Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas septiembre 2025
Resumen y highlights del Mes
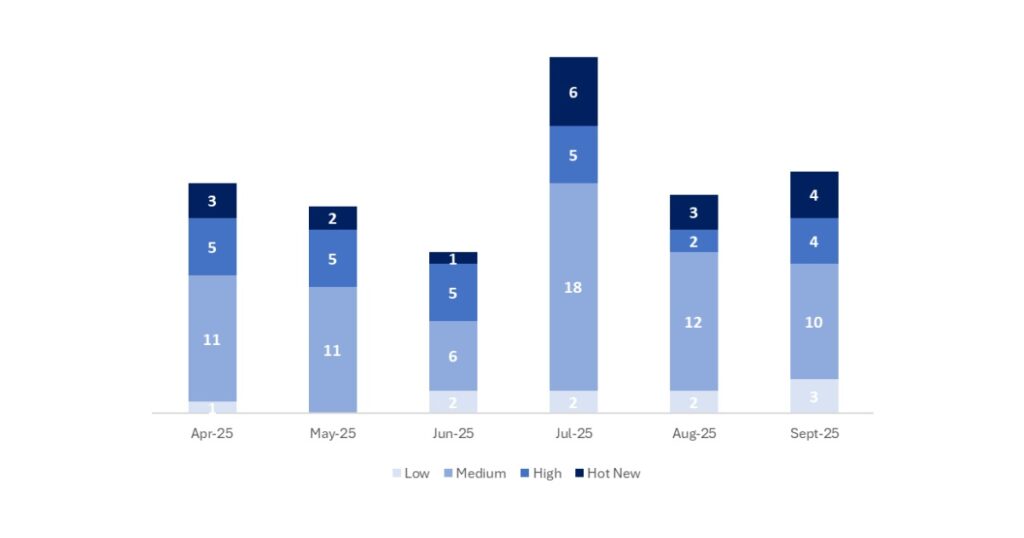
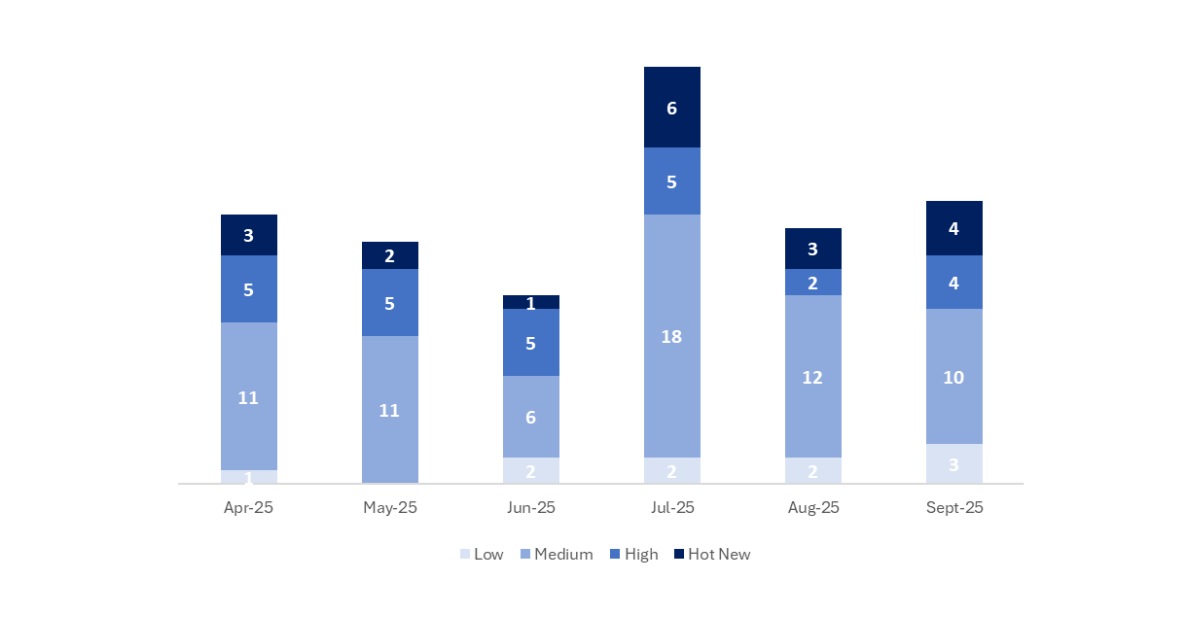
Este mes el número total ha sido de 21 notas, 2 más que en el mes anterior. Este mes tuvimos 4 Hot News, 1 más que en el periodo anterior. En cuanto a notas de criticidad alta, hay 4, que son 2 más que en el mes anterior. Las notas medias y bajas no serán revisadas, por lo que daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 21 notas para todo el mes (17 nuevas y 4 actualizaciones de notas publicadas en meses anteriores).
