Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas diciembre 2025
Resumen y highlights del Mes
Este mes el número total ha sido de 14 notas, 6 menos que en el mes anterior. Este mes hemos tenido 3 Hot News, las mismas que en el periodo anterior. En cuanto a notas de criticidad alta, hay 5, un aumento considerable con respecto al anterior periodo puesto que solo hubo una. Las notas medias y bajas no serán revisadas, por lo que daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 14 notas para todo el mes (Las 14 son nuevas y no hay actualizaciones de notas publicadas en meses anteriores).
Revisaremos en detalle un total de 8 notas, todas de criticidad alta y Hot News:
-
La nota más alta en criticidad del mes (CVSS 9,9) es una Hot News, y está relacionada con “Code Injection vulnerability in SAP Solution Manager”.
-
La siguiente en criticidad (CVSS 9,6) es otra Hot News, la segunda del mes, y está relacionada con “Multiple vulnerabilities in Apache Tomcat within SAP Commerce Cloud“.
-
La siguiente en criticidad (CVSS 9,1) es la última hot news del mes, y está relacionada con “Deserialization Vulnerability in SAP jConnect – SDK for ASE”.
-
La siguiente en criticidad (CVSS 8,2) es la primera de criticidad alta, y se trata de una nota relacionada con “Sensitive Data Exposure in SAP Web Dispatcher and Internet Communication Manager (ICM)”.
-
La siguiente en criticidad (CVSS 7,9) es la segunda de criticidad alta, y se trata de una nota relacionada con “Denial of service (DOS) in SAP NetWeaver (remote service for Xcelsius)”.
-
Las siguientes en criticidad (CVSS 7,5) se tratan de 2 notas de criticidad alta, y tienen que ver con “Denial of service (DOS) in SAP Business Objects” y “Memory Corruption vulnerability in SAP Web Dispatcher, Internet Communication Manager and SAP Content Server”.
-
La siguiente en criticidad (CVSS 7,1) se trata de la última nota de criticidad alta que analizaremos este mes, y tiene relación con “Missing Authorization Check in SAP S/4 HANA Private Cloud (Financials General Ledger)“.
-
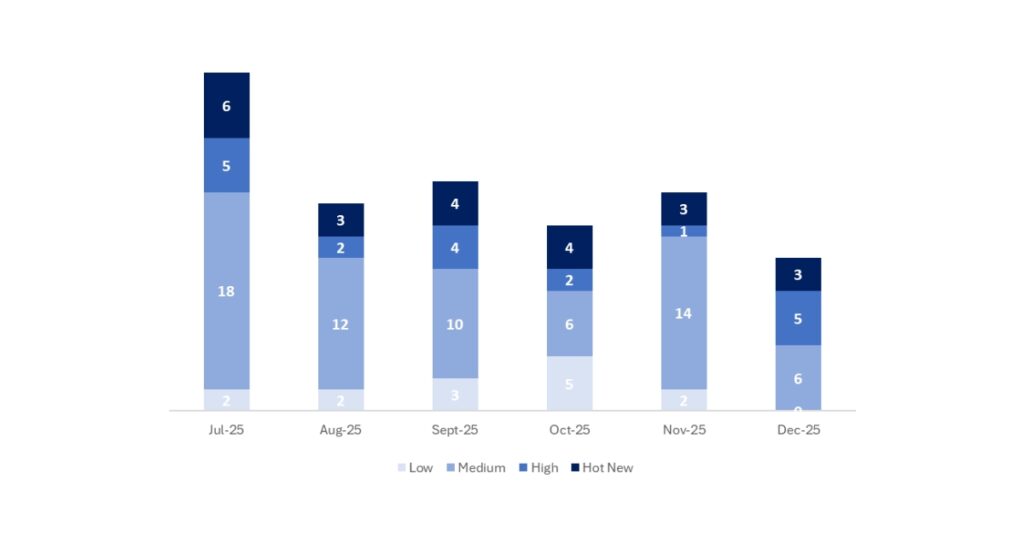
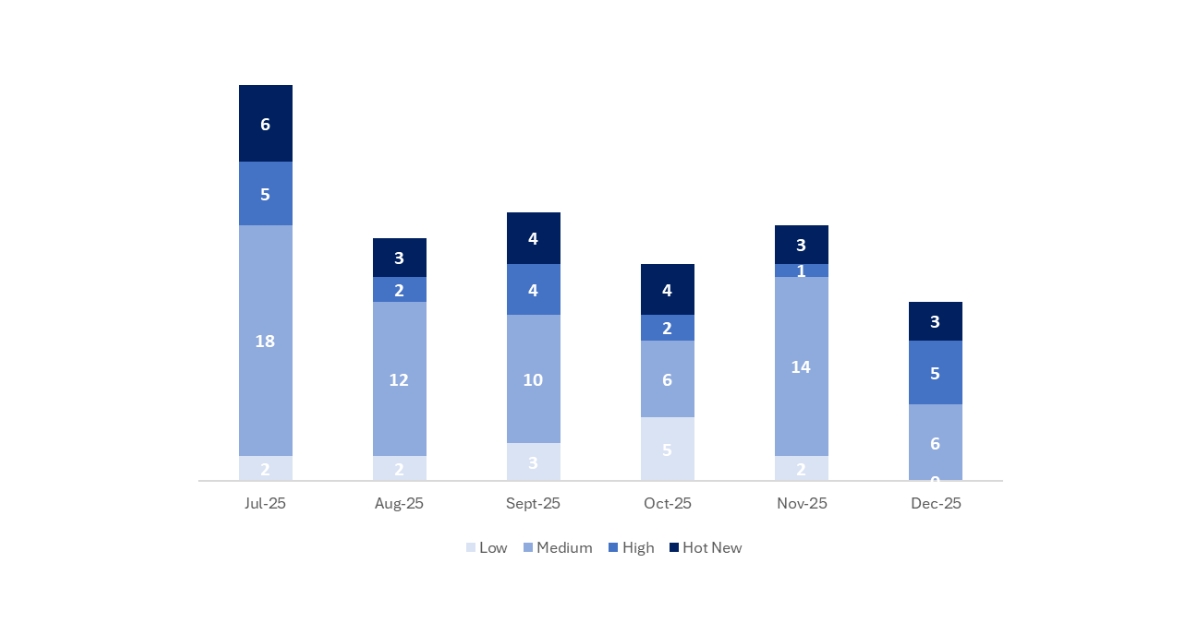
Este mes, pese a que han disminuido mucho el número de notas (de los meses con menor numero de notas del año), el 57% de ellas son de criticidad de 7 o más, por lo que tienen bastante relevancia.
