Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Diciembre 2022
Resumen y highlights del Mes
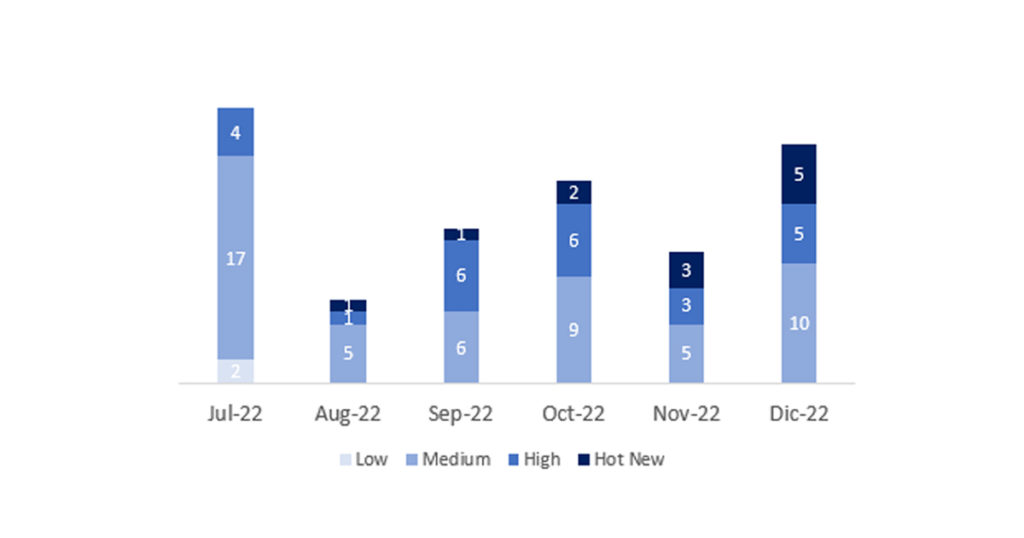
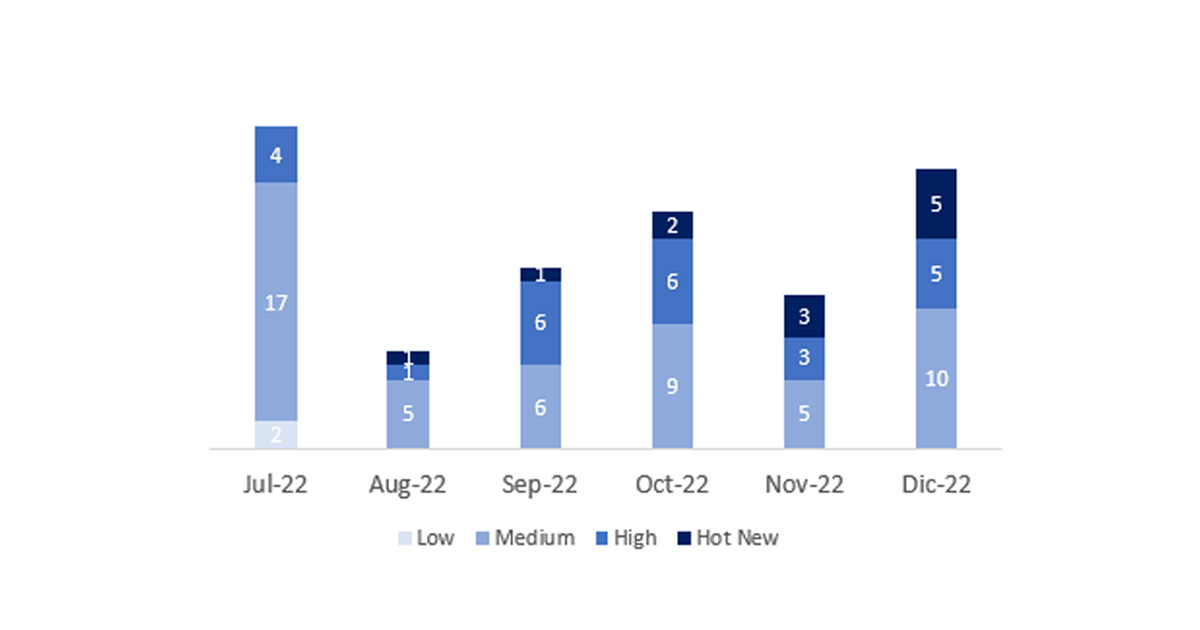
El número total de notas/parches ha sido de 20, 6 más que el mes pasado. El número de Hot News aumenta, pasando de 4 a 5 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta también aumenta este mes pasando de 3 a 5. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 10 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 20 notas para todo el mes (las 19 del patch Tuesday, 13 nuevas y 6 actualizaciones, son 8 notas más que el pasado mes).
