Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas agosto 2025
Resumen y highlights del Mes
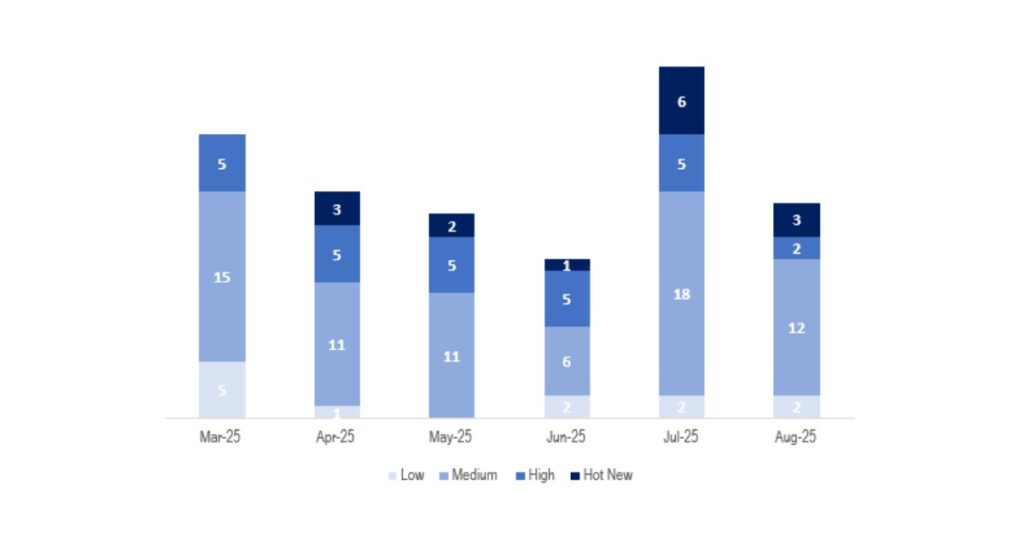
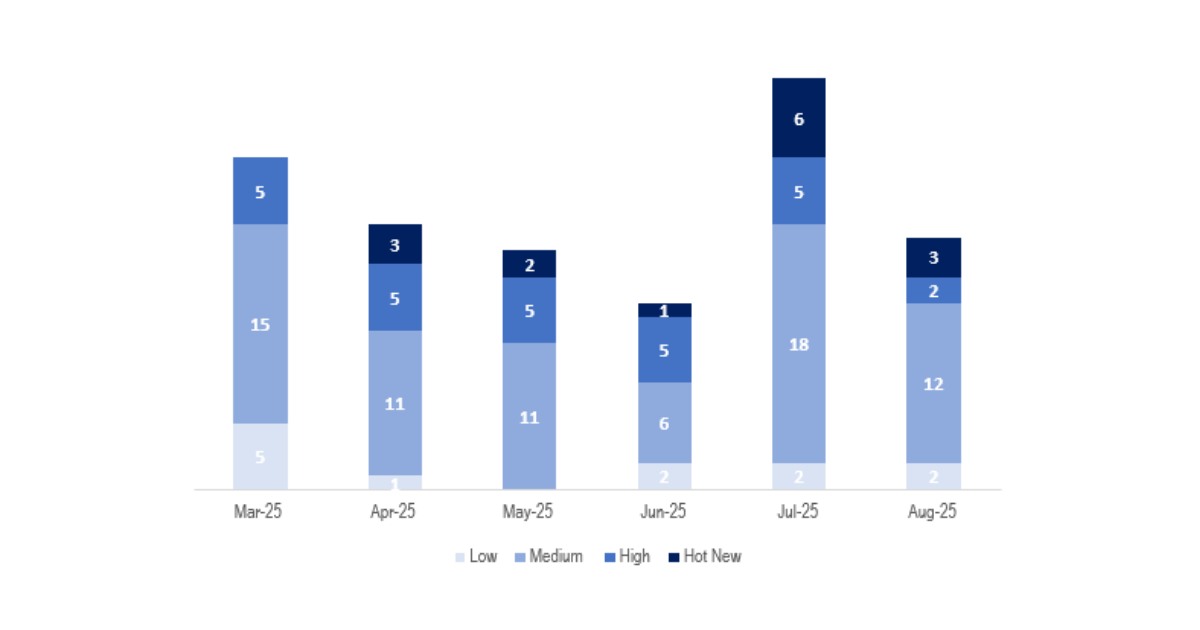
Este mes el número total ha sido de 19 notas, 12 menos que en el mes anterior. Este mes tuvimos 3 Hot News, 3 menos que en el periodo anterior. En cuanto a notas de criticidad alta, hay 2, que son 3 menos que en los 4 meses anteriores en los que se repitieron las 5 notas de este nivel. Las notas medias y bajas no serán revisadas, por lo que daremos detalle de un total de 5 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 19 notas para todo el mes (15 nuevas y 4 actualizaciones de notas publicadas en meses anteriores).