-
Este mes el tipo más predominante ha sido “Denial of service (DOS)” (3/20 en el patch day)
En la gráfica podemos ver la clasificación de las notas de diciembre, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
Code Injection vulnerability in SAP Solution Manager (3685270): SAP Solution Manager is affected by a command injection vulnerability caused by missing input sanitization in a remote-enabled function module, allowing an authenticated attacker to inject malicious code and potentially gain full system control, resulting in high impact on confidentiality, integrity, and availability. The issue is resolved by introducing input sanitization that rejects most non-alphanumeric characters, and customers should apply the referenced Correction Instructions or Support Packages. No workaround is available. CVSS v3 Base Score 9,9/ 10 [CVE-2025-42880]
-
Multiple vulnerabilities in Apache Tomcat within SAP Commerce Cloud (3683579): SAP Commerce Cloud is exposed to two Apache Tomcat vulnerabilities—console manipulation via crafted URLs and relative path traversal — due to shipping with affected Tomcat versions. If the prerequisites described in the CVEs are met, an attacker could compromise confidentiality, integrity, and availability. SAP resolves the issue by upgrading Tomcat to secure versions included in Patch Release 2205.45, Update Release 2211.47, and Update Release 2211-jdk21.5. Customers must download the updated releases from the SAP Support Portal, rebuild, and redeploy their environments following the respective Public Cloud or On-Premise deployment guidelines. No workaround is available. CVSS v3 Base Score 9,6/ 10 [CVE-2025-55754]
-
Deserialization Vulnerability in SAP jConnect – SDK for ASE (3685286): SAP jConnect contains a deserialization vulnerability that, under specific conditions, allows a high-privileged user to achieve remote code execution by supplying specially crafted input. This results in a high impact on confidentiality, integrity, and availability. The issue stems from accepting unsupported or arbitrary user-controlled input without proper validation. SAP resolves the vulnerability by disabling serialization and deserialization of the affected input values within the jConnect JDBC driver and by restricting allowable values for the relevant connection property, thereby preventing RCE. Customers must upgrade to one of the corrected versions: SDK for SAP ASE 16.0 SP04 PL08 or SDK for SAP ASE 16.1 SP00 PL01 HF1. No workaround is available. CVSS v3 Base Score 9,1/ 10 [CVE-2025-42928]
-
Sensitive Data Exposure in SAP Web Dispatcher and Internet Communication Manager (ICM) (3684682): SAP Web Dispatcher and ICM may expose internal testing interfaces through the icm/HTTP/icm_test_<x> parameter, which is not intended for production use. If explicitly enabled, unauthenticated attackers could access internal diagnostics, send crafted requests, or disrupt services, resulting in high impact on confidentiality and availability and low impact on integrity. The vulnerability affects standalone Web Dispatcher installations, the Web Dispatcher in SAP HANA XSC/XSA, and ICM in SAP NetWeaver AS ABAP and Java. The fix requires manually removing all icm/HTTP/icm_test_<x> parameters from DEFAULT and instance profiles (e.g., icm/HTTP/icm_test_0, icm/HTTP/icm_test_1, etc.) and then restarting the Web Dispatcher or application server. No workaround is available beyond applying the prescribed manual correction. CVSS v3 Base Score 8,2/ 10 [CVE-2025-42878]
-
Denial of service (DOS) in SAP NetWeaver (remote service for Xcelsius) (3640185): SAP NetWeaver’s remote service for Xcelsius contains a vulnerability that allows an attacker with network access and high privileges to execute arbitrary code due to insufficient input validation and improper handling of remote method calls. No user interaction is required. Successful exploitation can cause service disruption or unauthorized system control, resulting in high impact on integrity and availability, with no confidentiality impact. The fix removes the Xcelsius remote service entirely. Customers must apply the relevant Support Package or BI Java patch for SAP NetWeaver BI 7.50, as detailed in SAP Note 3539090 and associated delivery notes. Xcelsius itself is end-of-life, and this security note formally discontinues its remote service. A temporary workaround is available through manual steps provided in the note, but SAP strongly recommends applying the official corrections since the workaround is not a permanent solution. CVSS v3 Base Score 7,9/ 10 [CVE-2025-42874]