Revisaremos en detalle 10 del total de 10 notas altas y HotNews, 4 de las 5 HotNews son nuevas y 3 de 5 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es la habitual nota relacionada con “Google Chromium”.
- La siguientes en criticidad (CVSS 9,9) son 2 HotNews, una relacionada con “Server-Side Request Forgery vulnerability in SAP BusinessObjects Business Intelligence Platform” y la otra con “Improper access control in SAP NetWeaver Process Integration (User Defined Search)”
- La siguiente en criticidad (CVSS 9,8) otra HotNews, referida a “Remote Code Execution vulnerability associated with Apache Commons Text in SAP Commerce”
- La siguiente se trata de otra HotNews (CVSS 9,4), es una actualización de la nota relacionada con “Improper access control in SAP NetWeaver Process Integration (Messaging System)”
- La siguientes en criticidad (CVSS 8,8, 8,5, 8,2, 8,0 y 7,5) son las cinco notas altas, una de “Code Injection vulnerability in SAP BASIS, la siguiente estaría relacionada con “Privilege escalation vulnerability in SAP Business Planning and Consolidation” , la siguiente es una actualización de una nota lanzada en octubre referida a “Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Program Objects)” la cuarta nota estaría relacionada con “Cross-Site Scripting (XSS) vulnerability in SAP Commerce”, la última nota se trata de una actualización de una nota lanzada en el Patch Day de noviembre
- Este mes el tipo más predominante es “Cross-Site Scripting (XSS)” (2/20 y 2/19 en patch day).
En la gráfica (post diciembre 2022 de SAP) podemos ver la clasificación de las notas de diciembre además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Server-Side Request Forgery vulnerability in SAP BusinessObjects Business Intelligence Platform (3239475): SAP Business Objects platform allows an attacker with normal BI user privileges to upload/replace any file on Business Objects server at operating system level, enabling the attacker to take full control of the system causing high impact on confidentiality, integrity and availability of the application. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41267].
- Improper access control in SAP NetWeaver Process Integration (User Defined Search) (3273480): An unauthenticated attacker over the network can attach to an open interface exposed through JNDI by the User Defined Search (UDS) of SAP NetWeaver Process Integration (PI) and make use of an open naming and directory api to access services which can be used to perform unauthorized operations affecting users and data across the entire system. This allows the attacker to have full read access for user data, to make limited modifications to user data and to degrade performance of the system, leading to high impact on confidentiality and limited impact on availability and integrity of the application. CVSS v3 Base Score: 9,9 / 10 [CVE-2022-41272].
- Remote Code Execution vulnerability associated with Apache Commons Text in SAP Commerce (3271523): Apache Commons Text performs variable interpolation. Applications using the interpolation defaults in the affected versions may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used. On successful exploitation the attacker can completely compromise the confidentiality, integrity, and availability of the application. CVSS v3 Base Score: 9,8 / 10 [Related CVE-2022-42889].