Revisaremos en detalle un total de 5 notas, todas de criticidad alta y Hot News:
-
Las notas más altas en criticidad del mes (CVSS 9,9) son las 3 Hot News, las cuales tienen el mismo índice. Dos de ellas son notas nuevas relacionadas con “Code Injection Vulnerability in SAP Landscape Transformation (Analysis Platform)” y “Code Injection vulnerability in SAP S/4HANA (Private Cloud or On-Premise)”, la otra nota se trata de una actualización correspondiente a una nota lanzada en abril de este año, relacionada con “Code Injection Vulnerability in SAP S/4HANA (Private Cloud or On-Premise)”.
-
La siguiente en criticidad (CVSS 8,8) se trata de la primera nota alta relacionada con “Broken Authorization in SAP Business One (SLD)”.
-
Por último, la última nota que vamos a analizar y la más baja en criticidad (CVSS 8,1) se trata de una nota del relacionada con “Multiple vulnerabilities in SAP NetWeaver Application Server ABAP (BIC Document)”.
-
Este mes el tipo más predominante es “Missing Authorization Check ” (4/19 en el patch day) seguido de “Code Injection vulnerability” (3/19 en el patch day).
En la gráfica podemos ver la clasificación de las notas de agosto, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
Code Injection vulnerability in SAP S/4HANA (Private Cloud or On-Premise) (3627998): In SAP S/4HANA, a vulnerability in a function module exposed via RFC can be exploited by a privileged user to inject arbitrary ABAP code, bypassing authorization checks and acting as a backdoor, risking full system compromise and impacting confidentiality, integrity, and availability. SAP has released a fix that removes this code injection risk by preventing arbitrary script or command execution, and the referenced Correction Instructions or Support Packages must be applied immediately, as no temporary workaround is available. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42957]
-
Code Injection Vulnerability in SAP Landscape Transformation (Analysis Platform) (3633838): In SAP Landscape Transformation (SLT), a vulnerability in a function module exposed via RFC can be exploited by a privileged user to inject arbitrary ABAP code, bypassing authorization checks and acting as a backdoor, potentially leading to full system compromise and impacting confidentiality, integrity, and availability. SAP has issued a fix that removes the code injection risk by blocking arbitrary script or command execution, and the referenced Correction Instructions or Support Packages must be applied immediately, as no temporary workaround exists. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42950]]
-
Code Injection Vulnerability in SAP S/4HANA (Private Cloud or On-Premise) (3581961): In SAP S/4HANA, a vulnerability in a function module exposed via RFC can be exploited by a privileged user to inject arbitrary ABAP code, bypassing authorization checks and acting as a backdoor, risking full system compromise and impacting confidentiality, integrity, and availability. In the current version (V6, 12th August 2025), the note has been re-released with updated Support Packages & Patches information, which must be applied promptly to address the issue. The fix removes the risk of code injection by blocking arbitrary script or command execution. There is no workaround, so implementing the updated instructions is critical to securing the system. CVSS v3 Base Score 9,9/ 10 [CVE-2025-27429]
-
