 was incomplete for the component IS-OIL-DS-HPM. CVSS v3 Base Score: 9,1 / 10 [CVE-2023-36922].
- Improper Access Control vulnerability in SAP Commerce Cloud (3394567): In SAP Commerce Cloud, a locked B2B user can misuse the forgotten password functionality to un-block his user account again and re-gain access if SAP Commerce Cloud – Composable Storefront is used as storefront, due to weak access controls in place. This leads to a considerable impact on confidentiality and integrity. The note contains a workaround as well as manual remediation activities. CVSS v3 Base Score: 8,1 / 10 [CVE-2023-42481]
- Cross site scripting vulnerability in SAP BusinessObjects Business Intelligence Platform (3382353): SAP Business Objects Business Intelligence Platform is vulnerable to stored XSS allowing an attacker to upload agnostic documents in the system which when opened by any other user could lead to high impact on integrity of the application. Note contains a workaround. CVSS v3 Base Score: 7,5 / 10 [CVE-2023-42478]
- Information disclosure vulnerability in SAP GUI for Windows and SAP GUI for Java (3385711): SAP GUI for Windows and SAP GUI for Java allow an unauthenticated attacker to access information which would otherwise be restricted and confidential. In addition, this vulnerability allows the unauthenticated attacker to create Layout configurations of the ABAP List Viewer and with this causing a mild impact on integrity and availability. CVSS v3 Base Score: 7,3 / 10 [CVE-2023-49580]
- Missing Authorization Check in SAP EMARSYS SDK ANDROID (3406244): Vulnerability in authorization checks in the Emarsys SDK for Android, allowing an attacker to navigate to arbitrary urls including deep links to apps on the device. Depending on the application being called, there can be a serious impact on confidentiality and integrity. CVSS v3 Base Score: 7,1 / 10 [CVE-2023-6542]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (diciembre):
SAP Security Patch Day for December 2023| Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions -6.5, 7.0, 7.70
- Library-@sap/xssec, Versions –< 3.6.0
- Library-cloud-security-services-integration-library, Versions –< 2.17.0& from 3.0.0 before3.3.0
- Library-sap-xssec, Versions –< 4.1.0
- Library-github.com/sap/cloud-security-client-go, Versions -< 0.17.0
- SAP ECC and SAP S/4HANA (IS-OIL), Versions -600, 602, 603, 604, 605, 606, 617, 618, 800, 802, 803, 804, 805, 806, 807
- SAP Commerce Cloud, Version –8.1
- Business Objects BI Platform, Versions–420, 430
- SAP GUI for Windows and SAP GUI for Java, Versions–SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP EMARSYS SDK ANDROID, Version –3.6.2