-
Denial of service (DOS) in SAP Business Objects (3650226): SAP Business Objects is vulnerable to denial-of-service attacks due to improper request handling and insufficient resource management. An unauthenticated attacker can overload the service, causing long response delays or complete interruption, with no impact on confidentiality or integrity but a high impact on availability. The issue originates from third-party components that do not adequately restrict or manage incoming requests. The fix updates these components to secure, non-vulnerable versions that enforce stronger resource controls. Customers should apply the patches referenced in the “Support Packages & Patches” section of the security note and consult Knowledge Base Article 2144559 for the BI Platform maintenance strategy. CVSS v3 Base Score 7,5/ 10 [CVE-2025-48976]
-
Memory Corruption vulnerability in SAP Web Dispatcher, Internet Communication Manager and SAP Content Server (3677544): SAP Web Dispatcher, ICM, and SAP Content Server contain a memory corruption vulnerability caused by logical errors in internal memory handling. An unauthenticated attacker can exploit these flaws to trigger buffer overflows, heap corruption, and related issues, resulting in a high impact on system availability, though confidentiality and integrity remain unaffected. The issue affects ICM in SAP NetWeaver ABAP and Java, SAP Web Dispatcher in XSA versions below 1.4.0, and specific SAP Content Server releases listed in the note. The fix corrects the faulty memory logic and is delivered through updated kernel and component patches. Standalone and embedded Web Dispatchers, ICM, and Content Server must be patched using the appropriate kernel archives (SAPWEBDISP.SAR, dw.sar, SAPEXE.SAR, SAPEXEDB.SAR, SAPCS.SAR), following SAP’s kernel update guidance and relevant notes. XSA systems must be upgraded to version 1.4.0 or later. As a consistent rule, only the latest kernel or Content Server patch level should be applied. No workaround exists. CVSS v3 Base Score 7,5/ 10 [CVE-2025-42877]
-
Missing Authorization Check in SAP S/4 HANA Private Cloud (Financials General Ledger) (3672151): This vulnerability in SAP S/4HANA Private Cloud (Financials General Ledger) results from a programming error introduced in ECS logic, causing missing authorization checks. An authenticated attacker restricted to a single company code could improperly read sensitive data or create and modify documents across all company codes, posing a high confidentiality and low integrity impact, with no effect on availability. The fix enforces correct authorization validation, and customers should apply the referenced correction instructions or support packages to fully remediate the issue. A temporary workaround is available via functional SAP Note 3673002, but SAP strongly recommends implementing the permanent corrections as soon as possible. CVSS v3 Base Score 7,1/ 10 [CVE-2025-42876]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (diciembre):
SAP Security Patch Day – December 2025
SAP Patch Day: December 2025 – Onapsis
Recursos afectados
- SAP Solution Manager – ST 720
- SAP Commerce Cloud – HY_COM 2205, COM_CLOUD 2211, COM_CLOUD 2211-JDK21
- SAP jConnect – SDK for ASE – SYBASE_SOFTWARE_DEVELOPER_KIT 16.0.4, 16.1
- SAP Web Dispatcher and Internet Communication Manager (ICM) – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, 7.54, 7.77, 7.89, 7.93, 9.16, WEBDISP 7.22_EXT, 7.53, 7.54, XS_ADVANCED_RUNTIME 1.00, SAP_EXTENDED_APP_SERVICES 1, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 9.16
- SAP NetWeaver (remote service for Xcelsius) – BI-BASE-E 7.50, BI-BASE-B 7.50, BI-IBC 7.50, BI-BASE-S 7.50, BIWEBAPP 7.50
- SAP Business Objects – ENTERPRISE 430, 2025, 2027
- SAP Web Dispatcher, Internet Communication Manager and SAP Content Server – KRNL64UC 7.53, WEBDISP 7.53, 7.54, XS_ADVANCED_RUNTIME 1.00, SAP_EXTENDED_APP_SERVICES 1, CONTSERV 7.53, 7.54, KERNEL 7.53, 7.54
- SAP S/4 HANA Private Cloud (Financials General Ledger) – S4CORE 104, 105, 106, 107, 108, 109
- SAP NetWeaver Internet Communication Framework – SAP_BASIS 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756, 757, 758
- Application Server ABAP – KRNL64UC 7.53, KERNEL 7.53, 7.54, 7.77, 7.89, 7.93, 9.16, 9.17
- SAP NetWeaver Enterprise Portal – EP-RUNTIME 7.50
- SAPUI5 framework (Markdown-it component) – SAP_UI 755, 756, 757, 758
- SAP Enterprise Search for ABAP – SAP_BASIS 752, 753, 754, 755, 756, 757, 758, 816
- SAP BusinessObjects Business Intelligence Platform – ENTERPRISE 430, 2025, 2027