Revisaremos en detalle un total de 5 notas, todas de criticidad alta y Hot News:
-
La nota más alta en criticidad del mes (CVSS 10) es la Hot News con la máxima puntuación de criticidad. Esta nota nueva, está relacionada con “Insecure Deserialization vulnerability in SAP Netweaver (RMI-P4)”
-
La siguiente en criticidad (CVSS 9,9) se trata de la siguiente Hot News relacionada con “Insecure File Operations vulnerability in SAP NetWeaver AS Java (Deploy Web Service)”.
-
La siguiente en criticidad (CVSS 9,6) es la tercera Hot News del mes, y se tratata de una actualización de una publicada en Marzo del año 2023. Está relacionada con “Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform“
-
La siguiente nota en criticidad (CVSS 9,1) es la última Hot News del periodo, y está relacionada con “Missing Authentication check in SAP NetWeaver“
-
La siguiente nota en criticidad (CVSS 8,8) es la primera nota de criticidad alta, y se trata de una nota del relacionada con “Insecure Storage of Sensitive Information in SAP Business One (SLD)”.
-
La siguiente nota en criticidad (CVSS 8,1) se trata de una nota relacionada con “Missing input validation vulnerability in SAP Landscape Transformation Replication Server”
-
La siguiente nota en criticidad (CVSS 8,1) se trata de una nota relacionada con “Missing input validation vulnerability in SAP S/4HANA (Private Cloud or On-Premise)”
-
Por último, la última nota que vamos a analizar, y que su criticidad es (CVSS 7,7) se trata de una actualización de una nota lanzada en abril de este año, y está relacionada con “Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection)”
-
Este mes el tipo más predominante es “Missing Authorization Check ” (8/21 en el patch day).
En la gráfica podemos ver la clasificación de las notas de septiembre, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
Insecure Deserialization vulnerability in SAP Netweaver (RMI-P4) (3634501): In SAP NetWeaver, an unauthenticated attacker could exploit a deserialization vulnerability in the RMI-P4 module by sending malicious payloads to an open port. This insecure deserialization of untrusted Java objects could allow arbitrary OS command execution, severely impacting confidentiality, integrity, and availability. SAP resolved the issue by updating the affected P4-Lib component to enforce secure deserialization and restrict untrusted object acceptance. Customers must implement the patches specified in the note, ensuring that the JVM version is greater than Java 8 u121, and review dependency guidance to avoid incompatibilities. If patches cannot be applied immediately, administrators can mitigate risk by filtering the P4 port at the ICM level, allowing only trusted hosts and blocking all others. This workaround should only be used temporarily until the official fix is applied, after which it can be rolled back. CVSS v3 Base Score 10/ 10 [CVE-2025-42944]
-
Insecure File Operations vulnerability in SAP NetWeaver AS Java (Deploy Web Service)(3643865): In SAP NetWeaver AS Java, an attacker authenticated as a non-administrative user could exploit a flaw in an available service to upload arbitrary files, which if executed could result in full system compromise, affecting confidentiality, integrity, and availability. SAP resolved this issue by restricting access to the vulnerable web service exclusively to administrative users. A temporary workaround is available and described in KBA 3646072. It should only be used if patches cannot be immediately applied and must be assessed for applicability to the specific SAP landscape. SAP strongly recommends applying the permanent fix as soon as possible. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42922]
-
Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform (update) (3302162): In SAP, a directory traversal vulnerability in program SAPRSBRO allows an attacker with non-administrative authorizations to overwrite system files. While no data can be read, critical OS files may be replaced, leading to system unavailability. In the current version (v11, 9th September 2025), the note was re-released with updated Correction Instruction information. To resolve the issue, customers must implement the referenced Support Package or apply the attached coding corrections, which disable execution of the vulnerable program. For further details, SAP Note 3311360 provides additional guidance. CVSS v3 Base Score 9,6/ 10 [CVE-2023-27500]
-