- Improper access control in SAP NetWeaver Process Integration (Messaging System) (3267780): An unauthenticated user can attach to an open interface exposed through JNDI by the Messaging System of SAP NetWeaver Process Integration (PI). This user can make use of an open naming and directory api to access services which could perform unauthorized operations. The vulnerability affects local users and data, leading to considerable impact on confidentiality as well availability and also limited impact on integrity of the application. These operations can be used to read any information ,modify sensitive information ,Denial of Service attacks (DoS) and SQL injection. CVSS v3 Base Score: 9,4 / 10 [CVE-2022-41271].
- Code Injection vulnerability in SAP BASIS (Messaging System) (3268172): Due to unrestricted scope of the RFC function module, SAP BASIS allows an authenticated non-administrator attacker to access a system class and execute any of its public methods with parameters provided by the attacker. On successful exploitation the attacker can have full control of the system to which the class belongs, causing high impact on integrity of the application. CVSS v3 Base Score: 8,8 / 10 [CVE-2022-41264].
- Privilege escalation vulnerability in SAP Business Planning and Consolidation (3271091): In some SAP standard roles in SAP Business Planning and Consolidation, a transaction code reserved for customer is used. By implementing such transaction code, a malicious user may execute unauthorized transaction functionality. Under specific circumstances, a successful attack could enable an adversary to escalate their privileges to be able to read, change or delete system data. The note contains manual activities CVSS v3 Base Score: 8,5 / 10 [CVE-2022-41268].
- Update – Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Program Objects) (3229132): Under certain conditions an attacker can get access to OS credentials. Attacker must be authenticated, administrator sees credentials in clear text, normal user sees credentials in encrypted form. Getting access to OS credentials enables the attacker to modify system data and make the system unavailable leading to high impact on confidentiality and low impact on integrity and availability of the application. CVSS v3 Base Score: 8,2 / 10 [CVE-2022-39013].
- Cross-Site Scripting (XSS) vulnerability in SAP Commerce (3248255): Due to lack of proper input validation, SAP Commerce Webservices 2.0 Swagger UI allows malicious inputs from untrusted sources, which can be leveraged by an attacker to execute a DOM Cross-Site Scripting (XSS) attack. As a result, an attacker may be able to steal user tokens, and achieve full account takeover including access to administrative tools in SAP Commerce. The vulnerability comes from the open source library springfox-swagger-ui, which contains a repackaged version of the open source library swagger-ui. This version of swagger-ui packaged allows the DOM-based XSS vulnerability. CVSS v3 Base Score: 8,0 / 10 [CVE-2022-41266].
- Update – Multiple Vulnerabilities in SQlite bundled with SAPUI5 (3249990): An issue was found in fts5UnicodeTokenize() in ext/fts5/fts5_tokenize.c in Sqlite. A unicode61 tokenizer configured to treat unicode “control-characters” (class Cc), was treating embedded nul characters as tokens. SAPUI5 framework is using SQLite < 3.34.0 which was treating null characters as tokens, this could be exploited by an user over the network having low privileges leading to considerable impact on confidentiality, integrity and availability of applications using SAPUI5. . CVSS v3 Base Score: 7,5 / 10 [CVE-2022-35737].
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (diciembre):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
SAP Security Patch Day December 2022 | Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions -6.5, 7.0, 7.70
- SAP Business Planning and Consolidation,Versions–SAP_BW 750, 751, 752, 753, 754, 755, 756, 757, DWCORE 200, 300, CPMBPC 810
- SAP BusinessObjects Business Intelligence Platform (Program Objects),Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform,Versions -420, 430
- SAP Commerce Webservices 2.0 (Swagger UI), Versions-1905, 2005, 2105, 2011, 2205
- SAP Commerce, Versions-1905, 2005, 2105, 2011, 2205
- SAP NetWeaver Process Integration, Version –7.50
- SAPBASIS, Versions –731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 789, 790, 791
- SAPUI5 CLIENT RUNTIME, Versions –600, 700, 800, 900, 1000
- SAPUI5, Versions –754, 755, 756, 757