Broken Authorization in SAP Business One (SLD) (3625403): In SAP Business One (SLD), a broken authorization flaw allows an authenticated attacker to gain database administrator privileges by invoking a specific API, posing a high risk to confidentiality, integrity, and availability. The vulnerability occurs because the SLD backend service failed to enforce proper authorization for users logged in via the native client, exposing sensitive credentials. SAP has fixed the issue by revoking this API permission for normal users, ensuring only landscape administrators (e.g., B1SiteUser) can invoke it, adjusting database account usage in the client, and introducing an admin login prompt for privileged landscape management tasks. The referenced Support Packages and Patches must be applied immediately, as no workaround exists. CVSS v3 Base Score 8,8/ 10 [CVE-2025-42951]
-
Multiple vulnerabilities in SAP NetWeaver Application Server ABAP (BIC Document) (3611184): In SAP NetWeaver Application Server ABAP (BIC Document), multiple vulnerabilities were found due to missing input validation: Memory Corruption (CVE-2025-42976) allows an authenticated attacker to send crafted requests that can crash the target component or perform out-of-bounds reads, exposing sensitive in-memory data; Reflected Cross-Site Scripting (XSS) (CVE-2025-42975) lets an unauthenticated attacker trick a victim into executing malicious scripts in their browser via crafted URLs, potentially accessing or modifying web client data. SAP resolved the issue by improving input parameter validation. Customers must implement the Correction Instructions or Support Packages from the note. As a temporary workaround, the SICF service “BIC” can be deactivated, though SAP strongly recommends applying the permanent fix. CVSS v3 Base Score 8,1/ 10 [CVE-2025-42976]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (Agosto):
SAP Security Patch Day – August 2025
SAP Patch Day: August 2025 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
-
SAP S/4HANA (Private Cloud or On-Premise)
Versiones: S4CORE 102, 103, 104, 105, 106, 107, 108 (incluye Bank Communication Management y Supplier invoice módulos en algunas notas) -
SAP Landscape Transformation (Analysis Platform)
Versiones: DMIS 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2011_1_752, 2020 -
SAP Business One (SLD)
Versiones: B1_ON_HANA 10.0, SAP-M-BO 10.0 -
SAP NetWeaver Application Server ABAP (BIC Document)
Versiones: S4COREOP 104, 105, 106, 107, 108; SEM-BW 600, 602, 603, 604, 605, 634, 736, 746, 747, 748 -
SAP S/4HANA (Bank Communication Management)
Versiones: SAP_APPL 606, SAP_FIN 617, 618, 720, 730; S4CORE 102, 103, 104, 105, 106, 107, 108 -
SAP NetWeaver Application Server ABAP
Versiones: KRNL64UC 7.53; KERNEL 7.53, 7.54, 7.77, 7.89, 7.93; SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 816, 914, 916 -
SAP NetWeaver ABAP Platform
Versiones: S4CRM 100, 200, 204, 205, 206; S4CEXT 107, 108, 109; BBPCRM 713, 714; SAP_BASIS 758, 816, 916 -
SAP NetWeaver Enterprise Portal (OBN component)
Versiones: EP-RUNTIME 7.50 -
ABAP Platform
Versiones: SAP_BASIS 758, 816, 916 -
SAP GUI for Windows
Versiones: BC-FES-GUI 8.00 -
SAP S/4HANA (Supplier invoice)
Versiones: S4CORE 102, 103, 104, 105, 106, 107, 108, 109 -
SAP NetWeaver
Versiones: SAP_ABA 700, 701, 702, 731, 740, 750, 751, 752, 75C, 75D, 75E, 75F, 75G, 75H, 75I -
SAP NetWeaver AS for ABAP and ABAP Platform (Internet Communication Manager)
Versiones: KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53; KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93; 9.14, 9.15, 9.16 -
SAP Cloud Connector
Versiones: SAP_CLOUD_CONNECTOR 2.0 -
SAP Fiori (Launchpad)
Versiones: SAP_UI 754