Missing Authentication check in SAP NetWeaver (3627373): In SAP NetWeaver on IBM i-series, a missing authentication check allows highly privileged unauthorized users to read, modify, or delete sensitive information, as well as access administrative functions, severely impacting confidentiality, integrity, and availability. Systems are affected when multiple SAP system IDs (SIDs) are configured in one logical partition (LPAR). SAP resolved the issue by enforcing proper access restrictions and limiting SAP user profile rights. The fix is delivered via updated kernel patch levels (hotfix
ILE.SARor SP Stack Kernel filesSAPEXE.SARandSAPEXEDB.SAR). Customers should apply the latest available SP Stack Kernel or hotfix as recommended in the note and related kernel guidance. No workaround is available; applying the kernel patch is mandatory. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42958] -
Insecure Storage of Sensitive Information in SAP Business One (SLD) (3642961): In SAP Business One, when a user logs in via the native client, the SLD backend service failed to properly encrypt certain APIs, resulting in exposure of sensitive credentials in the HTTP response body. This flaw could compromise confidentiality, integrity, and availability of the application. SAP fixed the issue by enhancing the SLD service logic to securely encrypt the database password in responses. Customers must implement the referenced Support Packages and Patches to mitigate the risk. There is no workaround. CVSS v3 Base Score 8,8/ 10 [CVE-2025-42933]
-
Missing input validation vulnerability in SAP Landscape Transformation Replication Server (3633002): In SAP, missing input validation allows an attacker with high privilege access to ABAP reports to delete the content of arbitrary database tables if they are not protected by an authorization group. This vulnerability severely impacts database integrity and availability. SAP resolved the issue by removing obsolete and outdated code. Customers must apply the Correction Instructions or Support Packages referenced in the note. CVSS v3 Base Score 8,1/ 10 [CVE-2025-42929]
-
Missing input validation vulnerability in SAP S/4HANA (Private Cloud or On-Premise) (3635475): In SAP, missing input validation in ABAP reports allows an attacker with high privilege access to delete the content of arbitrary database tables that are not protected by an authorization group. This vulnerability affects database integrity and availability, though confidentiality is not impacted. SAP resolved the issue by removing obsolete and outdated code. Customers must apply the Correction Instructions or Support Packages specified in the note. No workaround is available; the official fix must be applied. CVSS v3 Base Score 8,1/ 10 [CVE-2025-42916]
-
Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection) (update) (3581811): In SAP Solution Manager, a directory traversal vulnerability in an RFC-enabled function module allows an authorized attacker to read files from any managed system, potentially exposing critical information and impacting confidentiality, though integrity and availability are unaffected. In the current version (v8, 9th September 2025), the note was re-released with updated Correction Instructions. SAP fixed the issue by enforcing proper path checks in the Service Data Collection function module to prevent arbitrary file reads. Customers must implement the referenced Correction Instructions or Support Packages. No workaround is available; applying the correction is required. CVSS v3 Base Score 7,7/ 10 [CVE-2025-27428]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (Septiembre):
SAP Security Patch Day – September 2025
SAP Patch Day: September 2025 – Onapsis
Recursos afectados
-
RMI-P4: SERVERCORE 7.50
-
Application Server Java (Deploy Web Service): J2EE-APPS 7.50
-
AS for ABAP and ABAP Platform: 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757
-
ABAP Platform / Service Data Collection: ST-PI 2008_1_700, 2008_1_710, 740
-
Application Server Java (IIOP Service): SERVERCORE 7.50
-
Application Server Java: WD-RUNTIME 7.50
-
Service Data Download: SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758, 816
-
B1_ON_HANA 10.0, SAP-M-BO 10.0
-
Replication Server: DMIS 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2011_1_752, 2020
-
S4CORE 102, 103, 104, 105, 106, 107, 108
-
BPC4HANA 200, 300, SAP_BW 750–758, 816, 914, CPMBPC 810
-
My Timesheet / Approve Timesheets Fiori 2.0: GBX01HR5 605
-
ENTERPRISE 430, 2025, 2027
-
SRM_SERVER 700, 701, 702, 713, 714
-
S4CRM 100, 200, 204, 205, 206; S4CEXT 109; BBPCRM 713, 714
-
Manage Payment Blocks: S4CORE 107, 108
-
F4044 Manage Work Center Groups: UIS4HOP1 600, 700, 800, 900
-
Launchpad: SAP_UI 754
-
HY_COM 2205, HY_DHUB 2205, COM_CLOUD 2211, DHUB_CLOUD 2211
-
ADSSAP 7.50